Transcript from Video :
Kurt: Good afternoon, Dan Mattock How are you?
Dan: Hey good afternoon Kurt. I am doing awesome. How are you doing?
Kurt: I’m doing great. Yeah, it’s wonderful to talk to you, Dan. Today. today, I’d love to, talk to all our YouTube fans about, electronics OEMs or original equipment manufacturers and how they are investing in the circular economy. So thanks for joining me today.
Dan: Thanks so much for having me. This is this is great. I’m excited here.
Kurt: Awesome, So for those of you who may not know, Dan Maddock, Dan Maddock is Vice President with Securis He’s actually been with the company for, more than 15 years. he holds a number of certifications. one is a CSDS, which stands for certified secure data destruction specialist. Dan also holds a certification, in LEED, which is the Leadership in Energy and Environmental design certification. many people know Dan from his role as the president of the Northern Virginia chapter of the National Property Managers Association. which is pretty cool. But, today, really I’m interested in talking to Dan because of his experience consulting with some of Securis’ largest customers on the topic of data security, the circular economy, as well as IT asset disposition, best practices. So Dan, I’m super excited to learn from you today.
Yeah, this is great. Thanks, Kurt
Kurt: All right. Dan. So not everybody listening to this podcast is going to understand the term, circular economy. So can you help just and maybe in layman’s terms, give me an idea of what that means. And especially as, as it, you know, with respect to, electronics manufacturers.
Yeah, sure. Absolutely. So, yeah, the term circular economy came on the scene. let’s say I’ve heard it used more and more often from maybe about 5 to 10 years ago, is when it really started. But the gist of it is that it’s basically an economic system. It refers to an economic system designed to minimize waste, make the most efficient use of resources by really keeping products, materials, resources, as long as possible. And maybe that’s through the design of the product initially, or it’s during its full lifecycle towards the end of the lifecycle, trying to find ways to reuse the product, even repairing or refurbishing, and then even towards the end, recycling the product in a way where all those raw materials can go back into new products.
And so, yeah, in regards to electronics, what’s interesting, one example where we see of this is so the EPA, they’ve published some calculators that just show how much better it is for the environment. first of all, first of all, if you can recycle the electronics, but even more dramatically is if you can reuse the products and extend their life, it’s actually dramatically better for the environment in terms of not having to tap into some of the virgin materials that are so costly, to, to mine and so forth.
Kurt: Yeah. that’s an incredibly, big deal. Thanks for, helping us understand the circular economy. You know, electronics obviously is your expertise, but I saw a segment on PBS news where, clothes were ending up on a beach, in Africa. super, super disappointing. but we also heard the stories, you know, electronics or electronics components, going overseas where they were supposed to be recycled and, ended up in landfill. So I think, I really applaud the efforts, many of the vendors that we work with, you know, people like HP and Dell all have initiatives around, circular economy. And then, of course, we’ll talk later about, contract manufacturers, meaning that people that manufacture everything from iPhones to, to, to servers, but, you know, sometimes people, people buy things and for whatever reason, whether there’s an issue with it or maybe it was the wrong item. sometimes we have to return those items. So, I’ve, I’ve recently learned more about a feature called reverse, logistics So can you help me understand that a little bit more Dan?
Dan: Yeah, absolutely. So yeah, reverse logistics really refers to the process of of managing the flow of products and materials that go from the customer back to the seller or manufacturer, or we’re used to the logistics right, of products going from the manufacturer to the consumer. But just play that in rewind. And that’s really what reverse logistics is all about. So it’s with, you know, some of the activities that would be involved in reverse logistics would be transportation, it’s returns of of products. You know, repairs and refurbishment could be included. It’s same with recycling and disposition. And so what’s interesting is that I think most people aren’t aware of how enormous this industry is. If you look globally, I think the reverse logistics industry for all products is approaching close to $1 trillion dollars
Kurt: Oh, wow.
Dan: And yeah, it’s it’s enormous. And in the US the US is maybe it’s closer to about 20% of that. It’s I mean maybe a little less. I’ve seen statistics where it’s maybe $150 billion to $180 billion a year. The components that I focus on are on the electronics side. That’s a that’s a subsection of the total reverse logistics market that’s closer to, you know, anywhere from 20 to 30 billion a year. But you can just see the magnitude of that when these manufacturers are tasked with getting returns and equipment back to them after they’ve already sold them to, to customers.
Kurt: Okay, great. another term that I think it’s important for our listeners to understand is RMA I think I first learned about this term, all the way back when I worked at, NetApp in the early 2000’s I know that, eBay, excuse me, that, Securus has a, thriving eBay, store where we actually remarket, equipment on behalf of our customers. So I know that this is occasionally, but not often. based on what I’m looking in terms of our satisfaction rating, part of our process. But what is the term RMA mean
Dan: Yeah, sure, and it’s funny you mentioned this, Kurt, because I was just meeting with one of our clients a couple days ago, a municipality, and he was talking about, the RMA policy of one of his vendors. So what RMA stands for is return material authorization. And the way to think about this, it’s basically the process of where a manufacturer or a supplier, grants the customer the right to return a product for a refund or maybe a replacement or even a repair. You know, you typically see this when there’s a defect with the product, whether it’s, you know, and a lot of times these are covered by the warranty, of the vendor. So it’s basically another way to think of it. It’s basically a permission slip for a customer to return, return their product.
Kurt: Perfect. That’s that’s helpful. So now I know what, reverse logistics is. I understand the circular economy and RMA, Dan, help me understand. you know, we’re going to talk about contract manufacturers, but why might one of these OEMs outsource this process of reverse logistics?
Dan: Yeah. So so we see a lot of this in our industry where OEMs are experts, a lot of times at designing their products, whether that’s that’s computers or other electronic devices. They’re experts at the design. A lot of times they’re experts at the the supply chain management of it, but where they’re not as, as well versed is just the idiosyncrasies of the reverse logistics game. And, on the surface, it may look simple. you just need to get the equipment back to the manufacturer. But a lot of times there’s a lot of, operational complexities involved here. You’re not sure how the equipment, what what state it’s going to be when it’s returned. if you’re looking to do repairs, it’s a whole. It’s really a different business. And so with a lot of these OEMs elect to do is they’re they want to be the best at the design and the supply chain management. but they want to outsource the core competencies of the reverse logistics game, because that’s just really not who they are, and that’s not what they do. And there’s going to be others who are more efficient and and more cost effective at doing it.
Kurt: So, okay, so, give me an idea. And who are some of those companies? I know that Securis has worked with a number of them. You worked with, some of them personally, what are some examples of companies, you know, if I want to start, you know, Kurt’s Computer tomorrow, right? Maybe, maybe I would hire you. And we’re probably not going to do our own delivery. So we just assume, can we, if we talk to, if we want to hire somebody to help us out.
Dan: Yeah. So so probably some of the most prominent names in the reverse logistics space are companies that a lot of us have heard of. Right. The Fedex’s, the UPS’s, you know, DHL is a pretty popular one, but those that may not be quite as as popular, that you have companies like Flex, they do a lot in this space. There’s GXO that’s a reputable reverse logistics company. And then there’s Reconnect. Which is also one where, again, a lot of them are involved in helping these OEMs get equipment back. And then sometimes they’ll even add more value by doing some of the work. when it comes to refurbishing or repurposing some of the equipment and returns as well.
Kurt: Okay. great. That’s that’s super helpful. So here’s something that might just surprise some of our listeners. I come to find out that sometimes inspection, sorting, repackaging, you know, testing and then trying to resell that equipment that came back in the RMA process, it’s actually way more expensive than, re remanufacturing. So, why is that Dan? Do you have any any guesses based on your expertise in the industry?
Dan: Yeah. You know, it’s interesting, I, I like to think of it this way. So if you’re if you’re talking about remanufacturing, I mean picture a warehouse where, you know, you have equipment being assembled and it’s usually it’s very easy to manage because it’s it’s streamlined. It’s standardized. They, you know, engineers get paid to just make that process so much more efficient, whether there’s all types of techniques. Right. There’s Six Sigma and and all those ways of making that manufacturing really efficient. And so when it comes to remanufacturing, you’re able to benefit from some of those streamlined processes. And that standardization. But but when it comes to inspections and repackaging and really kind of more and the reverse logistics side of it, it’s not as streamlined. It’s a lot of times the returns, they may be in extremely different condition than when you first sent them. Sent them out. And and some of them may need a unique type of repair that’s, that’s different from from the others being returned. So you really need that individualized attention. And so that that makes for higher costs and, and more difficulties.
And the other thing is, you know, there’s there’s an infrastructure component to this as well, because as you’re getting all these returns, you have to store these returns somewhere. You need warehouse space. You need workstations to to work and operate on the equipment. And so that makes it challenging to in addition, you know, it gets very hard because a lot of times you’ll have these unpredictable volumes. You’re you’ll be getting returns. But it’s very hard to predict at which rate. And that makes it hard for managers to manage through that, that, that process. So that’s why a lot of these OEMs, it’s in their best interest to outsource some of this work because, it’s just easier for them. It’s more cost effective. And then in addition, they don’t have to train the staff. There’s a lot of training that goes in to out to to the companies that are repurposing and sorting and repackaging. So so those are costs that they can shed when they when they outsource it.
Kurt: Yeah. I mean, I think the other thing we should probably talk about is most of these OEMs actually outsource their manufacturing and they outsource it to companies that are incredibly good at manufacturing. They are highly automated. there may be a scenario where they manufacture equipment for multiple different product lines, multiple different companies, and they may have a factory that, you know, two weeks out of the month is manufacturing in one line and then switches to, to another line. But I think because of that high degree of automation, they’re able to manufacture things really cheaply. And then when you compare that to things that come back from RMA and are typically one offs, there’s a lot of human element with the inspection, the testing, kind of one off manual repairs and it becomes difficult to to match that. And so, you know, what I found is that for lower value items, maybe like computer peripherals, it may make more sense to completely break down and recycle that and then manufacture. That is new, from a cost perspective versus trying to, you know, repair individual items. or maybe you’re talking about something that’s super expensive, like a storage array or maybe a high end server. that might be a little different. but, you know, some of these, you know, some of these lower end things, I think it’s it’s cheaper to manufacturers. So, talk to me, Dan, about this whole outsourcing industry known as, contract electronics manufacturers. Can you give me some examples of what you’re seeing in the electronics industry of that?
Dan: Yeah, absolutely. So you’re dead on Kurt in that a lot of companies are starting to outsource their manufacturing. I can think of a couple of examples. the big one is Apple. you know, they design their equipment typically in California, but a lot of it is, manufactured, over in China. I know that’s switching, you know, to India and I know Trump has, you know, I think reprimanded Apple for that but but yeah, you see this with some of the, the OEMs and on the networking side and server side as well. They’re using companies like, you know, Jabil and Flextronics and interesting, you know, Foxconn, which originally was working with Apple quite a bit on their phones and still are, but they are doing a lot of server manufacturing now for some of the hyperscalers out there. we’re also seeing companies like Nutanix now. They’re using Supermicro to manufacture and support some of the branded servers and so, yeah, I mean, an interesting case study too, is just to look at, Taiwan’s the Taiwan Semiconductor Company. I mean, that’s how they started. And just really ate the lunch of Intel because all of these designers for the chips was completely outsourced to Taiwan Semiconductor. And now Taiwan Semiconductor is, you know, it’s it’s I think it’s over $1 trillion business now. So, yeah, a lot of times it makes sense to to outsource this because the manufacturers just can benefit from economies of scale and expertise and, and different, different process improvements that, you know, sometimes it’s harder to be able to do the design all the way through the whole product lifecycle and stack, as well as if that piece of it is outsourced.
Kurt: So, yeah, no, thank you for that, Dan. So let’s maybe change gears a little bit. obviously OEMs are trying to, you know, be innovative. They’re trying to sell more of their products to consumers. Obviously AI with everything is super hot. Right? So these OEMs are trying to balance their need, you know, for innovation with the circular economy. goals. I mean, you know, I’m working with many customers today that are in the process of replacing all of their laptops and desktops because the older ones don’t support, Windows 11 and some of the new AI stacks are out there. So talk to me, Dan. What’s what’s the balancing act between innovation and the circular economy? Because sometimes they can be a little bit at odds with each other, right?
Dan: yeah. I agree with that. I mean, there is a real tension there, you know, between the product companies, you know, they’re incentivized to churn out new products and innovate. And, you know, just just look at Apple, right? It’s I mean, the wave of revenue that’s driven each time a new phone comes out, you know, and that and that does that conflicts with some of the sustainability expectations that clients may have, because, you know, what is going to happen to those old phones? Are they going to end up, you know, a lot of times there may be, whether it’s phones or in other electronics, there could be hazardous materials. And, so what is that going to do for the environment? So it’s interesting, you know, the best companies, I think they’re taking that to heart. And they realize that the consumer these days, they do care about, the environment and, and sustainability.
And so, the best companies that I’m seeing, I don’t think that they’re necessarily forced between choosing innovation or circularity. They’re they’re doing what, you know, Jim Collins talks So he talks about in his books, you know, Built to Last and Good to Great. He talks about the tyranny of the or and and the great companies are taken of you to the. And they want to be both innovative and focused on the sustainability. And so a lot of times when these OEMs, if they are designing the product with the end in mind, I think of, as Steve Covey said, begin with the end of mind. If they’re thinking about what will happen at the end of the lifecycle, are the materials made from more recyclable materials? Is it easier to recycle at the end? Is it easier to repair at the end? I’m seeing a trend towards that, and I think ultimately that can be a great thing. But you’re right there. In the past, there’s been that natural tension between spitting out new products and the sustainability. But we’re starting to see some some more awareness on the OEM side with that. But we’re starting to see some some more awareness on the OEM side with that.
Kurt: Yeah. I mean, I know HP’s got some investment there. I think there are some models with less plastic with easier to recycle plastic, maybe a little bit more aluminum and metals versus, plastics. So I’m definitely seeing, something there. So when we were talking about iPhones, I mean, I personally was part of a class action lawsuit where, this goes back a few years where, Apple was accused of, purposely making, iPhones obsolete and the very short lifespan. So I think that’s gotten consumers interested. You know, you talked about the environmental, impact, but there’s also potentially a cybersecurity impact. of these upgrades and end of life, equipment, you know, on our, you know, on our website, you know, Securis.com, we do have a, article that talks, you know, answers the question whether or not doing a factory reset on your phone, protects your data, but what types of products, then do you require data sanitization? before recycling?
Dan: Sure. Yeah. So, yeah, I would say in terms of what products required to do sanitization, I really lump that into two categories. There’s there’s your traditional IT assets that we’re all familiar with right. There’s your your desktop computers and your laptop computers and your phones and your servers. and those types of devices. And what’s interesting about that, that segment is that, you know, that that has evolved in terms of the difficulty with which, you know, the resources and difficulty in terms of data destruction and sanitization. I think back, I think it was basically, you know, back in the mainframe era where, you know, you had these huge, huge rooms just and that was basically the mainframe. And while maybe physically, it was a lot harder to destroy it because it’s so big, you knew where it was, you knew how to secure it.
But now with, you know, the form factor getting so small where terabytes of data can be on basically a chip the size of your thumb, you can just imagine for IT directors and CIOs and security officers, just that challenge of now managing all that data that could be all over the place. And so, you know, that’s the again, one segment is the traditional it’s that’s that’s again becoming harder to manage given, you know, the different form factors. But then the second set of items that really require data santization is, has really exploded ever since the Internet of Things took off. And so there’s a lot more consumer devices that you see that require disposition securely. You know, a couple that come to mind would be, you know, the health monitoring wearables or smart home devices, even think of automobiles. Now, you know, 40 years ago, I don’t know if there were any computer. I don’t think there were any computers in cars, now, I mean, it’s basically a car is, a rolling computer. So you’re seeing that even with, you know, consumer appliances, even some children’s toys there, there’s data being collected and about usage and streaming back to the internet. And so those are some of the things. Now, you know, the smartwatches and smart rings even can contain financial data. All those types of devices, are in that second segment that, you know, consumers really need to pay attention to in terms of proper sanitization.
Kurt: So, yeah, I mean, I think I saw a product announcement recently and that might not be wrong. Exactly right. But I think it was, Pure Storage has over a 41 terabyte individual drive now. Wow. Yeah. Which is pretty crazy. yeah. You know, you you also, brought up, wearables. That’s not something that I consider that a security concern until recently. I know at Securis one of the pieces of software that we used to make sure that all data is removed from things like, computers and servers and phones. is a company called, Blancco which, is software that we have found to be, really great and do a good job. It helps us with our workflows and gets all the data off. But there’s a gentleman that left Blancco recently, and maybe I’ll provide a link to this, in, in the show notes or the transcript, but he actually, now has a company that removes data from smartwatches. So we haven’t got a ton of them. yet at Securis. but I expect that we will. And if we get a scenario where customers are asking us to give them value or re-market those or reuse those, I think that’s something that’s going to eventually come up for us.
Dan: Yeah. No, that’s that’s interesting. you bring that up and I’m probably the most dramatic case I recall of the importance of securing the data on the smartwatches. This happened a couple of years ago. There were Marines who were stationed at a basically an undersea closed military base overseas in Syria, and they would do their their morning jogs and running around. They’d run around the perimeter of the base and things, and that data was getting streamed onto an app. And then it was just being published on the internet. And so it just tells you you’ve you’ve really got to think through these devices, not only the data that’s stored on them, but the risk it can put, various organizations if they’re not controlling it carefully.
Kurt: Awesome. All right, now switch gears again one more time. so we talked about data sanitization and why that’s important for both consumers and companies and even the US military. But some products really don’t contain their data bearing devices. And so they’re not going to require sanitation. But, I’ve learned that the OEMs might, want those, destroyed even I think Securis has experience with, a brand that manufactures speakers and headsets that I really like to use. Why would a company like that say, hey, I want these devices destroyed?
Dan: Yeah. So again, if you take away the data piece of it, I can think of a couple other reasons that manufacturers and OEMs would still want their their products destroyed. So the the first reason is brand protection. So if you have, if an OEM has a product that’s either defective or outdated, they want to make sure that those quality standards are kept extremely high. So they’re going to want to make sure that that product doesn’t get re-released out onto the market. So I can see them really as a way of brand protection. We see that often where, OEMs need destruction provided. The other other idea is limited liability. So if, if a product is defective or it’s if it’s recalled and maybe it has, you know, there’s potential for it to be, do harm, you know, it’s important that that gets taken off the market and destroyed.
I can think of a lot of times you may see, a battery that has either, you know, we call them bulging batteries. If there’s, you know, hazardous materials. The OEM doesn’t want their name associated with any risk to the consumer. If there’s there’s been some issue with with the product. The other the other reason that OEMs, you know, would want to products destroyed again, if you take out the data piece of it is just from, regulatory compliance perspective. Again, if if there are if the goods have expired a lot of times failure to sometimes manage and and and remove those items properly can can result in regulatory penalties.
And then lastly, just from, you know, if, if a product becomes obsolete or outdated, a lot of times, you know, the the OEM wants to make sure that they’re managing demand for their most recent product. And so if you have some of these older generation products, if they can remove those from the marketplace, that’s going to ideally drive more demand for their latest generation products. And so those are just some of some of the reasons that we see OEMs who, you know, want to make sure that their legacy products are destroyed properly in a in an environmental way, as well.
Kurt: Awesome, great. So we’re going to continue in the trend we’ve talked about OEM’s and you know what they outsource. And you know, specialization of different different vendors. And so we talked about OEM’s outsourcing manufacturing. We talked about them outsourcing reverse logistics. So either of those reverse logistics companies or their OEMs, many times they outsource, you know, this recycling or end of life destruction process to somebody called an IT asset disposition. company people like Securis. We do that for a number of OEMs. what kind of services are they looking for and why were they outsourced versus just trying to do that themselves?
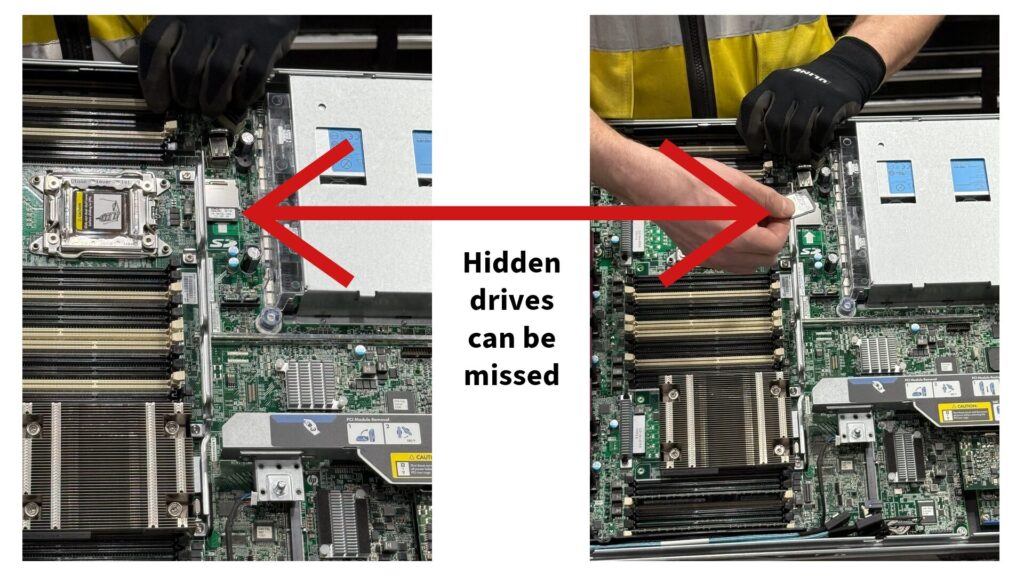
Dan: You know, so a lot of times you’ll see OEMs or reverse logistics companies even, they’ll outsource the very end piece of the the product lifecycle, to a company like an IT asset disposition company, a company like Securis because there’s, there’s, you know, a couple couple components to it. First is just from the data security perspective. We talked about that. There’s depending on the type of device or the way the media is stored, you really do have to be an expert in it to make sure that the data is destroyed properly. And so you know what’s interesting. And, you know, especially like I’m thinking some of these laptops these days and, you know, these, these small solid state drives that are included in them, you know, there are there are it’s almost like, you have to be a forensic, expert to be able to look through all these.
There’s almost like there’s little hidden component or compartments in the laptops that if you’re not just very, very careful and an expert in it, we’ve seen many cases where a small, small, solid state drive can slip through the cracks. So it’s that’s one reason OEMs know that they’re not necessarily the experts in reverse logistics companies know they’re not experts. But there are companies out there that are experts like the ITAD providers. And so that’s that’s that’s a reason that they want to tap into that expertise. that’s more on the data security side. on the environmental side too, a lot of the the best ITAD companies, have to have certain environmental certifications. The most prominent, is one called R2, r2, and it’s R2v3 is where it’s the third version out right now.
And they are doing, The organization that runs that is called SERI, and they are auditing ITAD companies to make sure that they’re complying with all the different regular environmental regulations. they’re making sure that the equipment is handled properly, that things aren’t ending up in landfills. They’re also making sure they’re auditing all the downstream potential vendors of the ITAD companies, too. So it’s a it’s a big deal. And that gives the OEMs a lot of comfort. And it goes again, it goes back to brand protection that the marketplace will see that they’re handling things appropriately. and then lastly, just there’s there’s a value recovery component to this. So a lot of times the ITAD companies, they’re they’re experts at maximizing the value of whether it’s, if they have permission to resell the equipment as is and refurbish it, or whether it’s just the broken down raw materials.
They they specialize in this. And a lot of times that they’re driving that value and then they’re giving some of that sometimes back to to the companies that they service. And so those are just a couple of the reasons that you’d see these OEMs and reverse logistics companies want to engage in ITAD And, you know, again, it comes down to that expertise protecting from the data security side and then also the environmental side and and the value recovery of it. So yeah.
Kurt: So Dan, you mostly have answered my my next and close to last question. Appreciate you bearing with me, through this learning session here. so obviously, you know, you mentioned R2, you mentioned, NAID AAA, which is a security, designation I had previously mentioned, you know, your individual certification and what, you have – a certified secure data destruction, specialist. but, I guess, you know, I’ve been told that one another reason that, these various logistics companies, other than the ones you’ve stated so far, looking to, to outsource, the the recycling or the data destruction to an ITAD company is because the, the, the OEM that they’re contracted with is looking for a legal document known as a certificate of destruction. so that’s an example of one type of reporting or auditing. But what other types of reporting or auditing might the OEM require? from both the ITAD and, you know, if it’s, you know, subcontracting relationship, but with the reverse logistics company, what are they looking for typically?
Dan: yeah, so it’s it’s interesting because it’s one thing to actually recycle the equipment or destroy the equipment that the OEM or reverse logistics company provides, but it’s another to prove that it was destroyed or recycled. And so a lot of these companies do get audited. And so it’s important that they have that evidence. So some of the, the, the methods that we’ve seen or some of the deliverables are anything from serial number capture. So a lot of times a company, may want to just see basically a list of all the serial numbers or even an asset tag of all the devices that have been recycled, and that can come in the form of a, an Excel file or a CSV file, something like that. We’ve also seen just weight reporting.
There’s some cases where they want to see the actual weight, because a lot of times they’re tracking for their sustainability goals, the the pounds of equipment that they have recycled. We’ve also seen cases where they’ll want to see photo evidence. So whether it’s we’re capturing with a photo the device right before it was destroyed or a picture of it afterwards. And then this comes also in the forms of, of inventory reports. And as you mentioned, that certificate of destruction and recycling. And so one thing that we found also really helpful is if a client is getting audited and they need to refer back, say, to a specific individual item that we’ve developed. And other companies in our industry have developed portals where they can go online, log into their the portal, and basically search for an individual asset by serial number or, or asset tag. And it saves them a ton of time.
I’ve, I’ve seen companies, God bless them where, you know, they were recording all of these items on a, on an Excel spreadsheet. And, you know, it was basically a 50,000 line spreadsheet. And so you can imagine the time it takes. Whereas now with, portals that we have, you can just type into the search bar and quickly pull up an asset and prove that it’s been dispositioned properly
Kurt: Microsoft Excel Dan, the most used database in the world. 1000 items starts to be a lot. last question. Thank you so much. So, there may be some OEMs or, reverse logistics companies listening to this and, wanting to reach out to Securis, but curious about our experience and our, our past performance. can you, can you share a couple that that might be relevant without, you know, providing any information that would be subject to non-disclosure?
Dan: Yeah. Yeah, absolutely. So yeah, outside, you know, traditional electronics companies that we work with, we work with companies that produce audio peripherals. So speakers and headsets and those types of products, we also work with companies that produces produce alarms. So they’re they’re producing the alarm systems at buildings and homes. And they need that those eventually to be dispositioned and destroyed and recycled properly. And then also, you know, here’s a neat one. Drone manufacturers. So they’re producing drones. And once they’ve reached their end of life, those need to be destroyed properly. So those are just some of the the OEM types of OEMs we work with, among others as well.
Kurt: Yeah, I mean, I know, Securis does a lot of work with the, the US, DoD and defense, industrial base and, and I, I think the term Dan is called de-militarization, at the, at the end of life, what I’ve learned is in some cases, you know, there’s these items, they might be concerned that there’s classified data on them. in other cases, they’re more concerned about, enemies of the United States trying to copy, whether it’s a radar system or a weapons system or the drone, technology. So many of those companies have reached out to us for kind of a use case. We haven’t talked about it yet, but really just that, demilitarization. use case. But, yeah.I really appreciate you joining. tons of insights, about electronics OEMs and and how they’re investing in the circular economy.
Dan: thank you so much. And have a wonderful day. All right. Thanks so much for having me. I appreciate it.
BIOS:
Dan Mattock is a VP with Securis and has been with the company for 15 years. He is a CSDS (Certified Secure Data Destruction Specialist) and LEED (Leadership in Energy and Environmental Design) Certified. He has served as the president of the Northern Virginia Chapter of the National Property Managers Association. He has consulted with some of our largest customers on the topics of data security, the circular economy, and IT Asset Disposition best practices.
Learn more about how Securis ITAD Services – Contact Us today!


 Decommissioning begins at the planning table long before a single asset is unplugged or wheeled out the door.
Decommissioning begins at the planning table long before a single asset is unplugged or wheeled out the door.  By the time your racks are empty and devices are staged for removal, the most visible parts of decommissioning may feel complete. But the real risk often lies inside the devices you can no longer see—in residual data
By the time your racks are empty and devices are staged for removal, the most visible parts of decommissioning may feel complete. But the real risk often lies inside the devices you can no longer see—in residual data 
 This phase is about more than maximizing financial return. It’s about making the most of what you already own. That might mean reselling equipment with market value, redeploying it within your organization, or donating it to support social impact and ESG goals. The key is knowing
This phase is about more than maximizing financial return. It’s about making the most of what you already own. That might mean reselling equipment with market value, redeploying it within your organization, or donating it to support social impact and ESG goals. The key is knowing 
 When reuse, resale, or donation aren’t viable, responsible recycling becomes the final—and critical—step.
When reuse, resale, or donation aren’t viable, responsible recycling becomes the final—and critical—step.
 Your ITAD partner should provide
Your ITAD partner should provide 
 Retiring end-of-life laptops, desktops, or servers? Your two priorities are clear: protect sensitive data and recover maximum value from those assets.
Retiring end-of-life laptops, desktops, or servers? Your two priorities are clear: protect sensitive data and recover maximum value from those assets. mply deleting files or reformatting a hard drive leaves your data exposed. At Securis, we go further, with verified software-based data wiping that sets the stage for
mply deleting files or reformatting a hard drive leaves your data exposed. At Securis, we go further, with verified software-based data wiping that sets the stage for

 Every IT department has that moment: a stack of laptops being phased out, a row of decommissioned servers waiting in the data center, or a closet full of outdated desktops collecting dust.
Every IT department has that moment: a stack of laptops being phased out, a row of decommissioned servers waiting in the data center, or a closet full of outdated desktops collecting dust.  What if your retired IT assets could offset the cost of your next refresh, without compromising data security?
What if your retired IT assets could offset the cost of your next refresh, without compromising data security? Secure IT asset value recovery doesn’t just protect budgets—it supports
Secure IT asset value recovery doesn’t just protect budgets—it supports  You can cut costs and increase returns with a few smart moves:
You can cut costs and increase returns with a few smart moves:
 Here’s how Securis partners with companies navigating M&A to mitigate data security risks:
Here’s how Securis partners with companies navigating M&A to mitigate data security risks:

 Why Degaussing Is Still Relevant
Why Degaussing Is Still Relevant Securis
Securis 
 1. Secure Data Destruction Is Non-Negotiable when Decommissioning a Data Center
1. Secure Data Destruction Is Non-Negotiable when Decommissioning a Data Center Significant fines
Significant fines
 Even the most technically sound projects can falter without realistic timelines. Data center decommissioning is resource-intensive, often requiring:
Even the most technically sound projects can falter without realistic timelines. Data center decommissioning is resource-intensive, often requiring:




 Sarbanes-Oxley Act (SOX)
Sarbanes-Oxley Act (SOX) Federal Financial Institutions Examination Council (FFIEC) Guidelines
Federal Financial Institutions Examination Council (FFIEC) Guidelines