This is the transcript of a conversation about Hardware Asset Management between and Jeremy Boerger, the author of the Pragmatic ITAM Method and a consultant who helps large organizations implement IT Hardware Asset Management solutions. You can find Jeremy at: https://www.itamcoaches.com
00:00:04:07 – 00:00:38:01
Kurt Greening
So welcome, everybody. Today, I am joined by Jeremy Berger, the creator of the pragmatic ITAM method and a consultant who helps large organizations implement great IT asset management. Jeremy’s been solving problems in this area since 2000, and he uses data theory, automation, self-governance, while others just are answering questions or excuse me, answering tickets and running inventory reports. We’re talking about hardware asset management today, but Jeremy also helps people solve problems with software asset management. SaaS, spend management, and financial operations. Now, there is a lot of debate today about remote work. Many companies are ordering at least a partial return to office, but the IT asset management problems for remote organizations, or at least people who are hybrid, they’re not going away.
So my name is Kurt Greening. If you don’t know me, I am an executive VP with Securis. Our primary business, is IT asset disposition, but we also help companies manage the hardware assets of remote employees. Jeremy, thank you for joining us today.
Jeremy Boerger
It’s my pleasure. Kurt, thank you for having me.
Kurt Greening
Awesome. So I have a few questions for you as, industry expert. First one I would, love if you can share some of the challenges that you may have noticed in your career when it comes to managing remote employees hardware assets.
Jeremy Boerger
Yeah. So the, the biggest challenge is getting to them, that’s the real problem. It’s either getting that hardware out to the end user and then getting it back when that end user, goes away or goes through a, refresh, and they get new equipment. now you’ve also got, a secondary problem with the communication piece. Inside the United States, we’ve got a much more robust data infrastructure. Most organizations, especially when, hybrid work was first being experimented with, maybe you had the old twisted pair, riding alongside your home phone line. Remember when we had home phones? Yeah. and that was a real challenge for no other reason than just to get the disposition of that device. Is it on? Is it working? Is it getting patched? nowadays we’ve got high-speed connectivity all over the place. for the most part. And so that kind of concern goes away. But the real challenge is getting the device and the entire setup over to the end user and then getting it back when they’re done with it.
Kurt Greening
Yeah. I worked for a remote-only company, so that was interesting. I actually did all of my interviews on, video. Via zoom. it’s a little nerve-wracking to accept a job that way, but onboarding, was also, completely remote. And, you know, you mentioned some of the challenges. I think getting the equipment is a challenge. If I were to, I would make a challenge getting the equipment back, especially with a less-than-happy employee. It’d be an even bigger challenge if you don’t make that super easy as an IP asset manager or a helpdesk organization. I don’t think you’re going to get that equipment back in a timely manner.
Jeremy Boerger
Right. You’re right. And in so when you’re dealing with that, you’re really as an asset manager, you’ve got to make a calculation. risk calculation in your head. once the real value of that device, sometimes it’s the value of the device itself. Don’t get me wrong. I work for an organization that does, animation, computer animation for entertainment, cartoons, and all of that stuff, that’s some high-powered stuff that is cranking along, doing ray tracing and, generating the frames. So there is still value in that. But for most organizations where the real value is, is in the intellectual property, in the data that’s stored on that device. So one of the ways that you can get around that problem is to have a more robust data destruction, cooling, and methodology that if you can remotely eliminate access to the IP from that device, that sometimes will alleviate some of the risk.
00:05:27:05 – 00:05:55:02
Kurt Greening
So that is a good point. Jeremy, you’re about to get into my next question. Which are some of, what are some of the software tools that are available to help improve, cybersecurity saying you mentioned remote wipe. you know, typically, most of my customers here at Securus, they’re using like, an end user management software or a mobile device management software. you know, to help with, you know, to help manage that solution. But other than that, or maybe talk about some of those features or other tools similar to that, that that make managing those, remote and user devices a lot easier.
Jeremy Boerger
Right. So, it, it’s tough to be able to talk about them because the technology itself is actually rather simple. It is just being able to have an inventory and the tool being able to reach out and send commands, to that device. from either a pre boot or, or a stance or an operating system where really there’s new tools that are coming on all the time. what I recommend for as part of our pragmatic ITAM method is stick with the easy ones.
Intune for your Windows devices. Jamf for Apple. There’s others that will also do the work, but those those two are the big ones, and they will get the job done. Encryption, also seems to have we’ll also have some, remote destruction or, magic bullet commands. sometimes that can go on. And with the, when you start talking about phones and contact lists and the, two factor authentication with some of those, oh, you know, the random number generators, in those password like that.
Those will also work so that you can lock down and immobilize the device, make it useless. not only does it protect any of the random bits that might still be on that device, but also gives, an incentive for the end user to give it up and send it back home, because they’re not going to be able to do anything with it anyway.
Kurt Greening
Yeah. I mean, I understand that some of these solutions also offer like GPS tracking. You mentioned enforcing specific cyber security policies to make sure that they’re safe on the on the network. You know, they might be working in conjunction with anti-virus software or, you know, more sophisticated, tools that are out there, you know, so I think all of those can be incredibly helpful.
Jeremy Boerger
Oh, yeah. And, you know, it’s what I, what I see in my book, you know, the best tool for the job is the one you’ve already got. So use the stuff that you’ve already got access to. Again, Intune is already there. If you’ve got a Windows volume license agreement or you’re part of the, you’re, you’ve got access to, oh, crud. What are they calling their Azure? what they’re calling their device, their cloud system.
Kurt Greening
And they used to call it. oh, I forgot. I think it’s now M365. But, you know, some of the really advanced security features might be the M5. or E5 offering.
Jeremy Boerger
Yeah. Yeah. And then actually brings up a good question, or a good thought as well. The proliferation of cloud storage remote backups mean that the risk of loss of the IP, the at the risk of the access of the loss of intellectual property or for an organization actually helps become minimized because so long as that device is inoperable, they have a backup copy that they can reach into. Any data or, intellectual property or whatever other files are needed.
00:10:00:12 – 00:10:16:03
Kurt Greening
I think you did a great job talking about how many of these, software tools can help remotely support these users and help with IT asset management. But there are certain problems that can’t be solved remotely with software. Can you give me an example of some of the challenges that organizations run into with remote employees?
Jeremy Boerger
You know, I am old enough to remember the old joke about the, the end user who plugged the, following the instructions to the letter plugged the, power strip into the power strip. I don’t know if we can solve that one, with software, but, you know, in today’s age, there’s a lot of, the the end user is a lot more savvy around technology, but some of the problems that you that you’re going to struggle with, are going to be the usability and the process side. And if you don’t have robust processes, around things like data handling and, inventory management and, recovery processes, what are those steps to get those devices back? You’re going to struggle. and there’s not much just throwing another magic bullet, piece of software at that problem is not going to make the poor processes go away.
Kurt Greening
Yeah, I mean, that’s true. I mean, I’ve talked to many of my friends that work in that helpdesk, and some of them are incredible at this job, in their job. They’re they’re highly committed. They tell me stories of, hey, I did everything I could to support this person. They had something, you know, critical coming up customer presentations. I got in my car and I drove four hours with a new, laptop with a fresh image, picked up their old one and took it home because there was nothing more that I could do.
Jeremy Boerger
I had worked Help desk one time and we were able to troubleshoot. the connectivity issue actually came down to the feed line into the, subdivision, buried cable line, and the reason why we were able to figure it out was because I was the first person to ask the guy point blank, the person that we were helping what’s the picture quality on channel two and channel three, which is where the on the old cable modems, that’s where the the data line there on channel three. And I think part of channel 13, he was like, oh it’s terrible. It’s like, how well do you know your neighbors? Can you talk to them? And just that persistence, that systemic thinking of going, okay, we’ve tested every possible issue with the hardware. We know it’s not the software. Then what happens next? That’s systemic thinking about okay, what’s the next device or issue in line that could be causing the problem and then start to troubleshoot it. If I remember right, the cable company came in and replaced all of the wire in that subdivision. It was 20, 30 houses, between the house and the street.
Kurt Greening
Interesting. Some some good, good war stories there. Jeremy.
Jeremy Boerger
Oh, yeah. That’s. Yeah, that’s the nice thing about helpdesk. Everybody’s got a war story.
Kurt Greening
Yeah. And, speaking of some of these challenges, why do you think, some companies or maybe even government, organizations might for, outsource laptop logistics, data sanitization, re-imaging imaging repair.
And then eventually, when they’re done with the device recycling that somebody like Securis.
Jeremy Boerger
Yeah. So, there’s, there’s a couple of reasons why it starts to make sense. The first is scale. as an organization grows, the demands for the disposal, the recovery, the disposal and the, recertification if you’re going to reuse it, all of that starts to become cumbersome and pulls attention and material and resources away from the business’s core focus.Right. If you are, manufacturer, you make airplanes. The last thing you want is people spending their time, hitting laptops with hammers to destroy the platters. Right. So outsource that. the second part is, if you are dealing with very heavily, abused, data, thinking, healthcare, thinking, finance, and government, there are specific regulations that you’ve got to follow and your organization might not be able to keep up with all of those regulations. A dedicated third party service provider, that’s the folks to go to. Finally, off the top of my head and thinking about it, if you are an organization that is in a very heavily congested urban area warehousing becomes a premium and you really want to have, square footage being paid out for devices that are just sitting there because they’re either being prepped or being removed, t hat’s money out the door that, you know, you could redirect somewhere else, especially if you have a, just in time relationship with, third party service provider.
Kurt Greening
Yeah, there’s a real good point. Yeah. I, I, you know, there’s kind of a space between, you know, a really small company that would outsource everything from an IT perspective to an MSP. And then, you know, I’ve got a customer and it’s a big hotel chain, and they have regionally dispersed helpdesk people, within a two-hour drive of almost, every major, property, so they don’t have a problem, but there’s kind of that in-between space where somebody is like, hey, we’ve got to help desk people, but either they’re not physically close to all those people you mentioned, you know, the warehouse issue or, you know, working for companies. You know, I know of a big company in the software space lab, Gitlab, they don’t have a corporate headquarters so they wouldn’t store the laptops anywhere, so there’s kind of that interesting space where, you know, you’re big enough to have a, you know, your own IT helpdesk to understand your applications, understand your software, but maybe you don’t have somebody in every region or what I’ve been told is that, providing hardware support, you know, shipping stuff out and boxes for somebody who’s got a bunch of, you know, network and helpdesk certifications, they may consider that to be soul-sucking work.
Jeremy Boerger
Yeah. Yeah. Could be too. Could be too. The other thing to consider is how you’re actually using the technology, so many of the used to be onboarded software activities are now residing in the cloud or are accessed through a web browser. It doesn’t matter what kind of platform you’re using. All you really need is a consistent connection to that SaaS provider. Apple Mac, however it’s configured, doesn’t matter so long as the connection is secured. Maybe a VPN, some sort of, certificate. You’re off to the races, so go out, pick up something at Walmart and bring it back to your home.
Kurt Greening
Awesome. Well, good. Good advice. So let’s say the company comes to you and you’re doing some IT asset management consulting to you, and they mentioned this as a problem. And they say hey, I’m going to outsource or possibly outsource some of this. What would you recommend that they look for. What types of questions should they ask of potential providers that will help them figure out what solution might be right for them?
Jeremy Boerger
So the first question that really needs to be asked is, what kind of a relationship do you want with this third-party service provider? They really, the services break off into two aspects. One is either that just-in-time inventory provision, or they are doing just, dross, haul away the garbage give you a certificate that they’ve destroyed it, and you wipe your hands of it. I’ve seen both. if you are going to go the dross method, then there’s some other sub-questions that you’ve got to ask the people that are doing the inspection. They’re going to be your employees. Are you okay with having someone spend, you know, an hour or two a day for a small organization every once in a while to an entire team of 3 or 4 people going through, examining the usefulness of the device, deciding whether or not it can be reused and put back out into, the computing environment. And then goinging through the activity of wiping it out, doing the DoD five-time wipe. Sometimes that goes for a while on these big, on these big hard drives. Cybersecurity is also starting to poke at some of the persistent memory. So you’ve got to really have some specific tools to break apart the chassis, to get to that memory and make sure that it’s disposed of.
00:20:25:11 – 00:21:01:09
Jeremy Boerger
Is the organization comfortable with having that dedicated team? Now, the last part that I kind of worry about for organizations, if they’re taking on this task on their own, is the sort of, certification of destruction. The insurance companies, especially the ones that are providing cybersecurity insurance, are very twitchy about their documentation. And they want that confirmation that that device has been destroyed.
Jeremy Boerger
Right. if you’re doing it yourself, it’s very easy to break that chain of custody and lose track of that certificate. And then you’re talking some serious money, your insurance. There’s a very real threat that your insurance, policy could be voided, and that’s the last thing you want to have happen if all of a sudden you need it, right?
Kurt Greening
Yeah. I call it thinking of defensible IT asset management or defensible IT asset disposition. Right. Yes. Do you have a policy. would it be considered best practices and do you follow that policy? Right?
Jeremy Boerger
right, right. Well, and I have seen, the, the, TSP’s, they will go so far as to say specifically when they make a run to pick up a lot, they own those devices. Once they obtain custody, they, assume ownership and reliability. Even then, you want that receipt. What did they pick up? When was that date? And you need to store that in your CMBB or, records repository in case anything happens.
Kurt Greening
All right. Let’s talk let’s talk about systems because you, If you don’t mind, unless you have another thought on that topic, right. So, let’s say and I think you can answer both questions. So you talked about outsourcing IT, asset disposition and data destruction. That’s maybe one relationship. But there’s also the other relationship we talked about where, hey, you’re managing deployment, wiping retrievable redeployment of of IT assets. Talk about some of the systems, whether it’s, ITAMsystems or ITSM systems, that have to be in place, and what do you kind of think that that relationship would be like in both of those scenarios?
Jeremy Boerger
Right. So when you are talking about just in time, supply, inventory, you own those devices, but you might not necessarily be in physical control of those devices. So the question comes down to where is your stuff? Now, you know, if you’re a small operation, maybe you can take somebody’s word for it that, oh, yeah, that box is sitting on our shelf, and that’s great. But if you’re going to be a large organization and you need to know where that inventory is, especially if you’re going to start doing some automation between your onboarding and procurement and removal and disposal. You have to have, reach into that third-party service provider’s inventory. And in order to do that, the best way is that you both have inventory systems and you’re sharing data back and forth with an API call, or at least some sort of automated report.
Kurt Greening
I’ve actually seen that happen two ways, Jeremy. So I have seen it happen where let’s say there’s, you know, 5 or 10 spare laptops that are inventory. They’re owned by the company, not by the outsourcer, and then all actions are actually done in the company or the customer’s ITSM system, and the IT asset management database. And then there’s various workflows, like hey monthly that outsourcer has to scan and prove that what you know is in the IT Asset Management inventory is actually, you know, still owned, you know, it’s still in, you know, a locked page or whatever the agreement, is that’s, you know, that’s one scenario. And also, you know, that the Outsourcer may get a helpdesk ticket assigned to them. You know, they perform an action that’s updated in the ITSM, system. You know, if there’s tracking numbers, you know, all of those things. I think that that’s that’s another way, right? Is if you are willing to, sign agreements and you would allow that third party to have access to your systems.
00:25:37:00 – 00:26:21:12
Jeremy Boerger
Oh, yeah. No, the, the the visual inspection is costly, but it is necessary for the, “just to be sure”. And let’s remember these are devices that nine times out of ten are not plugged into the network. They’re just sitting there ready to go for the next step. But they’re dark. They’re off the wire. So unless you have really good controls on the, live side, you know, you’ve got, a good tie-in or good reports from bills of lading that say when stuff is getting received in the inventory, you’ve got your discovery tools running full bore, so you know what’s powered on and being used actively. And you’ve got your certificates of destruction being updated regularly, then what should be in that room should be the stuff that you know you own, but you haven’t seen it on the wire yet. But things happen. Things change. Stuff gets moved. I lose track of water bottles all the time. It happens, so I, I really like, I believe if memory serves, the best practice is really once a quarter.
If you’re in a just-in-time inventory relationship, have a visual inspection. It’s a great time to just go and build the, the personal relationships as well with your, service provider. Go. Everything looks fine. Freedom to launch.
Kurt Greening
Yeah. I mean, I’ve also seen a requirement for monthly scanning of the asset tags and a photograph in addition to the quarterly visual inspection.
Jeremy Boerger
That’s pretty brutal. I mean, but again, if you’re in an organization and you’re uncomfortable with risk, then, yeah, you’re going to make demands like that.
Kurt Greening
Talk about other demands. We talk about IT Asset disposal. you know, I have some customers that they provide an inventory, we go up on-site, we scan everything that they give us. We cannot leave until there is a 100%, match. You have all the serial numbers, the asset tags and the Securis disposal tags. And then, there are photos taken of what is in the truck. The truck is locked. The truck is sealed. The truck is GPS tracked. It goes to our location. The items are scanned again. That scan is compared to the inventory, the two other inventories, and if one, item is off, then they start an investigation to figure out, do they have a cyber security incident or not? So to me, that’s what good inventory management, looks like, and I mostly see that from banks. I’d like to see that in some other industries as well.
00:28:46:10 – 00:29:21:01
Jeremy Boerger
It’s certainly, again, with financial and health care, there is so many nefarious activities that are going on. You have to be careful. honestly, between you and me, I would think that that level of chain of custody is pretty extreme. I hope your customer is paying for that level. For most organizations, the bill of lading is actually plenty to be able to tell you.
You know, here’s the truck, and here is the driver, here’s the expected delivery. Did all of the serial numbers that they said that the the delivery company picked up actually make it? And if that didn’t happen then that specific piece, that delivery driver is going to be in the hot seat. so there’s a range and I and that’s really where it kind of comes down to where you and I can agree. It’s that level of risk and the management of that risk through the collection of the details and the data about where those devices are between you handing the physical custody over to a third party and then saying, you know, providing a receipt that says, yes, we did the needful, this thing is now a small pile of molten metal. You’ll never see it again.
Kurt Greening
So this is all, good advice. Clearly, Jeremy, you’ve been doing this a long time. you’re an expert in many things. Hardware asset management, many things. Software asset management. So I appreciate you, sharing some things both with me and folks that watch the Securis YouTube channel. I guess the question is, some people are, are thinking about some of the things, some of the problems that you solve and they think that you might be able to help them. Where where can they reach you?
Jeremy Boerger
Well, you can find us on our website, boergerconsulting.com. weird German spelling though, that’s B o e r g e r, otherwise you end up at McDonald’s.
Kurt Greening
Now ITAM coaches, does that also get to your company to or…
Jeremy Boerger
ITAM coaches. Yes. So and this might be the right time to talk about that. We’re looking at doing a little bit of expanding and doing a brand name. So the ITAM coaches, URL will point to us as well.
Kurt Greening
All right. Awesome. Well, hey, thank you again, Jeremy Burger. really appreciate your insight. suggest that, people pick up your book. That ITAM pragmatic Method, or follow your blog because there’s a lot of good advice. I know, I read that it seems like maybe weekly or every other week you’re putting out good content. So I think thats another way to try to keep up to speed with all things I.T Asset management.
Jeremy Boerger
Iit is it is a moving target to keep up with the details and the best business practices. So, you know, we’re happy to help educate where we can, and partner you know that’s really kind of, if there’s a closing thought, having someone help you out, can be very beneficial. So consider it. Gartner already released an article saying it’s a good idea, Forrester followed in suit, as they do. You don’t have to do this alone.
Kurt Greening
All right? Sounds wonderful. Thank you so much.
Jeremy Boerger
My pleasure. Kirk. Good luck to you.
 The Office of the Inspector General (OIG) discovered that an FBI-controlled facility had classified and unclassified law enforcement data stored on pallets without adequate protection. If these items had been wiped or degaussed on-premises, there would have been at least one layer of protection before transportation took place.
The Office of the Inspector General (OIG) discovered that an FBI-controlled facility had classified and unclassified law enforcement data stored on pallets without adequate protection. If these items had been wiped or degaussed on-premises, there would have been at least one layer of protection before transportation took place. 
 Triple-Check Guarantee: Multi-step verification ensures hidden drives don’t slip through the cracks.
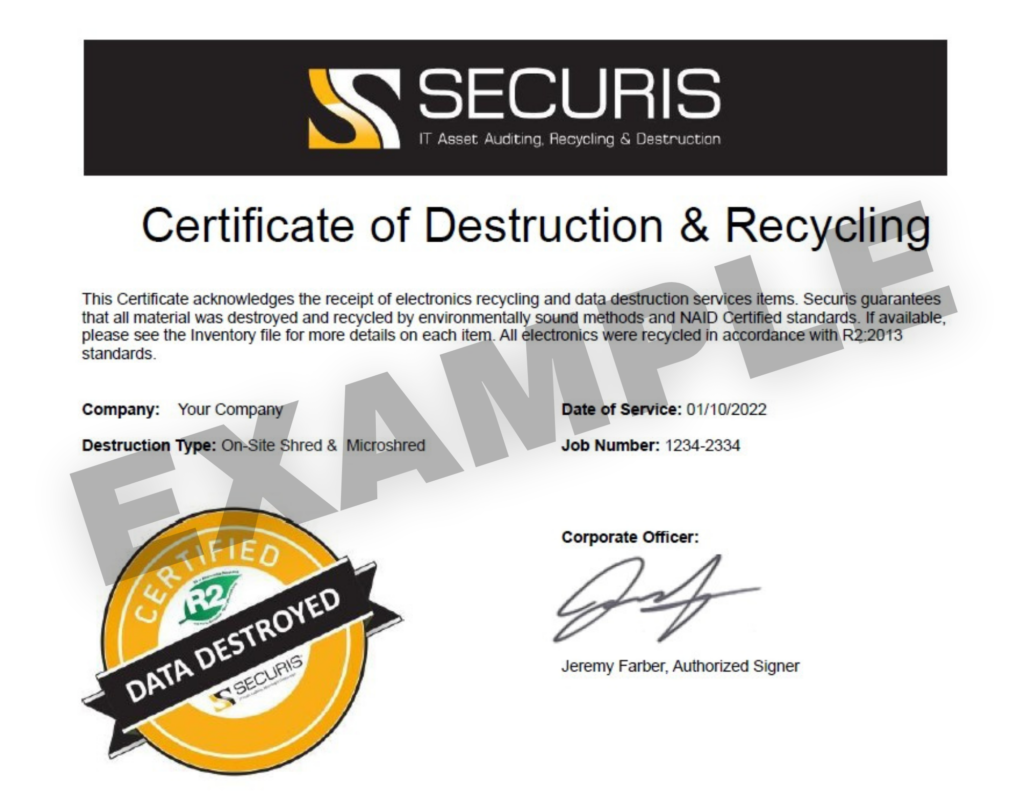
Triple-Check Guarantee: Multi-step verification ensures hidden drives don’t slip through the cracks. Capabilities: Can the vendor perform shredding to required destruction standards for various assets and storage media types? Do they provide a strong chain of custody and certificates of destruction?
Capabilities: Can the vendor perform shredding to required destruction standards for various assets and storage media types? Do they provide a strong chain of custody and certificates of destruction?









 In Chad’s Adventiste Hospital, the impact was just as profound.
In Chad’s Adventiste Hospital, the impact was just as profound.  Sustainability Meets Social Change
Sustainability Meets Social Change







 The vendor must use approved destruction methods to ensure data cannot be recovered. These include:
The vendor must use approved destruction methods to ensure data cannot be recovered. These include: Vendors must provide detailed documentation to demonstrate compliance, including:
Vendors must provide detailed documentation to demonstrate compliance, including:
 Introduction and Company Overview
Introduction and Company Overview Experience and Expertise
Experience and Expertise R2v3 Environmental Compliance
R2v3 Environmental Compliance Data Destruction Methods
Data Destruction Methods Reporting and Documentation:
Reporting and Documentation:
 Value Recovery
Value Recovery





 Securis has recently upgraded our handheld scanners to Zebra TC58s, a powerful, enterprise-class handheld mobile computer designed to streamline and improve inventory management. The TC58 is fantastic at capturing barcodes, even if they are damaged or poorly printed. Powered by a robust Qualcomm Snapdragon 8-core processor, the TC58 enables faster and more efficient operation, allowing it to handle demanding applications effortlessly, ensuring a seamless and efficient scanning process.
Securis has recently upgraded our handheld scanners to Zebra TC58s, a powerful, enterprise-class handheld mobile computer designed to streamline and improve inventory management. The TC58 is fantastic at capturing barcodes, even if they are damaged or poorly printed. Powered by a robust Qualcomm Snapdragon 8-core processor, the TC58 enables faster and more efficient operation, allowing it to handle demanding applications effortlessly, ensuring a seamless and efficient scanning process.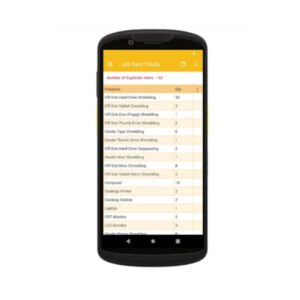 Mistakes are inevitable when scanning thousands of assets daily. Industry data suggests that scanning accuracy typically falls below 85%. A common issue is the inadvertent duplication of scanned items, leading to time-consuming investigations.
Mistakes are inevitable when scanning thousands of assets daily. Industry data suggests that scanning accuracy typically falls below 85%. A common issue is the inadvertent duplication of scanned items, leading to time-consuming investigations.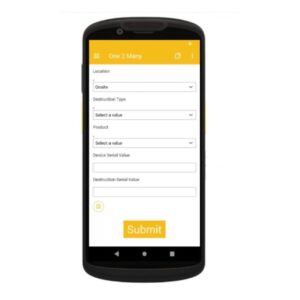 One of the most significant challenges in ITAD is ensuring that every asset is correctly matched to its corresponding storage device before being securely disposed of. Many of our clients, particularly those in the banking and financial services sectors, require assets to be matched to their storage cabinets for com
One of the most significant challenges in ITAD is ensuring that every asset is correctly matched to its corresponding storage device before being securely disposed of. Many of our clients, particularly those in the banking and financial services sectors, require assets to be matched to their storage cabinets for com