Please find our Frequently Asked Questions below. These are separated into the following categories:
General E-Waste Recycling Questions
Securis Specific FAQ’s
Degaussing FAQ’s
HIPAA Requirements and IT Recycling FAQ’s
If you are looking for information about our community recycling events or what is acceptable at those events, please visit our community recycling page.

General FAQ’s for IT Asset Disposition
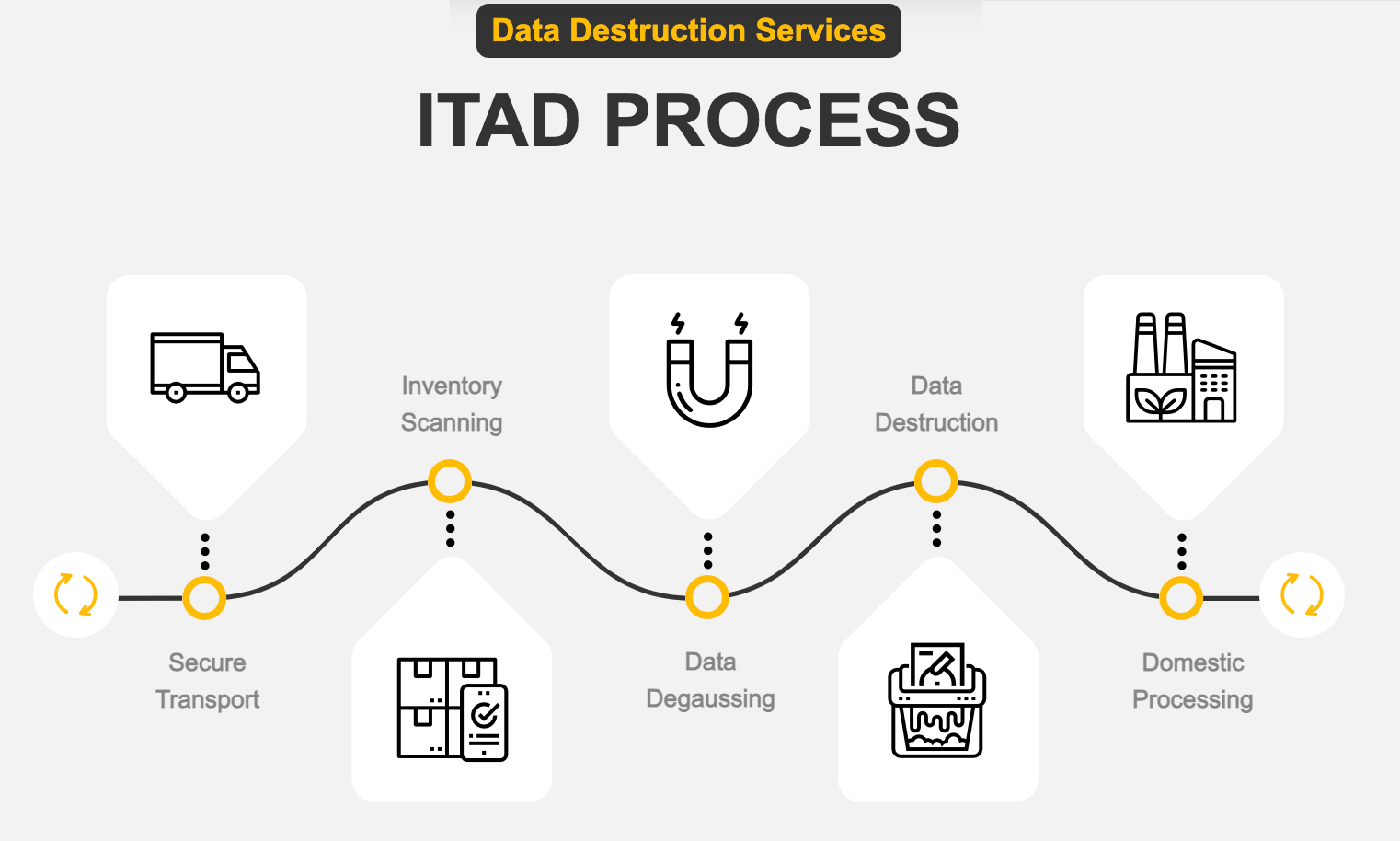
What is ITAD (IT Asset Disposition)
IT Asset Disposition (ITAD) describes the last phase of IT Asset Management in which IT Assets are securely and responsibly disposed of. The ITAD process provides compliant NAID AAA-certified data sanitization (data destruction) using various techniques, such as wiping hard drives to NIST 800-88 standards, degaussing, hard drive shredding, and media disintegration. This process can occur onsite via our mobile service, or assets can be picked up and sanitized at our secure facilities. After sanitization or destruction, IT Assets are recycled or resold while ensuring environmental compliance and data security.
Why is IT Asset Disposition important?
IT Asset Disposition (ITAD) is crucial for several reasons. First and foremost is data security. ITAD done right means any sensitive data is completely erased from retired devices. Sometimes, it calls for shredding or disintegrating data-bearing devices if they contain classified information. It is also essential for companies to comply with industry, Federal, and local E-waste compliance standards. Many companies also have internal standards for environmental governance. A company needs to choose an IT Asset Disposition company that can assure compliance, security, and the highest environmental standards to avoid potential breaches or non-compliance, which can result in extreme fines and reputational damage. In addition, IT asset disposition is cost-effective as companies can recover value from obsolete assets through resale, recycling, or donation.
How do you choose an IT asset disposition company?
When selecting an ITAD provider, consider the following:
- Certifications and compliance with industry standards
- Secure data destruction methods
- Environmental responsibility practices
- TransparencyTimliness and accuracy in reporting and
- Range of services offered (e.g., on-site data destruction, recycling, resale)
- Reputation and customer reviews
For more detailed advice on what to look for in a responsible E-Waste recycling partner, please read our blog post, and for our look at the top IT asset disposition companies, please click here.
What is NIST800-88 as it relates to data destruction?
NIST 800-88 is a guideline published by the National Institute of Standards and Technology that outlines best practices for media sanitization. The guidelines categorize data based on sensitivity, which helps determine the appropriate sanitization method. Highly sensitive information, such as classified or confidential data, requires more stringent sanitization than less sensitive data. The guidelines categorize media sanitization into three levels: Clear, Purge, and Destroy. Each level corresponds to different methods and levels of assurance in data sanitization. For a deeper dive into NIST 800-88 and the guidelines recommended for media sanitization, please read our blog NIST 800-88: Secure Data Destruction Standards for Media Sanitization.
What are the different data destruction methods?
Standard data destruction methods include:
- Software-based data wiping: This data destruction method employs software to purge a data-bearing device to NIST 800-88 standards. Wiping is the most sustainable option, as equipment can be safely reused or donated while ensuring data has been irretrievably destroyed.
- Degaussing is a powerful demagnetization process (for magnetic media) that is a proven method for removing data from magnetic storage hard drives and tapes.
Physical destruction (shredding or disintegration): This destruction process involves physically destroying data-bearing devices. The shredding method is chosen based on the physical size of the data-bearing device and the sensitivity level of the media on the device. The most sensitive information and the smallest devices, such as Solid-state drives (SSDs), flash drives, smartphones, SIM cards, memory cards, and micro SD cards, are usually shredded using a disintegrator capable of shredding these items to 2mm pulp.
What does data or media sanitization mean?
Media sanitization means permanently removing all data from a storage device to prevent unauthorized access. This can involve overwriting, degaussing, or physically destroying the media to ensure data cannot be recovered.
What are NSA data destruction standards?
The National Security Agency (NSA) has established stringent standards for data destruction to protect classified information. These standards typically involve physical destruction methods, such as disintegration, incineration, or pulverization, to ensure that sensitive and classified data cannot be recovered. The NSA issues a list of evaluated products that meet NSA specifications as well as an FAQ page that answers questions about media destruction. Securis employs several products from the evaluated products list.
How can you be sure that an IT Asset Destruction partner will not harm the environment with their e-waste recycling?
R2v3 certification is a reliable indicator that a vendor meets stringent electronics recycling and refurbishment requirements. This certification is not merely a management system but a comprehensive sustainability standard to achieve positive outcomes in electronic waste management. As an R2v3 Certified Facility, Securis undergoes independent audits to ensure compliance with the highest global electronics reuse and recycling standards. Please read our blog post to learn why you should choose an R2v3-certified e-waste recycling company for your ITAD needs.
What is a certificate of destruction?
A Certificate of Destruction (CoD) is more than just a document; it’s your assurance that your IT assets have been securely and permanently destroyed to NIST 800-88 standards, protecting your sensitive information from potential breaches. This vital certificate proves compliance with data protection regulations, helping your organization meet legal and industry standards while safeguarding your reputation. At Securis, we are committed to providing comprehensive and transparent documentation with every CoD, ensuring you have complete confidence in our meticulous processes. Our certificates detail the destruction of your assets, reinforcing your compliance and strengthening your security posture. They are available online in our Client Portal 24/7.
What is R2v3 Certification, and why should we partner with an R2v3-certified vendor?
The Responsible Recycling (R2v3) certification is a globally acknowledged electronics recycling and refurbishment standard. Developed by Sustainable Electronics Recycling International (SERI), the R2v3 standard mandates that certified facilities adhere to strict environmental, health, safety, and data security protocols. It is the most widely adopted sustainability standard for electronics recycling and refurbishment, applicable to facilities of all sizes and locations. R2v3 certification is a reliable indicator that a vendor meets stringent electronics recycling and refurbishment requirements and guarantees your companies electronic waste will not be illegally dumped. This certification is not merely a management system but a comprehensive sustainability standard designed to achieve positive outcomes in electronic waste management. As an R2v3 Certified Facility, we undergo independent audits to ensure compliance with the highest global electronics reuse and recycling standards. Please read our blog to learn why you should choose an R2v3-certified e-waste Recycling Company for your ITAD.
Is Data Center Decommissioning the same as ITAD?
Data center decommissioning is the process of closing down and dismantling a data center, which includes the removal of IT assets from the data center and the subsequent media sanitization, disposal, and recycling of those assets. ITAD is a broader term that is an acronym for IT Asset Disposition, which describes the last phase of the IT Asset Management cycle in which IT Assets are securely and responsibly disposed of. Data center decommissioning is more specialized and should be handled by companies experienced with the unique challenges and requirements of decommissioning large-scale data center environments which may include electrical and HVAC systems.
FAQ’s about IT Asset Disposition (ITAD) with Securis
How long have you been in business?
Securis has proudly been in business since 2020. You can learn more about our Company History here.
What methods do you use for destruction?
Our Standard data destruction methods include:
- Software-based data wiping employs software to purge a data-bearing device to NIST 800-88 standards. Wiping is the most sustainable option, as equipment can be safely reused or donated while ensuring data has been irretrievably destroyed.
- Degaussing is a powerful demagnetization process (for magnetic media) that is a proven method for removing data from magnetic storage hard drives and tapes.
- Physical destruction (shredding or disintegration) involves physically destroying data-bearing devices. The size of the shredded materials depends on the kind of device and the sensitivity of the media contained in the device. The most sensitive information and the smallest devices, such as Solid-state drives (SSDs), flash drives, smartphones, SIM cards, memory cards, and micro SD cards, will be shredded using a disintegrator capable of shredding these items to 2mm pulp.
- Smelting is an option but only sometimes used.
Can you provide a certificate of destruction?
Yes, Securis provides Certificates of Destruction (CoD) for all destroyed assets as evidence that your IT assets have been securely and permanently destroyed to NIST 800-88 standards. Our certificates detail the destruction of your assets and are available online in our Client Portal 24/7.
Do you capture serial numbers and provide an inventory report?
Yes, we capture serial numbers for all assets (if available) and provide detailed reporting. The average inventory accuracy rate in the ITAD industry is just 85% due to challenges such as damaged or missing asset tags, difficulty scanning large quantities of assets, and the appearance of multiple barcodes on electronic assets. At Securis, our thorough triple-checking process and use of AI uncover data-bearing devices that customers miss. Our inventory documentation reflects our commitment to accuracy throughout the ITAD process and promises a leak-proof chain of custody for every asset. After project completion, your inventory documentation will be available online via our Client Portal so that you will be audit-ready at any time.
Can you destroy to NSA standards? Is your equipment on the NSA's EPL?
Yes, Securis employs several products on the National Security Agency (NSA) evaluated products list. The (NSA) has established stringent standards for data destruction to protect classified information. These standards typically involve physical destruction methods, such as disintegration, incineration, or pulverization, to ensure that sensitive data cannot be recovered. The NSA issues a list of evaluated products that meet NSA specifications as well as an FAQ page that answers questions about media destruction.
Do you destroy to NIST 800-88 standards?
Yes, Securis always follows NIST 800-88 standards when deciding which data destruction methods would be most appropriate for a client. NIST 800-88 is a guideline published by the National Institute of Standards and Technology that outlines best practices for media sanitization. It provides recommendations for the most appropriate method for securely erasing data from various storage devices to prevent unauthorized access to sensitive information. The guidelines categorize data based on sensitivity, which helps determine the appropriate sanitization method. Highly sensitive information, such as classified or confidential data, requires more stringent sanitization than less sensitive data. The guidelines categorize media sanitization into three levels: Clear, Purge, and Destroy. Each level corresponds to different methods and levels of assurance in data sanitization. For a deeper dive into NIST 800-88, please read our blog NIST 800-88: Secure Data Destruction Standards for Media Sanitization.
Where are your facilities located, and what locations do you cover?
Securis uses NAID AAA-certified mobile trucks to extend service across the United States. Our physical locations are in Northern Virginia, Norfolk, Virginia, Central Carolina, Provo, UT and Richmond, Virginia.
What types of items do you shred, and what particle size can you shred down to?
Securis’ industrial shredding services are the foundation of our secure and certified data destruction processes. Our proprietary trucks allow us to safely destroy traditional hard drives (HDD) and smaller items such as Solid State Drives (SSD), flash drives, smartphone SIM and memory cards, and micro SD cards on-site at the customer’s location or securely in our access-controlled facilities. Depending on the destruction standards that need to be met, we can offer traditional shredding as well as a disintegration option that goes beyond traditional shredding and pulverizes devices into 2mm e-crumbs as recommended by the NSA, rendering all data completely irrecoverable. Certain hazardous materials, such as lithium-ion batteries, need to be removed before we shred phones and tablets. Some larger items may require our team to perform manual disassembly or cutting before they can be shredded in our mobile shredders. Items as large as a 1974 Volkswagen Bug can be shredded. For systems that are highly classified, the 2mm dust left over from NSA EPL disintegration could be incinerated if requested. Call our team to discuss your specific requirements.
Are you R2v3 Certified? What are your e-waste recycling practices?
Yes, Securis is R2v3 certified and dedicated to green recycling practices for each piece of equipment – whether intact, refurbished, or broken down for scrap to ensure harmful chemicals do not end up in landfills. Even our downstream vendors must follow strict standards to prevent environmental harm. Global stewardship and a commitment to serving others are at the core of Securis’ beliefs. As an electronic recycler, refurbisher, re-integrator, and data destruction firm, Securis’ mission is to provide environmentally sound solutions for the secure, effective management and removal of any organization’s end-of-life electronic assets while providing the most secure IT data destruction services in the industry. Securis’ commitment to improving the environment expresses our guiding principles and demonstrates our “think globally and act locally” sensibilities. Please read our blog to learn why you should choose an R2v3-certified e-waste Recycling Company for your ITAD.
Do you give any value back or pay for equipment?
There’s no need to completely write off the value of IT equipment in today’s environment. Along with secure data destruction, IT asset value recovery should be a consideration when decommissioning a data center or business environment. Securis technicians have over 20 years of experience identifying value in retired IT assets. This leads to a quick, efficient, and maximally profitable liquidation process, helping you maximize your assets’ residual value and offset the decommissioning process’s costs.
What services do you offer in your Mobile Trucks? Can you come to me and pick up the equipment?
Our specialized mobile truck is equipped with machines that allow us to provide quiet, speedy, and secure software-based wiping, degaussing, hard drive shredding, and Data Disintegration services wherever you are, allowing us to serve clients nationally. Performing on-site electronic media shredding at the client’s location enables their personnel to witness the process, thus maintaining the highest level of security. Our mobile trucks are NAID AAA Certified, so you can be sure that your ITAD projects will meet the strict information disposal standards established by the National Association of Information Destruction (NAID).
Do you provide locked totes?
Yes, we do. If you do not have enough equipment to warrant a site visit or need a secure place to keep equipment until your service window arrives, Securis has a variety of Pelican Storm Cases that our clients can use to store or securely send equipment to Securis. These cases are military tough and designed to be safe and secure in the harshest conditions. Classified information can be transported via storm cases from USPS or courier as long as protocols are followed. In this video, our Director of Operations, Sal Salvetti, explains how Securis clients use Pelican storm cases.
What can you tell me about your company's security? What are your credentials? Are you AAA NAID certified?
Securis is NAID AAA certified for mobile operations and at our main facility in Northern Virginia. An NAID AAA certification provides several important assurances about an ITAD (IT Asset Disposition) vendor. NAID AAA-certified vendors must adhere to rigorous standards for secure data destruction, following strict protocols and employing robust security measures to safeguard confidential information during the entire ITAD process, including safe transportation, controlled facility access, and secure destruction methods. NAID AAA certification involves comprehensive auditing and compliance verification, as vendors must undergo scheduled and unannounced audits by trained, accredited security professionals to verify compliance with data protection laws and NAID standards. The certification process includes rigorous audits in 20 operational and security requirements areas. NAID auditors verify employee screening processes, validate employment and training records, and randomly test employees’ knowledge of data erasure policies. Auditors verify quality control logs and inspect security systems like CCTV and alarm logs. Vendors must have appropriate written policies and procedures in place for all aspects of data destruction. NAID AAA certification signals that the vendor will keep sensitive information secure until it is properly destroyed, helping protect against data breaches.
What is the average turnaround time to receive inventory reports and Certificates of Destruction? Is there a Client Portal to access this information?
Securis posts inventory reports and certificates of destruction on average 72 hours of project completion. These reports and certificates are available to our clients 24/7 via our Client Portal.
What are your chain of custody procedures? What happens to my equipment once it leaves my facility/office?
Secure On-Site services begin at the client location. Securis‘ professionally trained and certified staff members scan, tag, and inventory all electronics slated for destruction or recycling to establish a chain of custody. Once inventory is complete, media sanitization begins. This often takes place onsite at our clients’ offices but can also occur at the Securis facilities, depending on the particulars of the agreement. Securis performs wiping, degaussing, shredding, and disintegration services during sanitization using our NSA-approved equipment. Sanitized equipment is then loaded onto a Securis GPS-traceable truck and securely transported to one of Securis’ processing facilities, where a client-approved recycling plan is executed. Inventory lists are updated with records of all processed items for audit and accountability purposes. At the end of the process, a complete inventory list is provided to the client, as well as a Certificate of Destruction, a nationally recognized legal document of performance.
What separates you from other vendors?
Securis has been an IT Asset disposition (ITAD) leader for over 24 years. Over that time, we have worked with some of the country’s largest data centers, healthcare facilities, government contractors and agencies, and financial institutions.
Secure: Our vast experience with large IT Asset Disposition (ITAD) projects has helped us streamline the ITAD process to ensure we are using the most secure data destruction methods for your hard drive destruction and IT asset disposal needs. Our numerous certifications, including NAID AAA, ensure strict compliance with all Federal, state, and local data destruction standards.
Accurate: The average inventory accuracy rate in the ITAD industry is just 85%. At Securis, we achieve greater than 99% accuracy in our ITAD processes. Our thorough triple-checking process uncovers data-bearing devices that customers miss. Our inventory documentation reflects our commitment to accuracy throughout the ITAD process and promises a leak-proof chain of custody for every asset. Learn more about Why Inventory Matters in Electronics Recycling and Data Destruction Policy.
Sustainable: We are R2v3 certified and dedicated to green recycling practices for each piece of equipment – whether intact, refurbished, or broken down for scrap. Even our downstream vendors must follow strict standards to prevent environmental harm. To learn why you should choose an R2v3-certified e-waste Recycling Company for your ITAD, please read our blog on that subject.
Are your facilities and employees cleared to handle classified data?
Our North Virginia facility and mobile operations are NAID AAA-certified, ensuring that security protocols are strictly followed. Securis has experience destroying CUI, Secret, Top Secret, and even SAP classified data. While all employees are background checked and drug tested, please call to discuss your specific requirements.
Do you track your truck with GPS?
Yes, our trucks are GPS-monitored and driven by screened employees, including through background checks, fingerprinting, and drug testing.
Can you pull the hard drives from the devices, or do we need to do that?
The most environmentally friendly way to recycle computers is to sanitize the data using a NIST 800-88 purge. To purge the data, customers should leave the drives in the computer. If a customer requires the drives to be shredded, the customer can remove them, or Securis technicians can remove them. We charge an additional fee to remove drives from computers or caddies.
Can you de-rack servers, or do we need to do that?
We require that servers and network equipment be powered off and can remove servers from racks for an additional fee.
Do you recycle batteries?
We can recycle Lithium Ion batteries and uninterruptable power supplies (UPS).
How fast can you come and pick up our equipment for disposal?
Our schedule is usually booked out two or more weeks in advance. While it is best to contact us 3-4 weeks ahead of time, we may be able to schedule sooner if you are flexible on the date and time.
What is your process for routers & switches?
Networking gear will be returned to factory settings unless the customer requests the data-bearing devices be shredded. Our best practice is to destroy data-bearing devices in firewalls. If we can not return switches to the factory setting for any reason, we destroy data-bearing devices before recycling them as a requirement of our certifications. Clients are welcome to witness the entire process if they wish.
Can you match hard drives to servers?
Yes. Some customers request that we match drive serial numbers to servers before shredding and we can do this for an additional charge. Our photo AI scanning service significantly increases the accuracy of hard drive scanning. Learn more about our AI scanning technology in this video.
Can you come to do an audit (inventory count) and create an asset list?
If you don’t have a complete inventory, one of our account representatives may be able to visit your site before scheduling your job. If that is not possible, pictures can help estimate quantities. Securis will do its best to assist you with estimating your inventory and charge for the number of recycled items.
Do the economics of electronic recycling work?
Unlike single-use plastics, electronics can be recycled in an environmentally friendly way without breaking the bank. This is because some equipment can be re-sold after proper data sanitization, which offsets some of the high labor and machinery costs associated with older equipment that is disassembled and scrapped.
Do you shred paper?
We don’t shred paper, only hard drives and electronics. We have referred companies to www.trueshred.com and received positive feedback.
Is Securis a minority-owned company?
Securis is not a minority-owned company, but we partner with various companies, including 8(a) minority-certified and SDVOSB Service Disabled Veteran Owned Small Businesses. Securis has a program that employs people with intellectual disabilities, which many companies report on as part of supplier diversity, ESG, and DEIB initiatives.
General E-Waste Recycling FAQ's
Why Recycle Computers and Electronics with Securis?
The electronics we use for business and play contain materials such as antimony, arsenic, lead, and mercury that are unhealthy to us and to our environment. It is surprisingly easy for these materials to ultimately end up in our bodies and cause major issues including lung damage, cancer, and seizures.
Just one color monitor alone contains 6 ½ pounds of lead and measurable amounts of cadmium, mercury, and other toxic metals.
At Securis, every part of the electronic asset is recycled in our e-waste recycling programs. Each item is strategically and securely dismantled. All toxic elements are responsibly disposed of, and all remaining metals, plastics, glass, and circuitry are processed domestically. It’s a commitment we make to keep everyone and every land healthy during computer disposal and recycling.

What Items are Considered Electronics for E-Waste Recycling?
We define and perform electronics recycling for materials listed under the Resource Conservation and Recovery Act (RCRA) issued by the Environmental Protection Agency (EPA) These include:
- Televisions
- Monitors
- Computers
- Printers
- Computer peripherals
- Audio and stereo equipment
- VCRs
- DVD players
- Video cameras
- Telephones
- Facsimiles
- Copying machines
- Cellular phones
- Wireless devices
- Solar Panels
Why Prevent Electronics From Entering a Landfill?
Some electronic device components contain constituents that, if improperly handled, could be harmful to the environment and its inhabitants. E-waste that is not recycled ends up in the environment. Water is poisoned, the air turns toxic, the soil becomes dead, and wildlife and plant life suffer, which is part of why e-waste recycling is so important.
Certain components of electronics contain measurable amounts of regulated heavy metals, including lead, silver, barium, cadmium, and mercury. Many of these metals can be recovered and responsibly disposed of, based upon EPA standards.
How Will Recycling My Obsolete Computer and/or Electronic Equipment Make a Difference?
It is estimated that of the approximately 250,000,000 tons of solid waste generated annually in the United States, around 5% is classified as e-waste.2 Of this, only an estimated 10% to 18% of electronics are recycled, according to WellHome.3
Securis wants to help change this for the good of our local and global environments through our e-waste recycling commitment.
What are the Outcomes if We Dispose of Electronics Improperly?
A NOTICE OF VIOLATION can be issued by the Resource Conservation and Recovery Act.
Failure to correct the alleged violations cited required by this NOTICE may result in the assessment of penalties, not to exceed $27,500 per violation pursuant to Section 3008 of Resource Conservation and Recovery Act (RCRA) of 1976, 42 U.S.C. § 6928.
What About Donating My Electronic Assets?
Donation programs can work well if all involved parties understand the limits and liabilities associated with the transfer of equipment. Questions such as, “Who will ensure that proprietary data is eliminated before the donation?”? need to be answered prior to ownership transfer.
The Gramm-Leach-Bliley Act of 1993, Health Insurance Portability and Accountability Act (HIPAA), and many other state and federal laws make all companies and organizational entities legally responsible for the protection of client privacy. Failure to effectively destroy all informational data prior to the transfer of ownership leaves an organization open to corporate liability.
Securis’ Data Destruction process helps eliminate the worry of such a risk.
Why Does it Cost Money to Recycle Some Electronics?
While we do our best to be sure each customer receives the maximum value from each repurposed and scrapped piece of IT equipment, there are certain items that cost us to properly dispose of, such as some televisions and monitors (see a full list of acceptable items and fees here).
Materials such as antimony, arsenic, lead, and mercury used to manufacture electronics are unhealthy to us. If not recycled properly, it is surprisingly easy for these materials to ultimately end up in our bodies and cause major issues including lung damage, cancer, and seizures. E-waste that is not recycled ends up in the environment. Water is poisoned, the air turns toxic, the soil becomes dead, and wildlife and plant life suffer.
To avoid these harmful effects on both our bodies and our environment, reputable e-waste recycling companies provide outlets for responsible riddance of your old electronics. Unfortunately, some e-waste recycling companies lower their costs by exporting old electronics to countries like Ghana, Nigeria, Pakistan, India, and China where it gets broken down by men, women, and children who are usually unprotected from the toxins.
Securis just doesn’t believe that is how the w-waste recycling process should be handled. We focus on proper disposal and e-waste recycling that’s safe and doesn’t put the less-fortunate at risk.
Read more from the sources we’ve used:
FAQ's About Degaussing
What is a Degausser?
Essentially, a degausser is a machine that changes the magnetic domain of magnetic data storage devices where the data is stored. Examples of magnetic storage would be media like backup LTO and DLT tapes, VHS tapes, cassettes, reel-to-reel tapes and hard drives. Compact Discs (CDs) are not considered magnetic storage because the data is stored on the disc with optics. When the degausser is applied to magnetic domains the information is scrambled into random patterns. This process renders the data that was stored in these magnetic domains unreadable.
Some generic magnetic storage devices can be reused after the degaussing process has taken place. Reel-to-reel tape and VHS video cassettes and older media types are examples of these kinds of devices. However these items are so old that saving them or reusing them is generally not a common practice because of the very limited storage capabilities.
For other forms of newer data storage like server hard drives and some backup tapes, degaussing renders the media completely unusable because of permanent damage to the storage system. This happens because of damage to the special servo control data that is written onto the media at the factory by the manufacturer. Once the servo track is damaged, it cannot be corrected. Degaussing removes not only the stored data on the device but also removes the servo control data, and without the servo data the device is no longer able to determine where data is to be read from or written to on the magnetic media.
Why is Degaussing Necessary?
Physical destruction of a data storage device alone technically does not remove the data. It just makes the device (tape or hard drive) unusable and the data unreasonable to retrieve.
This means that even though the item has passed through a shredder, it still has data on the little pieces that can be recovered. Many recycling and shredding firms claim that after shredding the data is not recoverable. This is a possibility, albeit unlikely, depending on where the shredded hard drive was sent.
After shredding a hard drive, most computer experts would not be able to retrieve data from the shredded pieces. However, there are some people/places/countries that would indeed be able to retrieve the information. How is this possible? If you take a magnet and smash it on the ground, the magnet will break into small pieces, but each of these pieces is still magnetic. Hard drives work the same way. Because the hard drives or tapes store the data using magnetics, even a small piece of the device retains its magnetic properties, and therefore can still be read.
When is Degaussing Required?
Most of the time, degaussing is the only way to satisfy a federal requirement related to the sanitization and destruction of clearance-level information like “Classified” or “Top Secret.” In an attempt to protect the country’s classified information, several different federal agencies have standards and procedures that have been written on how to handle the destruction of sensitive data. Those standards involve the use of a degausser followed by physical destruction of the unit.
How is Your Service Licensed? What is the Cost Model?
Our services are customized based on each client’s quantity, frequency, and desired level of security.
Do You Provide this Service On-site or at Your Site?
The degausser is internally mounted and powered by our 26’ box truck so that the service can be provided at your site. However, we also have the capability to degauss the drives off-site at our secure, NAID-certified facility. This is typically done once or twice a week. For maximum data security assurance, we recommend on-site degaussing followed by on-site shredding.
Doesn’t the Degausser Need Periodic Calibration?
Yes, monitoring of the magnetic fields is done via a program we use called FieldCheckR. Our degausser is verified before every degaussing process to ensure that it is properly functioning. Not all degaussers have the ability to be tested using our digital read-out system with the FieldCheckR program.
Can You Degauss Solid State Drives?
Solid State Drives (SSDs) do not store data magnetically, so they cannot be degaussed. Please visit this blog post to learn more about the best practice for destroying information stored on solid-state drives.
Is There a “Degaussing” Equivalent or “Absolute Best Practice” of Data Destruction for Solid State Drives?
Yes, secure data shredding with a controlled, smaller shred width and particle size is the most secure method for solid-state drives. View more information on our blog by clicking this link.
If Degaussing is the Best Way to Destroy Data, Why Would I Shred My Hard Drives Too?
Shredding is an added redundancy to ensure the absolute destruction of data. Due to the fact that a degaussed drive and a non-degaussed drive physically do not look different, it is a best practice to shred drives after they are degaussed.
What Types of Companies Should Use Degaussing?
Organizations with zero tolerance for any leaks who want to be totally risk-free and can rationalize the cost. Typically data that is sensitive or proprietary, such as mission-critical data, financial information, private health records, or personal identifying information, should be considered for degaussing. Most organizations today consume some type of sensitive data, whether its employee bank account information, social security numbers, or even HR records.
FAQ's about HIPAA Requirements and IT Recycling
What is the HIPAA Privacy Rule?
The HIPAA Privacy Rule restricts the use and disclosure of an individual’s protected health information (PHI). Healthcare organizations and medical facilities (referred to as “the covered entity,” or CE) and any vendors or business associates of that CE are responsible for adhering to the HIPAA HITECH requirements.
What does the HIPAA Privacy Rule require regarding the disposal of E-PHI (electronic protected health information)?
HIPAA requires policies and procedures that address the disposition of protected health information (PHI) and the hardware that it’s stored on. All PHI must be removed from media before items are made available for re-use. See 45 CFR 164.310(d)(2)(i) and (ii).
HIPAA does not specify a disposal method. Data must be destroyed by clearing (data completely overwritten), purging (degaussing), or destroying through shredding, incinerating, etc.).
Are healthcare organizations and medical facilities required to keep patient medical records for a specific amount of time?
No. Individual state laws dictate how long patient medical records must be retained. HIPAA does require safeguards are in place to protect the privacy of protected health information (PHI) for the amount of time that the information is maintained. See 45 CFR 164.530(c).
What devices are at risk in hospitals, medical facilities, and healthcare organizations?
It is estimated that of the approximately 250,000,000 tons of solid waste generated annually in the United States, around 5% is classified as e-waste.2 Of this, only an estimated 10% to 18% of electronics are recycled, according to WellHome.3
Securis wants to help change this for the good of our local and global environments through our e-waste recycling commitment.
- X-ray machines, both preventing usage and hacking into the system to generate image backups on a hacker’s network
- Pacemakers and other devices inside people
- Computers used to create electronic medical records (EMRs)
- Servers that store E-PHI, EMRs, and payment information
- Defibrillators (including those implanted in people) that are Bluetooth enabled
- Temperature settings for connected coolers and refrigerators that contain blood, organs, medicine, and other elements — hacking piggybacks controls used to monitor temperature and make adjustments if the device becomes too hot or cold
- CT scan machines, where radiation exposure limits could be adjusted
- MRI and other machines that rely on operators located in separate rooms or facilities for controls, settings, results recordings, and maintenance.
The list of hackable devices even includes those in-room screens and devices designed specifically to track who you are and what your medical needs are. A simple hack can reset these back to square one, or create changes in your chart that would cause the wrong medicine to be administered.
Essentially, almost any connected device in your local hospital, medical facility, and healthcare organization is vulnerable.
Are healthcare organizations and medical facilities able to reuse computers and other media that store E-PHI?
Yes, once steps have been taken to remove the protected health information from the media prior to reuse. See 45 CFR 164.310(d)(2)(i) and (ii).
How can healthcare facilities and hospitals protect against risk?
The FDA has taken some steps to limit risks. Part of the FDA’s work includes guidelines to ensure devices are patchable when a vulnerability is found.
The FDA also notes that devices can be updated with cybersecurity information and protections without having to go through recertification, making devices easier to secure for manufacturers and hospitals.
Just like in recent ransomware attacks, another way to minimize risks is to always update systems as soon as an update is available. Hundreds of thousands, if not millions, of dollars could be protected each year in the U.S. alone if system administrators at hospitals, corporations, and small businesses would apply patches as soon as they were made available.

Can a business such as Securis be hired to dispose of protected health information?
Yes. Healthcare organizations and medical facilities are allowed to hire third-party vendors to dispose of protected health information. There must be an agreement or contract that requires the vendor to safeguard the PHI through disposal. See 45 CFR 164.308(b), 164.314(a), 164.502(e), and 164.504(e).
What, exactly, can Securis do to protect patient records, billing information, and other risks left on computers and other medical equipment?
At Securis, we focus on protecting patient information, passwords, and other sensitive data left in older devices.
Simply throwing out an old laptop, PC, copier, smartphone, or hard drives can put organizations at significant risk because you can’t be sure that data lurking on these devices has been cleansed.
We tout the thorough shredding and destruction of these devices because it is a simple and effective way to prevent information from getting into the wrong hands. And, in the cases of healthcare facilities and hospitals, it helps you adhere to local and federal regulatory requirements protecting patient information and E-PHI.
It’s how we do our part, and we welcome a conversation with you about how you can do your part to protect your organization, customers, and even the environment.
Source: https://www.hhs.gov/hipaa/for-professionals/faq/disposal-of-protected-health-information
SECURIS FACILITY SECURITY