Sustainability Meets National Security-Interview Transcript
Attendees
Kurt Greening, EVP Securis
Richard “Dick” C. Schaeffer, Jr
Mr. Schaeffer is a former Senior Executive with the National Security Agency (NSA), with almost 50 years in the Information Security, Cyber Security, and Intelligence space. Since retiring in 2010, Mr. Schaeffer has continued to pursue his passion for improving the security of U.S. and partner interests in the Cyber domain. He started a private consulting firm, Riverbank Associates, LLC, located in Severna Park, Maryland, bringing visionary leadership, management, technical experience and expertise to his client’s challenges. His client base has included a full range of private sector companies from small start-ups, middle market companies, large system integrators, commercial businesses, and international entities. He also leads the Paladin Strategic Advisory Group and is a Principal in Endeavor Technology Group.
Bill Downer
Bill is a Managing Director at Rare Element Solutions, a company that was formed to solve supply chain challenges for the U.S. Department of Defense. Before starting Rare Earth Element Solutions Bill was vice president of national programs at Seagate Government Solutions, a provider of data management solutions to federal agencies. Downer previously held several sales-related directorial roles in companies such as Sun Microsystems, DEC, StorageTek, Quantum, Mellanox Technologies and DataDirect Networks. Downer earned a master’s degree in business administration from Averett University and a bachelor’s degree in religious studies from Randolph-Macon College.
Transcript
Kurt Greening: Welcome Dick and Bill. For anyone who doesn’t know, my name is Kurt Greening and I am an executive VP with Securis. We’re an industry leader in drive shredding and IT asset disposal. And today we’re here to talk about two important issues, sustainability and national security. For those of you who may or may not know Bill and Dick, I’ll just read a quick bio, and if I miss anything, maybe the two of you can help me a little bit.
Kurt Greening: But Dick Schaefer actually is a former executive with the National Security Agency, NSA, and he spent almost 50 years in the information security cyber security, and, intelligence., and he’s still pretty active these days, doing things like working for Riverbank Associates, working for Paladin.
Kurt Greening: in terms of investing in some up-and-coming technologies. and he’s also a principal in Endeavor Technology. Did I miss anything Dick you want me to point out?
Richard Schaeffer: No, that’s it.
Richard Schaeffer: I’m an old guy who’s been seen a lot.
Kurt Greening: Awesome. That’s great. And Bill, it’s great to have you on as well. I’m excited to introduce people to Rare Element Solutions which is a company that recently has been created to solve supply chain issues for the US Department of Defense.
Bill Downer: Yeah. Thanks, Kurt.
Kurt Greening: And I know you’ve been around also for a while working for people like Seagate, Sun, DAX, Storage Tech, Quantum if there’s an expert out there in the data storage industry, I think your resume kind of screams that. So I’m really excited to have you on and introduce people to what Rare Element is doing. So, maybe if I could start with you, to help our audience, can you explain to people how supply chain became a national security issue or became an issue that maybe more people are now aware of today?
Richard Schaeffer: Yeah, I think it’s more the latter. Supply chain has always been a national security issue. whether that is in the aerospace and defense, whether that’s in intelligence, whether anytime the US government has built something to execute or conduct a mission, the things that go into the technology that supports those missions has always been critical. we haven’t always thought about it in the context of supply chain. We would design things, we would order material, we would build things, we would test them, we would deploy them. and eventually they’d reach end of life and they’d probably end up in a warehouse somewhere or I started out life in the Marine Corps. we were the folks that got everything after the other services were done using them.
Richard Schaeffer: So we learned how to do a lot with very little. But over the last 10 years the concept of understanding protecting the supply chain has become more and more important. And then I think during the COVID era when all of a sudden the containers sat on ships in harbors on the west coast or on the east coast and components couldn’t be brought ashore because of the shortage of personnel or the inability to move the material off the docks and so forth.
Richard Schaeffer: people became more aware of just what it meant when you couldn’t order get material, build things, deliver things, and so forth. and there’s always been an issue with at end of life, how do you ultimately take something that has been a critical mission component? I’ll say all my years at NSA we worried about national security systems. of those systems that procified that process classified information or were part of weapon systems and you worry how do you destroy devices that are part of that ecosystem such that if an adversary was to obtain those devices they couldn’t extract anything from them that was useful.
00:05:00
Richard Schaeffer: and NSA was responsible for setting the standards for how that was done. the discipline to do that I’m not always sure was at the highest level that it needed to be because I think IG’s and others would find warehouses where there was equipment stored that probably should have been destroyed years ago or things were done just out of expediency the people who were actually doing it weren’t even aware of the requirements for how things should be processed.
Richard Schaeffer: But I think we’re in a time now in a phase when supply chain’s important and it’s important to think about supply chain from whether it’s mining or that that creates the aluminum, titanium, other metals from which gearboxes or other kinds of devices that go into aerospace and defense components or whether it’s the sand that forms the silicon devices from which micro electronic devices are produced and then ultimately at the end how those things are recovered. I think it’s a much much bigger issue today but it’s not new.
Richard Schaeffer: It’s the attention we’re bringing to the capabilities that we can bring to that environment and then ultimately how do we ensure that we’re maximizing the value chain that’s part of this whole process as well.
Richard Schaeffer: So probably more than you wanted on just the national security aspects of it but it’s an extraordinarily complex topic. not well understood by a lot of people who are outside of the immediate area impacted by supply chains.
Kurt Greening:. Perfect. Yeah, thanks for that. Bill when I talk to a lot of people about sustainability, they’re thinking about Earth Day recycling cans, can I buy an electric car? But maybe an area that they might be less familiar with is electronics. How does electronics play a role in sustainability?
Richard Schaeffer: Well I’ll start and then maybe kick it over to Bill. As I pointed out earlier, NSA is responsible for the destruction piece. So, there are materials that we’re able mine in partner, countries that become the feed stock, if you will, for the microelectronic devices. we used to produce a lot of them here. actually NSA used to have its own foundry. we used to build our own chips.
Richard Schaeffer: NSA doesn’t do that anymore. there are a few microelectronic fabrication facilities here in the US. Maybe there will be more in with thrust of the current administration, but a lot of that comes from offshore. and so the devices are fabricated, they’re manufactured, they’re delivered, and then they’re put into systems here. And it used to be that when we destroyed something like a solid-state drive or a hard drive or something like that, we crush it up and then take it to a landfill. it became part of the terrain.
Richard Schaeffer: and that was done because we didn’t have the ability to recover the devices, even the precious metals in a lot of cases. you look at a printer wiring board today, there’s silver there, there’s gold there, and a lot of cases, we just crush it up and it goes to the landfill. and you say now are there ways in which we can actually at a reasonable price point recover some of that material so that we can feed it back to the front end of that big supply chain loop.
Kurt Greening: Yeah, maybe we’ll talk about the economics at the end. Bill, any thoughts or things you want to add to that?
00:10:00
Bill Downer: No, and I agree with Dick and his opening remarks that there was a lot of focus coming to this prior to COVID and the pandemic and where a lot of our materials for what the US government uses and the banks and everyone else were coming from China. But to Dick’s point, the pandemic really put a microscope on so much when we could no longer get it into the country.
Bill Downer: we really became very evident of where the products or the sub-asssemblies or materials are coming from and as a result created rightfully so an alarm around where are these things coming from and how much at risk was the US because it didn’t really understand all the dynamics of the supply chain and now it has really become very much a focus
Bill Downer: which I think is great. sorry it had to be a pandemic that brought us to this point but for good outcome as a result
Kurt Greening: To the good outcomes, what are some of the things, strategies or programs that the US government is employing to solve some of these issues?
Kurt Greening: I don’t know, Dick, you want to take that one?
Richard Schaeffer: Yeah. Let me start. And again, I’ll let let Bill chime in here as well. I think it’s okay. The US government now recognizes that there’s an issue. the problem is and we do with so many big challenges in the federal government, there’s a lot of people who are involved. And whenever there’s a lot of people involved, it usually ends up where no one’s in charge. So if you think of supply chain security today, everybody’s got a little piece of it. Everybody in the federal government. So you’ve got the Department of Defense, yeah, they’ve got a big role. You’ve got Department of Homeland Security, they’ve got a role. Department of Commerce has a role. and in defense, if you look down amongst all the defense departments and agencies, everybody’s got a little role. And there there really isn’t, there are there are policies, there are regulations, there are best practices, but there really isn’t a US government champion who is what I would call the great advocate for both the materials and the processes and who can set priorities.
Richard Schaeffer: So if if we need I’ll do something simple like if we need aluminum for manufacturing of aerospace and defense systems that can be air breathers, it can be satellites, it can be remotely piloted vehicles, unmanned aerial systems, drones, it can be a whole series of things. and there’s probably 20 different kinds of aluminum. if you go to the mines and you say, “Okay, I think it’s oxite that you create aluminum Okay, here, here’s a mine, we mine the ore, we process it somewhere. We create the alloys of aluminum by adding stuff to them and then they go off to be satellite components or airframe components whatever they do. Oh and some of this stuff has to be of a form where it can be machined, where it can be and so the manufacturer, the supply chain for that from the mining all the way through to the delivery of the components is there’s probably 10 or 15 departments and agencies that are involved in that whole process. The health and human services from an OSHA standpoint, what can people do? what can’t they do?
Richard Schaeffer: but there’s nobody who’s sort of sitting at the top saying aluminum is a critical component to aerospace and defense and we need to ensure that we’ve got input into that supply chain into the beginnings of manufacturing the creation of the material and then in the end how do we recycle that stuff? Okay, we’ve got an F-15 that’s longer serviceable. we were flying A4s when I was in Vietnam and when they got shot up, we took them out in South China Sea and a big CH53 would carry them out there and dump them in the ocean or dump them in the sea and they’re probably disintegrated by now. That wasn’t very effective.
00:15:00
Richard Schaeffer: But it’s kind of a government mindset if there’s nobody saying here’s the priorities, here’s the processes, here’s what we need to do in order to be able to create, here’s what we need to be able to do to at end of life to recover, and here’s how all the agencies will play together in order to make that all happen. We just don’t have that today.
Kurt Greening: Yeah, great great background.
Kurt Greening: So, you gave us some examples of, planes and weapon systems and aluminum. Bill, you’re kind of our resident expert here on the interview on data storage. Tell me about What do hard drives have in inside of them that make them so valuable to the DoD?
Bill Downer: So to Dick’s point, a lot of the connectors use precious metals. in fact, the platters have been different materials over time, whether they were aluminum or glass. and all of that is recyclable, well both of those particular things are very recyclable, but at the end of the day data storage is about zeros and ones and historically how we’ve created the data on any storage device. The zeros and ones has to do with magnetism and using magnets. And as we get more and more sophisticated, as we shrink these things down, you made more and more sophisticated magnets, which has led us to building the magnets out of rare earth metals. because everything Dick said earlier about the difficulty in mining those ores, the difficulty in processing them, they have become more and more valuable. And that’s why responsible retirement and reclamation becomes such an imperative because those materials are so hard to
Kurt Greening: Thanks for that. Dick, you kind of answered this question that, telling us there’s at least 15 different agencies in the federal government helping with this problem. I have some knowledge that DOE is also helping with some research grants and in this area. Is there anything that stands out there in terms of work that’s exciting?
Richard Schaeffer: I’m probably not as sort of current on Yeah,…
Kurt Greening: And that’s an area outside of your experience.
Kurt Greening: I mean, I know that they’re one of the 15. yeah, right.
Richard Schaeffer: I would just say, from a DOE perspective I mean, the US government has long used the DOE labs as I’ll say think tanks, and basic research components to explore of doing kind of a simple term ways of doing things.
Kurt Greening: Yeah. Yeah.
Richard Schaeffer: Anytime we had a hard problem, whether it was nuclear fusion or fission or whether it is possibly recovery of material, we’ve used the national labs as think tanks within the government classified environments in many cases to explore solutions to big hard problems and so the ability to create those solutions is interesting, but it’s not very helpful if you can’t get them out and then make them commercially viable. And tech transfer is always hard.
00:20:00
Richard Schaeffer: But if you can find ways to move the science, move the process from the laboratory to the commercial entity that can create a value proposition for executing the process, then what we’ve got is a winner. We’ve got government investment in a national lab creating a solution to a problem that can then be productized and turned into a moneymaking commercial entity which then satisfies the need of a large group of people not just a couple of scientists inside a lab.
Kurt Greening: That’s a good point Dick. So, speaking of winners and commercial viability, Bill, what made you think that you needed to start a company to help solve this problem?
Bill Downer: It’s funny and it perfectly goes off what you just talked about. While still working at Seagate Federal, they were looking for a more responsible way to they’re very much into doing the responsible things for the Earth. And I got tasked by my manager to go figure out what was going on in responsible retirement and reclamation around hard drives. It led me to do a year-long research to look at various technologies.
Bill Downer: What I found was multiple DOE labs had developed differing technologies to get the magnets out of hard drives and to effectively get the materials back to a certain state. and we evaluated all those and the DOE and I’ve been on the hill a number of times since while I was doing this project. they started doing a lot of this research in 2010 before it was quite the crisis that it is now. and they have now created these various technologies. They have made them licensable to commercial firms, so we stood up a firm purpose-built to go take some of these DOE technologies and prove them out commercially but in particular with a focus on how to help DoD and the intelligence community responsibly retire the equipment from those sites in a certain manner, and to get the materials into the strategic reserve that has been set up for the rare earth elements. And so a perfect cycle to take both in from terms of chain of custody. These are devices owned by the government and giving back whatever products are produced back to the government for their own use.
Kurt Greening: I love it, solving some of both the economic problems, the data security problems as well as sustainability.
Kurt Greening: Is there anything more that you want to say about the methods that you plan to use or more detail? You talked about how you’re going to recover and then store the rare earth. Anything more you want to say about either of those, Bill?
Bill Downer: Yeah, I would say that we’re not fixated on just doing this with hard drives. DOE has done a great job of research reclaiming rare earth elements from all manners of magnets in everything, whether it’s in EVs or it’s in windmills or whatever. the windmills are a huge issue on how we retire those and what we do with them. So we’re looking at all manners of technology that have been developed by the US government labs and how to build a commercial capability that allows us to do a full life cycle of anything that has been pot bought and paid for by the government whether it’s the research or it’s the actual devices.
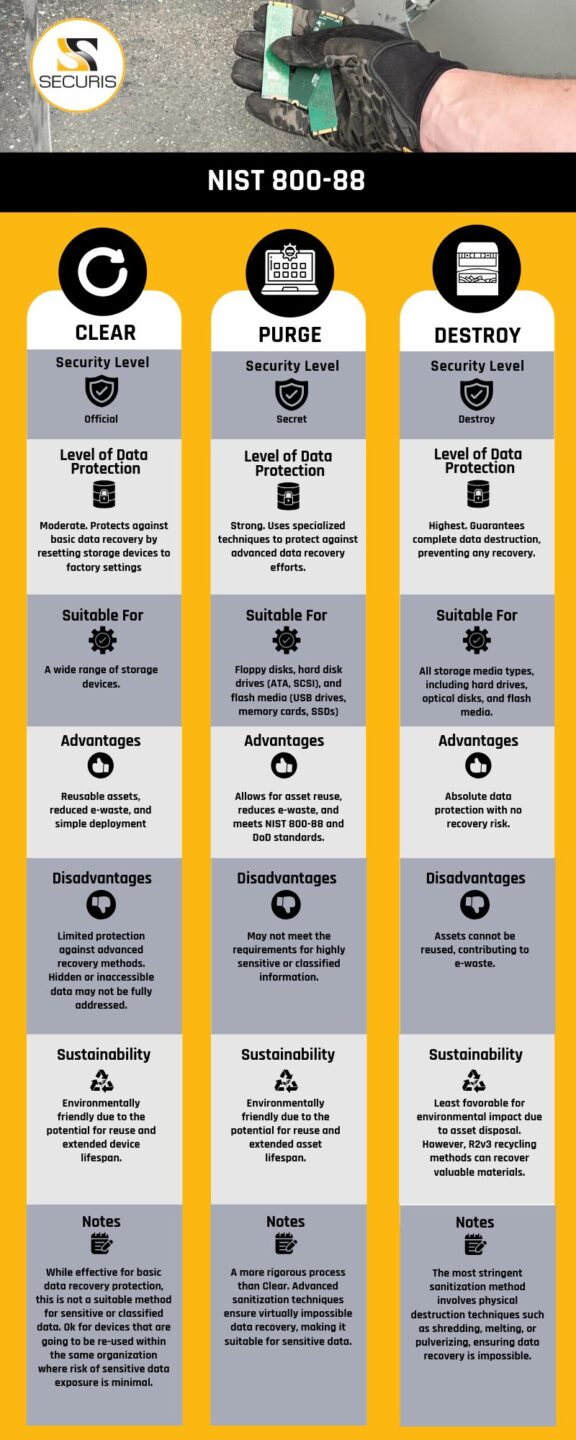
Kurt Greening: Perfect. thank you for that answer, Bill. Dick , I understand you worked at the NSA. You were explaining a little bit of this to me earlier. You mentioned it’s the center for storage device sanitization try to get it right I think now it is under what is called the cyber direct directorate can you talk about any of the standards that NSA has developed or maybe working in concert with some of the NIS standards that protect the DoD and also the DIB or the defense industrial base when it comes to cyber security risk associated with end of life electronics,
00:25:00
Richard Schaeffer: So again I’m going to use this term life cycle. If there is a national security system, so a system that processes classified information, then NSA as in its national manager role sets the standards for destruction. So they set the standard for we’ll use Bill’s example of a hard drive. they’ll tell you, you’ve got a big, you’ve got to try to remove all of the information that’s on the drive. So, you want to degauss it, you want to make sure that you’ve done as much as you can do. we talk about writing ones and zeros to the platters. that’s a method. but ultimately you’re gonna grind that thing up. you’re going to turn it into essentially a handful of metallic particles and what NSA will say this is how small those particles have to be. And so they will set the specification for the machine. Think of it as a grinder. so you’re going to throw it into a grinder, and it’s gonna, a bunch of particles are going to come out the bottom and they’re going to be of a size that NSA will say we have a high degree of assurance that no one could recover information from that device when processed through this cycle this writing of ones and zeros or degassing or grinding and ultimately you’re left with something and NSA will do that for not just hard drives, but they’ll do it for micro electronic devices, solid state drives, and so forth.
Richard Schaeffer: The challenge is so people in the national security community are aware of those specifications because they’re part of that community, but they also form a corpus of best practices that private sector that has sensitive information on their devices should also be following. So it’s in this life cycle and this happens quite often, it’ll be the Department of Defense or the intelligence community will create a process because of classified information data objects that are very sensitive and ultimately as the private sector looks at that and says it’s not classified in a national security sense but it’s damn important to me. it is the lifeblood of my company and therefore I’m going to treat that information, those data objects in the same way that the US government might treat their classified information. I’m going to be assured that in the end, nobody can recover that information and steal my intellectual property or whatever.
Richard Schaeffer: So gradually things leak from the defense and intelligence space into the private sector become common usage and the nation is better off from it. We don’t do enough, and this is where I get back to nobody being in charge. Nobody’s really pulling all the pieces together and saying, Yes, we have national security information, but we also have very industrial information. We have very sensitive health care information and we’ll all have to ensure that we’re treating all of these categories of data appropriately.
00:30:00
Richard Schaeffer: And ultimately scale means everything. if Bill’s company is only processing a thousand hard drives a week, that’s one price point. But if somebody said, Bill, I need you to process a 100,000 a week.” He’s going to get a whole lot more efficient in the way that he does that. And then the output which is sort of these rare earth elements that are ultimately recovered from these processes, become more plentiful. They become less expensive.
Richard Schaeffer: And by the way, there’s more of them that can go back into I don’t care whether they come out of the private sector or whether they come out of the national security sector. If I can feed them back into that national need for rare earth elements, I’m minimizing then the amount of material that we’ve got to import from other countries. and so there’s this term life cycle takes on a much more significant meaning because it’s Bill and rare earth elements is sort of sitting almost at the end of that life cycle.
Richard Schaeffer: something has to be done probably to process that material to get it back into the national stockpile. But that becomes a very critical part of the supply chain not just for government, but for private sector as well. And I use private sector to mean everything that’s not US government.
Kurt Greening: Thank you for that Dick. We do have some educated customers that come to us here at Securis, and they will ask us about the National Industrial Security Program operating manual. many times they will quote, 32 CFR part 117. some of my older customers will still ask about DoD 5220, which is pretty outdated. but you talk about what’s spilling into the private sector.
Kurt Greening: You know, traditionally what I hear from civilian agencies is that they are following NIST publication 800-88. but I’m also hearing that from banks and hospitals in the private sector. So the good news is the work that the taxpayer is funding around cyber security that is flowing out into organizations that are protecting citizen data our financial systems energy sector etc.
Richard Schaeffer: Let me just give you one additional piece of good news or what should be good news. NSA creates specifications, NIST creates specifications. and I’ll say people inside the system understand those things but you don’t understand the specifications for the tires that are on your car right? You just go to Goodyear, and you buy a set of tires, or you go to Firestone or whoever you go to. you go there and you buy a set of tires for your car, that’s the endpoint. That’s where we’ve got to get this to where people don’t need to know the specifications. They don’t need to know sort of, is the grinding machine, does it meet this spec?
Richard Schaeffer: What they need to know is that for the national good, they’re taking their outdated, no longer usable microelectronic devices and they’re putting them into a process that ultimately ends up doing good for the nation. And again I’m looking for this grand pooba, who’s going to be the sage on the mountain, but we don’t talk about it in that way. we talk about it in terms of the geek speak for those organizations that are mandated to do it, most of whom do.
Richard Schaeffer: But if we made it easy, if we made it economically feasible if we made it so that they felt like they were contributing to the national good in some way, and sort of other hats that I wear, I meet with investors who don’t have a clue about national security. They don’t have a clue about complex IT systems. But what they say is, “I’ve made a lot of money in my life. It’s real estate or it’s whatever they’ve done.” and I want to contribute to the national good. and so that’s the context, I think, that when we can get companies to understand that they’re contributing to the national good simply by not throwing this stuff into a landfill somewhere.
00:35:00
Richard Schaeffer: and it’s it beyond recycling. it’s actually a contribution to the national and then I think we begin to build scale. We begin to bring prices down. We begin to fill that national supply need for rare earth elements. we do the things that we need to be to become a much more self- sustaining and truly a much more self- sustaining because we’ve got the life cycle part down. Then companies Securus become a critical link in that chain as well because you’re the outward-looking face to the private sector.
Kurt Greening: Yeah, perfect.
Kurt Greening: And I probably should have mentioned the good work that folks over at NSA have done on the evaluated products list for shredders and degausers. So that’s certainly helpful. But maybe I wanted to switch the conversation a little bit. I’ve got a lot of friends who are chief information security officers, sisos, and the defense industrial base.
Kurt Greening: And I’ve had conversations with them and some of the hot cyber security topics today are software supply chain cloud security that’s all the new rage and what you have these folks talking about but do you think that the defense industrial base and the government should be paying as much attention to end-of-life electronics as some of these new hot cyber security issues?
Richard Schaeffer: Without a doubt. I believe that there are devices sitting in warehouses that have highly sensitive industrial secrets on them. I’ll use the term secrets. Maybe that’s a small S but intellectual property I think. So I’m going to give you another example, and it can be edited away but my wife has a friend who does estate sales and so occasionally he’ll need help setting up somebody’s parent dies or grandparent or some friend or some there’s nobody left and they hire a company to come in and sort of run an auction or run a sale and get rid of all the stuff. So, she did this a couple of weeks ago and she comes home and she says, “You’re not going to believe this”. This guy who died had a box and I think there were 27 hard drives in a cardboard box. and the guy who runs the estate sale said we’ll sell them for $2 a piece or $5 a piece or whatever it was. and I said, go tell Duke, don’t you dare. I said, ‘You have no idea what is on those hard drives. What if you’re selling somebody’s pornographic library? worse, what if it’s child pornography on there?
Richard Schaeffer: What if there is? You have no idea. What they ought to do is take them to a place that’s going to grind them up and shred them and get rid of them. And I think that situation occurs, all over the country probably a thousand times a day. It’s probably not pornographic libraries, but it’s probably personal banking information. social security numbers, all sorts of personal information and it’s so easy for somebody to go to a sale. I mean, these estate sales are all over, go to a high netw worth area, go to an estate sale and buy a used computer and see what’s on it.
00:40:00
Kurt Greening: Yeah Dick you’re right. So I-Sigma did a study and bought electronics off of eBay. More than 40% of them had either corporate or personal personally identifiable information on them. Rapid 7, who’s a cyber security company, they bought infusion pumps off of eBay that were in hospitals and they were able to get the wireless configuration data from seven hospital chains. So, you’re right, those things are a risk. So, I’m going to ask one last question and then maybe we’ll call it a wrap. this has been awesome. Thank you, Dick, and thank you, Bill.
Kurt Greening: So, Bill, not too long ago, maybe, I think in the last two years, it was probably going back to your time at Seagate, you started to approach Securis to, help what now became, your company, and I’ll post the link in the show notes to help the DoD solve this issue that is at the intersection of supply chain, cyber security, and sustainability. what made you decide to partner with Securus on this?
Bill Downer: So just like I did a due diligence on all the various reclamation technologies, I did a similar thing on information technology asset disposal companies and the name of Securis came up multiple times for the quality of the recordkeeping, the responsible method in which they did the work, and the fact that you were doing work for both the federal and state and local governments. And I became such a fan, and this predates you, Kurt, that I actually hosted multiple tours, I’m not sure if you’re part of these, but we hosted the industrial policy people for supply chain from the Pentagon. We hosted Defense Logistics Agency who’s responsible for the strategic reserve.
Bill Downer: we hosted the Department of Energy industrial or advanced manufacturing group and it’s interesting to me every time I was at a meeting with various government executives often that were set up by Dick what we found was that many of the people that set the policies around the supply chain around defense logistics had never visited an asset disposal facility. and so I brought them out and typically they’d say, ” I’ll give you 45 minutes and I’m out.” Couple of times, Dan and I had to run them off the facility at the end of the day because they didn’t leave because they had so many questions and here they are setting policy around responsible destruction and reclamation and yet have not had an opportunity to tour such facility.
Bill Downer: Given your proximity to the beltway, your company, it is ripe for bringing people out from various headquarter locations in the federal government to see a very responsible company do what you do. and how you do worry about the full supply chain, and keeping the proper records and keeping up to speed and being a leader in the certifications required in that industry. You are always ahead of the game. And so it was easy for me to become an advocate and host those tours. And y’all did a great job of hosting the various government representatives so they could learn more about how their policies were affecting industry.
Kurt Greening: Thank you, Really appreciate having you on, your partnership, what you’re doing for sustainability, what you’re doing to protect our national security interest, and looking forward to more great work on solving these problems.
Richard Schaeffer: Yeah. Thank you, And I just leave you with you should be unapologetic and ruthless in demanding of your government, and my government, the best process, the best approaches, you’re you live it day to day. You know what works. You know what doesn’t work. You know what what works well, what needs to be fixed.And you should be demanding of the government solutions that actually work for the masses, not just for the people as Bill pointed out, people that set the policy who’ve never actually done the work to understand what do those policies actually mean. So, be unapologetic and be ruthless.
Kurt Greening: With that, we’ll end.
Kurt Greening: Thank you for that advice, Dick.
Richard Schaeffer: Thank you.
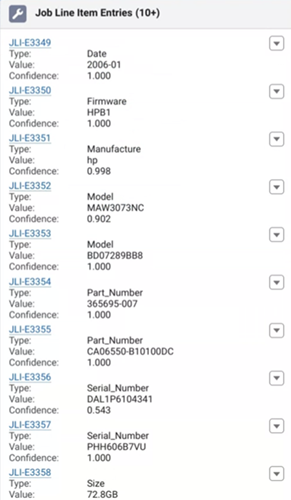
 Securis has recently upgraded our handheld scanners to Zebra TC58s, a powerful, enterprise-class handheld mobile computer designed to streamline and improve inventory management. The TC58 is fantastic at capturing barcodes, even if they are damaged or poorly printed. Powered by a robust Qualcomm Snapdragon 8-core processor, the TC58 enables faster and more efficient operation, allowing it to handle demanding applications effortlessly, ensuring a seamless and efficient scanning process.
Securis has recently upgraded our handheld scanners to Zebra TC58s, a powerful, enterprise-class handheld mobile computer designed to streamline and improve inventory management. The TC58 is fantastic at capturing barcodes, even if they are damaged or poorly printed. Powered by a robust Qualcomm Snapdragon 8-core processor, the TC58 enables faster and more efficient operation, allowing it to handle demanding applications effortlessly, ensuring a seamless and efficient scanning process.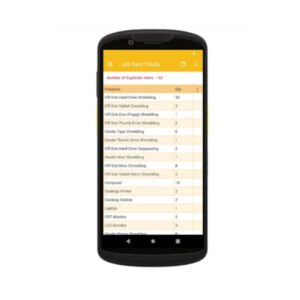 Mistakes are inevitable when scanning thousands of assets daily. Industry data suggests that scanning accuracy typically falls below 85%. A common issue is the inadvertent duplication of scanned items, leading to time-consuming investigations.
Mistakes are inevitable when scanning thousands of assets daily. Industry data suggests that scanning accuracy typically falls below 85%. A common issue is the inadvertent duplication of scanned items, leading to time-consuming investigations.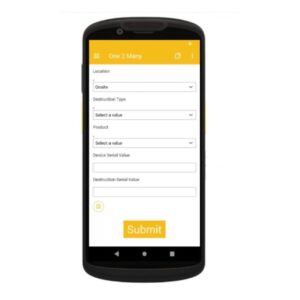 One of the most significant challenges in ITAD is ensuring that every asset is correctly matched to its corresponding storage device before being securely disposed of. Many of our clients, particularly those in the banking and financial services sectors, require assets to be matched to their storage cabinets for compliance and financial reasons.
One of the most significant challenges in ITAD is ensuring that every asset is correctly matched to its corresponding storage device before being securely disposed of. Many of our clients, particularly those in the banking and financial services sectors, require assets to be matched to their storage cabinets for compliance and financial reasons.



 What is Unified Endpoint Management (UEM)?
What is Unified Endpoint Management (UEM)?

 In a fast-paced digital environment, businesses must constantly upgrade their technology to remain competitive. Millions of electronic devices are discarded or replaced yearly, creating an escalating
In a fast-paced digital environment, businesses must constantly upgrade their technology to remain competitive. Millions of electronic devices are discarded or replaced yearly, creating an escalating  Ultra-secure IT recycling
Ultra-secure IT recycling Collection and Inventory
Collection and Inventory Securis’ data erasure processes meet or exceed industry standards such as
Securis’ data erasure processes meet or exceed industry standards such as  The benefits of computer and device donation extend beyond the donating company, making a significant impact on communities in need:
The benefits of computer and device donation extend beyond the donating company, making a significant impact on communities in need: As technology evolves, the need for responsible
As technology evolves, the need for responsible 
 Degaussing: Erasing with Magnetic Force
Degaussing: Erasing with Magnetic Force Shredding: Crushing the Problem
Shredding: Crushing the Problem MicroShredding: Taking It a Step Further
MicroShredding: Taking It a Step Further Choosing the Right Method for Your Needs
Choosing the Right Method for Your Needs The Role of Professional Data Destruction Services
The Role of Professional Data Destruction Services Beyond Hard Drives: Other Media to Consider
Beyond Hard Drives: Other Media to Consider Conclusion: Taking Data Destruction Seriously
Conclusion: Taking Data Destruction Seriously