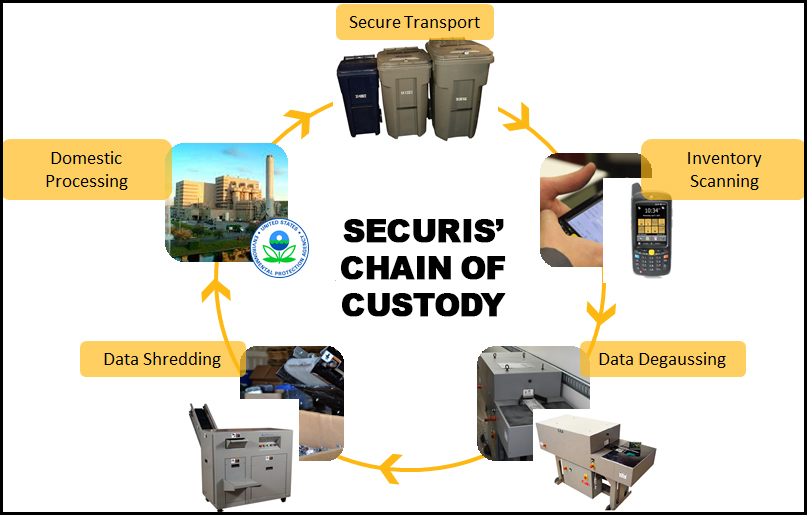
Sometimes, a standard shredder isn’t enough. For highly sensitive information, especially on smaller devices such as solid-state drives (SSD) and cell phones, it’s recommended that data is shredded using a micro-shredder.
For the most sensitive jobs, the material must be run through a micro-shredder that has been evaluated and verified by the National Security Agency (NSA). NSA-certified shredders have been reviewed, extensively tested, and approved by the NSA to ensure that SSD and phone particle shredded size is less than 2mm – the width of an uncooked spaghetti noodle.
Why Shred SSDs and Cell Phones to the NSA Recommended Particle Size?
There are a number of reasons. They all come back to the overarching need for data security and verification of destruction. It’s next to impossible to retrieve any useful information from such small components.
Shredding to the 2mm NSA standard means that sensitive data stored on solid-state drives and cell phones – be it corporate financial information, medical records, and even state secrets – is not able to be recovered. The 2mm size is necessary for solid-state drive destruction.
“Having an NSA-approved micro-shredder is really getting the agency’s seal of approval,” says Dan Mattock, Securis’ Vice President of Sales. “Some jobs require total destruction of their assets. For those jobs, we can offer either degaussing of magnetic drives – which erases and renders the drives useless – and shredding solid-state drives to the 2mm NSA standard. Both of these processes ensure total destruction of information and data.”
Given that Securis has the option to securely shred SSDs down to the NSA standard, the question arises as to whether or not this type of secure shredding is necessary for other businesses, as well. The answer is yes. There are tremendous benefits of shredding data on SSDs and cell phones down to the NSA standard for particle size. This holds true for government entities, banks, healthcare organizations, and technology companies.


“There is no better method of data destruction,” says Mattock. “We read all the time about data breaches and the damage they cause. Micro shredding to the NSA-approved size ensures that all information is eliminated completely. This means everything from customer data to business strategic plans and competitive analyses are destroyed and cannot fall into the wrong hands. It’s peace of mind that the highest standards of data destruction possible are adhered to.”
What it Means to be Certified for Data Destruction by the NSA
To obtain an NSA certification, a shredder must be verified to shred to the 2mm size. The shred particle size for SSD needs to be 2mm. Random samples are examined under a microscope by a team of NSA analysts. The examination team then needs to certify that the shredded components are rendered totally inoperable.
Other tests are run based on the latest hard drives, as well as the safety and security of both the machine and the shredded assets. Only if a shredder passes all of these inspections will it be considered certified by the NSA, granting the machine a seal of approval by a panel of third-party experts.
“NSA-certified shredders are like the Good Housekeeping Seal of Approval for SSD destruction,” Mattock explains. “We are able to give our customers peace of mind that we are remediating their data to the highest, most exacting standards in the industry. That is why so many businesses across so many different industries team up with us for their data and asset destruction.”
Curious about phone and SSD destruction? Call Securis today for a free quote.