Quite a few customers have asked us exactly how we shred a hard drive. To help explain this, below are the steps that a magnetic hard drive goes through.
Introduction to the Shredder:
The hard drive is placed into the shredder. Industrial shredders for electronic equipment like hard drives typically have solid and metal-cutting blades.
Cutting Mechanism:
The blades in the shredder are made of heavy-duty metals, such as hardened steel or tungsten carbide. Depending on the shredder’s design, they are arranged in a crisscross pattern or a spiral or helical arrangement.
Initial Contact and Cutting:
When the magnetic hard drive passes through these blades, the outer casing, usually aluminum or hard plastic for external drives, is first cut. The strength and sharpness of the blades allow them to slice through this material.
 Destruction of the Magnetic Hard Drive’s Internal Components:
Destruction of the Magnetic Hard Drive’s Internal Components:
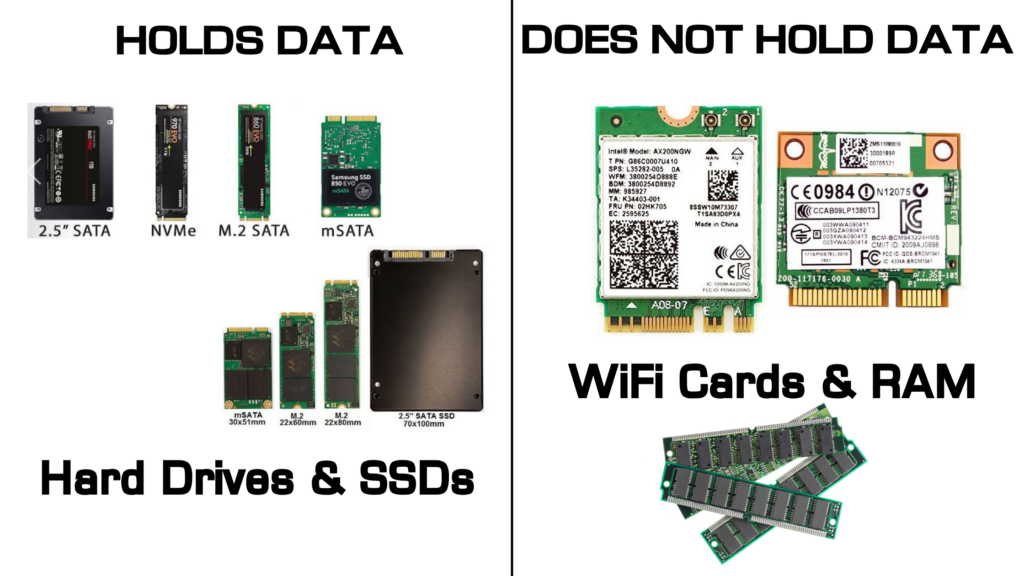
As the shredding continues, the blades come into contact with the hard drive’s internal components. This includes the platters (which store the data), the spindle, the read/write arms, and the circuit board. The blades are designed to cut through these materials, breaking them into smaller pieces.
Fragmentation of Platters:
The platters, typically made of aluminum, glass, or ceramic coated with a thin layer of magnetic material, are the most crucial part of data storage. The shredder blades must be strong enough to deform and fragment these platters, making them unreadable.
Discharge of Shredded Material:
The resulting debris, consisting of small metal, plastic, and other materials, is expelled from the shredder. This material is usually collected for disposal or recycling.
 Ensuring Data Destruction for Magnetic Hard Drives:
Ensuring Data Destruction for Magnetic Hard Drives:
The effectiveness of the shredding process in destroying data is due to the physical deformation and fragmentation of the platters. Since data is stored magnetically on the surface of the platters, their physical destruction renders the data unrecoverable.
The entire process is quite forceful and noisy, requiring robust machinery. The shredders must exert significant force to break down the hard drive’s materials, especially the metal components. The shredder’s design, including the blades’ pattern and strength, is crucial for thoroughly destroying magnetic hard drives.
Read more about how Securis destroys hard drives here.


 How Does R2 Certification Promote a Circular Economy in Electronics?
How Does R2 Certification Promote a Circular Economy in Electronics? How Can I Verify if a Company Is Truly an R2 Certified Recycler?
How Can I Verify if a Company Is Truly an R2 Certified Recycler?