Finding the top IT Asset Disposition (ITAD) companies can be challenging. This regularly updated list has been designed to help you identify the best options for your company based on some key factors. First, we discuss the factors to consider when choosing your ITAD partner, and we have a longer blog on that subject here. Then, we will provide a list of ITAD providers that you can choose from to find the best partner to meet your organization’s specific IT asset disposition needs. When making your final decision, consider scheduling consultations with multiple providers to assess their specific offerings and how well they align with your organization’s priorities regarding data security, environmental impact, and cost.
What is ITAD?
ITAD is short-term for IT Asset disposition. ITAD is the process every company must go through when refreshing IT Assets such as computers, tablets, smartphones, and storage devices. Because these devices often contain sensitive information and environmentally hazardous materials, disposal of end-of-life electronics is not as simple as throwing them in the trash. ITAD vendors should bring Security, Accuracy, and Sustainability to your IT asset disposition process. Here are some questions to ask as you are assessing your various options:
Security
When selecting an ITAD vendor, security should be a top priority. A reputable vendor should provide comprehensive security measures addressing every aspect of the asset disposition process. This begins with a thorough evaluation of end-of-life equipment to inform decision-making about which data erasure and/or destruction methods should be employed and should extend to considerations such as transportation and logistics.
Certifications such as ISO-9001:2015, ISO 14001:1015, ISO 45001:2018, and NAID AAA certification for mobile and plant-based facilities can also inform an ITAD vendor’s commitment to data security. Compliance with industry-specific regulations is also important. You should be aware of data destruction-related regulations specific to your industry, such as HIPAA, HITECH, or Gramm-Leach Bliley, CMMC, etc and be sure that your ITAD vendor complies with them.

The vendor should also be open to arranging site visits, talking with their references, and allowing you to assess their logistic and security requirements firsthand. Employee screening is another critical aspect of security. A trustworthy vendor will conduct thorough background checks on their employees, including fingerprinting and drug testing, and provide ongoing, intensive security training. These measures help ensure that reliable, well-trained professionals handle your sensitive data and assets throughout the disposition process.
Accuracy
A reputable ITAD vendor should provide comprehensive and accurate reporting on all processed assets. This includes maintaining a detailed audit trail that tracks each asset from when it enters its custody until its final disposition. While the industry average accuracy in ITAD reporting is 85%, you should look for a vendor who can exceed this number and provide highly accurate reporting, ideally with greater than 99% precision. To ensure the utmost accuracy in data capture, the vendor should implement a two-step verification process for all captured data, minimizing the risk of errors or discrepancies. After the asset disposition process, the vendor should furnish a certificate of destruction. This document is official proof that the assets have been properly disposed of and that any data contained within has been securely destroyed.
In addition to basic asset tracking, a top-tier IT asset disposition vendor will go above and beyond by providing weight and LEED (Leadership in Energy and Environmental Design) reporting. This information is valuable for organizations looking to quantify their environmental impact and potentially earn credits for sustainable practices.

Finally, the vendor should offer a client portal to empower clients with full visibility into their asset disposition process. This portal should provide unlimited access to inventory reporting, allowing clients to review asset status, track progress, and generate reports as needed. Such a feature demonstrates the vendor’s commitment to transparency and client empowerment while streamlining their customers’ asset management process.
Sustainability
When selecting an ITAD vendor, it’s crucial to prioritize sustainability and environmental responsibility. The ideal ITAD partner should prioritize sustainability through a two-pronged approach. First, they should focus on extending the life of IT assets through refurbishment and reuse whenever possible. This approach not only benefits the environment by extending the lifecycle of IT equipment and contributing to a circular economy but also provides financial advantages to your company. Second, for assets that cannot be reused, the vendor should employ environmentally friendly disposal methods that minimize the impact on ecosystems.
A reputable vendor should hold certifications such as R2v3, which ensure adherence to responsible recycling practices and environmental standards. These certifications have rigorous requirements, demonstrate the vendor’s commitment to sustainable ITAD processes, and assure that they follow industry best practices. R2V3 certification ensures comprehensive environmental compliance, including agreements with all downstream vendors to dispose of sensitive materials properly and prevent environmental harm in vulnerable regions due to unethical e-waste recycling practices.

Additional considerations
In addition to security, accuracy, and sustainability, other considerations exist when choosing your ITAD vendor. A quality vendor should be able to handle your specific asset types and volumes and have the logistics and transportation capabilities to support your needs. This includes scaling services up or down based on your requirements and tailoring their offerings to your unique situation.
End-to-end services are also important, so you only have to vet one vendor who can then handle everything from logistics and data destruction to remarketing and recycling. The vendor should offer on-site and off-site data destruction options, ideally with NAID AAA-certified mobile trucks and facilities. Convenient collection services are also important, whether through scheduled pick-ups, accessible drop-off locations, or mail-in options.
Flexibility is key when it comes to contracts and equipment. Be wary of vendors that lock you into long-term contracts. An established reputation for excellent service and reliability is also critical. Look for solid testimonials from clients in similar industries to gauge the vendor’s track record. Finally, responsive customer support can significantly improve your ITAD experience. A dedicated project manager can ensure that any issues or questions are addressed promptly, helping to streamline the entire ITAD process and provide peace of mind.
Securis
Securis provides secure, accurate, sustainable, certified, and compliant on-site and off-site data sanitization and IT asset disposal and recycling for PCs, laptops, hard drives, solid-state drives, smartphones, servers, and other e-waste using NSA-approved degaussing and drive shredding technology and NIST 800-88 compliant drive wiping. Many Securis customers are in highly regulated industries such as government, healthcare, and financial services. In response, Securis has spent more than 20 years developing best practices for destroying classified and highly sensitive data. Securis holds certifications for ISO 9001, ISO 14001, and ISO 45001, as well as a NAID AAA (i-sigma) certification. In addition, Securis is certified by the DLA (Defense Logistics Information Service) to store and transport military critical technical data and by the Department of Transportation to transport e-waste materials. Securis also complies with relevant regulations, such as HIPAA, HITECH, OSHA, Gramm-Leach Bliley, FERPA, and many more. Securis is also R2V3 certified to responsibly remarket or recycle every component in your retired electronic devices, ensuring e-waste stays out of landfills and your ESG rating is increased. Securis also has a Certified Secure Destruction Specialist® (CSDS®) on staff, so you can be sure that regulatory compliance, information security, and risk management protocols are always top-tier.
Securis provides a thorough chain of custody and a transparent and well-documented process for your IT asset disposition projects, culminating in a certificate of destruction, all readily accessible to you 24/7 from their Client Portal. Inventory reports have been demonstrated to be greater than 99% accurate. Securis’ value recovery program assures the best possible return for any residual value in your end-of-life IT assets. Securis has more than 50 five-star reviews on Google and positive reviews on Gartner. Securis provides services throughout the continental U.S.
At a Glance:
- Company Type: Private
- Year Founded: 2000
- Website: https://securis.com/
- Headquarters Location: Virginia, USA
- No. of Employees: 51-200
- Reviews: As of March, 2025, Securis has an Overall Rating of 5 out of 5 in the IT Asset Disposition market, based on 6 reviews on Gartner Peer Insights™, Trustpilot – No Reviews Google: 4.8 out of 5 based on 82 reviews
Bottom Line: Securis is the best overall choice for companies looking for secure, accurate, and sustainable ITAD services. Securis offers military-grade certifications, ESG reporting, and flexible nationwide IT asset disposition services.
Iron Mountain
Iron Mountain is best known for its records management capabilities, which historically have been paper and tape storage, backup, and recovery services. They are one of the largest companies in the United States and have a recognizable brand name globally. Iron Mountain entered the ITAD business in 2021 by acquiring IT Renew, based in Newark, California. In November 2023, Iron Mountain completed the acquisition of Regency Technologies, expanding its presence in the IT asset disposition market. In September 2024, Iron Mountain also acquired Wisetek, adding to its portfolio of ITAD acquisitions.
Iron Mountain now provides IT Asset Disposition services as part of its broader IT Asset Lifecycle Management (ALM) offerings, which include data destruction, asset remarketing, e-waste recycling, and comprehensive reporting.
At a Glance:
- Company Type: Public
- Year Founded: 1936
- Website: http://www.ironmountain.com
- Headquarters Location: Boston, USA
- No. of Employees: 10001+
- Reviews: As of March 2025, Iron Mountain has an Overall Rating of 3.7 out of 5 in the IT Asset Disposition market, based on 2 reviews on Gartner Peer Insights™, Trustpilot – 1.3 based on 90 reviews. Google: none found
Bottom Line: Iron Mountain offers a comprehensive set of services but may not be best of breed for all of them. Companies are likely to choose them for ITAD services, with an existing procurement relationship is a key factor.
HOBI International Inc
HOBI International, Inc. provides IT asset disposition and managed mobile services. The company specializes in sustainable solutions for managing and disposing of global IT and mobile assets for businesses. HOBI’s services include data security and erasure, mobility managed services, reverse logistics, data center services, enterprise asset services, and environmental services, with systems designed to maximize a client’s return on obsolete assets while minimizing processing costs. Hobi processes more than 1 million individual assets annually across its three facilities in Dallas, Phoenix, and its original location in Batavia, Illinois.
HOBI also offers a custom-designed data management system with concise reporting on logistics, costs, asset serialization and configuration, redeployment schedules, sales history, and scrap summaries.
At a Glance:
- Company Type: Private
- Year Founded: 1992
- Website: https://hobi.com/
- Head Office Location: Batavia, Illinois, United States
- Reviews: As of March 2025, HOBI has not been rated on Gartner Peer Insights™, 1.0 based on 1 review on Yelp No others reviews found
Bottom Line: HOBI maintains R2v3, RIOS, and ISO 14002 certifications and is a WBE-certified company but does not have a NAID-certified facility.
DELL
Dell offers end-to-end device lifecycle management, including inventory tracking, equipment repair/replacement, upgrades, and responsible disposition. This can simplify IT asset management for companies with large, dispersed workforces. Dell manages the entire IT asset disposition process, including pickup logistics for any leased or owned hardware brand, secure data wiping following NIST SP 800-88 R1 standards, device resale or recycling, and online tracking through Dell’s TechDirect portal. Dell has a strong focus on sustainability and circular economy principles. They aim to recycle or reuse an equivalent product for every product a customer buys.
Dell has expanded its Asset Recovery Services to 35 countries outside the U.S., covering Canada, Europe, the Middle East, Africa, and Asia. This makes Dell a viable option for multinational corporations. While Dell can handle multi-vendor assets, its ITAD services encourage the continued use of Dell products, potentially limiting flexibility in IT procurement decisions. While Dell offers some flexibility, its services may not be as customizable as those of specialized ITAD providers. In addition, Dell uses third-party partners for some aspects of disposition.
At a Glance:
- Company Type: Public
- Year Founded: 1984
- Website:https://www.dell.com
- Headquarters Location: Round Rock, Texas, USA
- No. of Employees: Approximately 120,000
- Reviews: As of March 2025, Dell has an Overall Rating of 5 out of 5 in the IT Asset Disposition market, based on 1 review on Gartner Peer Insights™, Trustpilot – 1.4 based on 303 reviews. Google: none found
Bottom Line: Customers who are exclusive users of Dell servers, storage, and laptops are most likely to consider using them for ITAD services.
Ingram Micro
 Ingram Micro is an American distributor of information technology products and services. In February 2016, it was acquired by Chinese conglomerate HNA Group. In May 2018, it acquired CloudBlue, which offers cloud commerce services. Ingram Micro’s approach to ITAD is comprehensive and focused on risk management, logistics, asset repair, and refurbishment, and maximizing residual asset value.
Ingram Micro is an American distributor of information technology products and services. In February 2016, it was acquired by Chinese conglomerate HNA Group. In May 2018, it acquired CloudBlue, which offers cloud commerce services. Ingram Micro’s approach to ITAD is comprehensive and focused on risk management, logistics, asset repair, and refurbishment, and maximizing residual asset value.
Ingram Micro offers onsite and offsite data erasure and destruction services, including degaussing and physical shredding. Its industry sectors include enterprise, government, manufacturing, legal, retail, and healthcare. Ingram uses a proprietary system called BlueIQ for global asset tracking and intelligence throughout the ITAD process and also performs re-sales through a platform named RENUGO.
At a Glance:
- Company Type: Private
- Year Founded: 1979
- Website: http://www.ingrammicro.com
- Headquarters Location: Irvine, USA
- No. of Employees: 10001+
- Reviews: As of March 2025, Ingram Micro has an Overall Rating of 5 out of 5 in the IT Asset Disposition market, based on 1 review on Gartner Peer Insights™, Trustpilot – 1.4 based on 144 reviews. Google: none found
Bottom Line: As a large distributor of IT Services, customers have access to Ingram Micro Service through a large network of value-added resellers
HPE
HPE (Hewlett Packard Enterprise) offers comprehensive IT Asset Disposition services as part of its IT asset lifecycle management solutions. HPE prioritizes the reuse of IT assets over recycling, supporting the management of multi-generational environments. This strategy aligns with sustainability goals by extending the life of IT products and reducing environmental impact. HPE provides asset recovery services, including collecting, inventorying, transporting, sorting, and processing IT products for recycling or remarketing.
HPE partners with other ITAD companies to source used HPE computers and to subcontract ITAD services. Devices are processed through HP-approved partners and audited by a third party. If equipment cannot be repurposed, it is responsibly recycled. HPE offers a full suite of IT asset lifecycle management solutions, including the option to purchase pre-owned technology. It also has a large global presence, offering services in multiple countries. However, there are service limitations with HPE, as in many countries, the HP ITAD Service is currently available for direct customers only. In addition, onsite decommissioning services are only available in Australia, Germany, the United Kingdom, and the United States.
At a Glance:
- Company Type: Public
- Year Founded: 2015
- Website: http://hpe.com
- Headquarters Location: Houston, US
- No. of Employees: 10001+
- Reviews: As of March, 2025, HPE has an Overall Rating of 4 out of 5 in the IT Asset Disposition market, based on 1 review on Gartner Peer Insights™, Trustpilot – 1.2 based on 7,793 reviews Google: none found
Bottom Line: HPE is best suited for companies that are committed users of HPE equipment and often reuse HPE equipment for different employees.
ERI
 ERI is one of the largest and most well-known ITAD companies. It claims
ERI is one of the largest and most well-known ITAD companies. It claims
to be the largest fully integrated IT and electronics asset disposition provider in the United States and possibly the world. ERI maintains NAID AAA, R2, and e-stewards certifications. In 2021, it announced an investment by the private equity firm Closed Loop Partners.
ERI uses its partner network to provide services in the U.S. and 46 countries. It offers a full range of ITAD services, including data destruction, asset tracking and reporting, repair and reuse, parts harvesting, recycling, compliance management, and device remarketing. ERI also ensures regulatory compliance and meets or surpasses corporate risk management requirements.
At a Glance:
- Company Type: Private
- Year Founded: 2002
- Website: https://eridirect.com
- Headquarters Location: Fresno, California
- No. of Employees: Approximately 1000
- Reviews: As of March 2025, ERI has not been rated on Gartner Peer Insights™, Trustpilot – no reviews found Google: no reviews found
Bottom Line: Customers looking for an international presence and a fully integrated ITAD supply chain may likely choose ERI.
ER2
ER2 provides IT Asset purchasing, installation, tracking, and disposal services. ER2 operates in Arizona, California, Tennessee, Nebraska, Florida, and Texas but offers worldwide service. ER2 is a private company specializing in technology life cycle solutions, primarily serving Fortune 1000 clients.
The company was founded in 2011 and has shown significant growth since its inception, being recognized as one of the fastest-growing companies in the US for multiple years. ER2 focuses on providing complete IT asset management services, from installation to deployment, while maintaining a commitment to social and environmental responsibility
At a Glance:
- Company Type: Private
- Year Founded: 2011
- Website: https://er2.com
- Headquarters Location: Memphis, Tennessee,
- No. of Employees: 120
- Reviews: Reviews: As of March 2025, ER2 has not been rated on Gartner Peer Insights™, Trustpilot – no reviews found Google: no reviews found
Bottom Line: ER2 is well suited to companies that want to work with one vendor to manage the entire IT lifecycle, from purchasing and installing to disposing of end-of-life equipment.
Dynamic Lifecycle Innovations
 In 2018, Dynamic Recycling changed its name to Dynamic Lifecycle Innovations to reflect a dedication to providing clients with customized, secure, and cost-effective solutions for all stages of the IT lifecycle, including e-recycling, materials recovery, refurbishment, or decommissioning outdated IT assets. Dynamic Lifecycle Innovations is a full-service electronics and materials lifecycle management corporation providing solutions for IT asset disposition, data security, product refurbishment, remarketing and resale, electronics recycling, legislative compliance, metals recovery, and logistics.
In 2018, Dynamic Recycling changed its name to Dynamic Lifecycle Innovations to reflect a dedication to providing clients with customized, secure, and cost-effective solutions for all stages of the IT lifecycle, including e-recycling, materials recovery, refurbishment, or decommissioning outdated IT assets. Dynamic Lifecycle Innovations is a full-service electronics and materials lifecycle management corporation providing solutions for IT asset disposition, data security, product refurbishment, remarketing and resale, electronics recycling, legislative compliance, metals recovery, and logistics.
Dynamic is certified for NAID AAA, R2v3, E-stewards, ISO 9002, ISO 14001, ISO 45001. With physical locations in Onalaska, Wis. and Nashville, Tenn., the company claims to service 100 countries across six continents. Dynamic has a carbon calculator tool that includes details for 30 different categories of e-waste, comprising of both whole units and component parts
At a Glance:
- Company Type: Private
- Year Founded: 2007
- Website: https://thinkdynamic.com/
- No. of Employees: 201-500 employees
- Headquarters Location: Onalaska, Wisconsin
- Reviews: As of March 2025, Dynamic Lifecycle Solutions has not been rated on Gartner Peer Insights™, Trustpilot – no reviews found. Google: 4.3 based on 26 reviews Yelp: 3.0 out of 4 based on 4 reviews
Bottom Line: Best for companies who value extremely detailed ESG reporting.
Cascade Asset Management – (now owned by Sage Sustainable Electronics)

Cascade Asset Management has been acquired by Sage Sustainable Electronics. The combined company will operate under the Sage umbrella but will keep the Cascade name. Over 20 years of experience in the ITAD industry. Cascade specializes in healthcare, finance and insurance, education, government, and technology and was NAID AAA certified, e-stewards certified, ISO 9001 and ISO 14001 certified, and PCI-DSS (Payment Card Industry Data Security Standard) compliant. Cascade brings a secure chain-of-custody process to Sage, and Sage brings a strong set of tools to provide third-party-certified impact reporting to clients, an area in which Cascade has been less active.
Cascade offers a full range of ITAD services, including on-site inventory and data destruction, secure logistics and transportation, asset testing, erasure, and unlocking. It also offers options for asset resale, recycling, donation, redeployment, or return to the company. Cascade has a value recovery program in the form of rebates for assets with residual value.
At a Glance:
- Company Type: Private
- Year Founded: 1999
- Website: https://cascade-assets.com/
- No. of Employees: more than 100
- Headquarters Location: Madison, Wisconsin
- Reviews: As of March 2025, neither Cascade Asset Management nor Sage Sustainable Electronics has not been rated on Gartner Peer Insights™, Trustpilot: No reviews found, Google: No reviews found for Cascade Assets, but Sage Sustainable Electronics received a 3.8 out of 5 from 16 reviews.
Bottom Line: Cascade is a good choice for companies in the Cascades freight zone, which includes Wisconsin, Illinois, Minnesota, Iowa, Indiana, Ohio, Michigan, Kentucky, and Florida. Also, while Cascade is NAID, e-Stewards ISO 9001, and ISO 1400 certified, if your company requires R2v3 certification, this may not be the best choice.
Sims Lifecycle Services
 SLS specializes in managing retired electronic equipment, components, and metals. They primarily cater to businesses, data centers, and manufacturers. The company offers services such as secure and compliant global IT asset disposition (ITAD), e-waste recycling, data center decommissioning, data destruction, and refurbishing, repairing, and restoring materials for continued use.
SLS specializes in managing retired electronic equipment, components, and metals. They primarily cater to businesses, data centers, and manufacturers. The company offers services such as secure and compliant global IT asset disposition (ITAD), e-waste recycling, data center decommissioning, data destruction, and refurbishing, repairing, and restoring materials for continued use.
Sims holds comprehensive certifications and provides online reporting. It operates globally with centers throughout the Americas, Europe, the Middle East, Africa, and Asia-Pacific regions. This extensive network allows it to support multinational companies and large data centers worldwide. The company also emphasizes sustainability, offering tools like a sustainability calculator to help clients quantify carbon emissions avoided through IT asset reuse and recycling.
At a Glance:
- Company Type: Public
- Year Founded: 2002
- Website: https://www.simslifecycle.com/
- No. of Employees: Over 4,000 employees globally
- Headquarters Location: West Chicago, Illinois,
- Reviews: As of March 2025, Sims Lifecycles services has not been rated on Gartner Peer Insights™, Trustpilot: no reviews found. Google: no reviews found, Yelp: 3.6 out of 5 based on 13 reviews
Bottom line: SIMS is a good choice for global companies that need a vendor to participate in all aspects of the IT asset lifecycle, from procurement to maintenance to disposition.
SK tes
SK tes specializes in sustainable technology services throughout the lifecycle of IT assets, including deployment and commissioning of technology devices, IT asset disposition (ITAD), battery recycling, and materials recovery. With facilities in 22 countries, SK tes offers service worldwide. They provide end-to-end lifecycle management for technology assets, from deployment to recycling. The company has developed proprietary processes for recycling and materials recovery, such as its lithium battery recycling technology particularly from electric vehicles.
SK tes places a strong emphasis on sustainability through electronics refurbishment. The SK tes Consumer Solutions division offers data secure refurbishment, repair and remarketing services for consumer returns, trade-in and excess consumer electronics. They also boast a 99% recovery rate for processed materials and have committed to repurpose 1 billion kilograms of assets by 2030.
At a Glance:
- Company Type: Private
- Year Founded: 2005 as TES rebranded in 2024 to SK tes
- Website:https://english.tesgroup.de/
- No. of Employees: Around 1000
- Headquarters Location: Jurong Industrial Estate, Singapore
- Reviews: As of March, 2025, SK tes has not been rated on Gartner Peer Insights™, Trustpilot: No reviews found, Google: No reviews found.
Bottom Line: SK tes is best for global companies that are more focused on reselling retired assets or have large quantities of commodities such as lithium batteries that need to be properly recycled.
DMD Systems IT Asset Disposal Service
 DMD Systems Recovery delivers comprehensive IT Asset Disposition (ITAD) solutions that prioritize environmental sustainability and data security. With a focus on protecting both client reputations and the planet, DMD serves a diverse clientele, including numerous companies and public entities. Core DMD Systems services include secure data destruction, asset decommissioning, and equipment redeployment and remarketing. These services span various IT categories, such as Data Center infrastructure, End User Computing devices, and Mobile technology. DMD maintains certifications that include NAID AAA, R2v3, ISO 9001, 14001, and 45001.
DMD Systems Recovery delivers comprehensive IT Asset Disposition (ITAD) solutions that prioritize environmental sustainability and data security. With a focus on protecting both client reputations and the planet, DMD serves a diverse clientele, including numerous companies and public entities. Core DMD Systems services include secure data destruction, asset decommissioning, and equipment redeployment and remarketing. These services span various IT categories, such as Data Center infrastructure, End User Computing devices, and Mobile technology. DMD maintains certifications that include NAID AAA, R2v3, ISO 9001, 14001, and 45001.
DMD operates three certified ITAD processing facilities in Tempe, AZ, Austin, TX, and Palo Alto, CA. Their “Reuse First™” approach prioritizes extending the lifecycle of IT assets whenever possible. The company serves a wide range of industries, including healthcare, finance, and government.
At a Glance:
- Company Type: Private
- Year Founded: 1994
- Website: https://www.dmdsystems.com/
- No. of Employees: 50+
- Headquarters Location: Tempe, Arizona,
- Reviews: As of March. 2025, has a rating of 4.5 based on 5 reviews on Gartner Peer Insights™, Trustpilot: No reviews found, Google: 3.8 of 5 based on 16 reviews
Bottom Line: DMD Systems is a good choice for West Coast organizations seeking compliant and environmentally responsible IT asset disposition solutions.
Hummingbird International, LLC
 Hummingbird International, LLC specializes in IT asset disposition (ITAD) services, focusing on secure data destruction, asset remarketing, and environmentally responsible recycling. Founded in 2010, the company offers comprehensive solutions for the collection, auditing, recycling, and safe disposal of laptops, monitors, hard drives, and other IT equipment. Hummingbird International provides customized ITAD services tailored to clients’ specific needs. Their services include free e-waste pickup for both residential and commercial clients, ensuring a hassle-free process for disposing of obsolete electronics.
Hummingbird International, LLC specializes in IT asset disposition (ITAD) services, focusing on secure data destruction, asset remarketing, and environmentally responsible recycling. Founded in 2010, the company offers comprehensive solutions for the collection, auditing, recycling, and safe disposal of laptops, monitors, hard drives, and other IT equipment. Hummingbird International provides customized ITAD services tailored to clients’ specific needs. Their services include free e-waste pickup for both residential and commercial clients, ensuring a hassle-free process for disposing of obsolete electronics.
The company adheres to NIST 800-88 standards for data destruction, utilizing software to overwrite personal data and physically shredding hard drives to eliminate any chance of data retrieval. Hummingbird International provides service to Philadelphia, New York, New Jersey, Pennsylvania, and Texas. Specific certifications are not mentioned on the Hummingbird website.
At a Glance:
- Company Type: Private
- Year Founded: 2010
- Website: https://hummingbirdinternational.net/
- No. of Employees: 2-10
- Headquarters Location: Yardley, PA
- Reviews: As of March. 2025, Hummingbird International has a rating of 5.0 based on 4 reviews on Gartner Peer Insights™, Trustpilot: No reviews found, Google: 3.4 of 5 based on 5 reviews
Bottom Line: Hummingbird may be a good choice for organizations in the New York area but make sure certifications such as R2v3 and NAID AAA are in place before proceeding.
Guardian Data Destruction
 Guardian Data Destruction partners with ITADs, MSPs, Resellers, and value-added resellers (VARs) to deliver best-in-class onsite drive shredding services. They are NAID AAA certified, NIST-compliant equipment, and have a process that can help protect customers from data breaches. Their mobile trucks serve most of the lower 48 U.S. States and have partnerships to destroy data internationally.
Guardian Data Destruction partners with ITADs, MSPs, Resellers, and value-added resellers (VARs) to deliver best-in-class onsite drive shredding services. They are NAID AAA certified, NIST-compliant equipment, and have a process that can help protect customers from data breaches. Their mobile trucks serve most of the lower 48 U.S. States and have partnerships to destroy data internationally.
In May 2024, Guardian Data Destruction announced an investment by San Francisco-based private equity firm Housatonic Partners. They also announced that Glen Laga was retiring and Rob Alston was taking his place as CEO.
At a Glance:
- Company Type: Private
- Year Founded: 2009
- Website: https://guardiandatadestruction.com/
- No. of Employees: 80
- Headquarters Location: Hackensack, NJ
- Reviews: As of May. 2025, Guardian Data Destruction does not have reviews on Gartner Peer Insights™ as they are not a ITAD vendor, Google: 4.4 of 5 based on 10 reviews
Bottom Line: Guardian is a good choice for organizations looking for on-site shredding when they already have an R2v3-certified recycling partner.


 Securis has recently upgraded our handheld scanners to Zebra TC58s, a powerful, enterprise-class handheld mobile computer designed to streamline and improve inventory management. The TC58 is fantastic at capturing barcodes, even if they are damaged or poorly printed. Powered by a robust Qualcomm Snapdragon 8-core processor, the TC58 enables faster and more efficient operation, allowing it to handle demanding applications effortlessly, ensuring a seamless and efficient scanning process.
Securis has recently upgraded our handheld scanners to Zebra TC58s, a powerful, enterprise-class handheld mobile computer designed to streamline and improve inventory management. The TC58 is fantastic at capturing barcodes, even if they are damaged or poorly printed. Powered by a robust Qualcomm Snapdragon 8-core processor, the TC58 enables faster and more efficient operation, allowing it to handle demanding applications effortlessly, ensuring a seamless and efficient scanning process.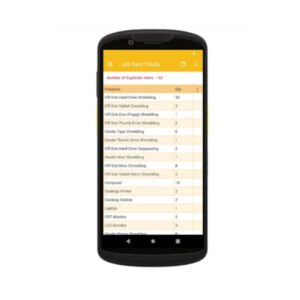 Mistakes are inevitable when scanning thousands of assets daily. Industry data suggests that scanning accuracy typically falls below 85%. A common issue is the inadvertent duplication of scanned items, leading to time-consuming investigations.
Mistakes are inevitable when scanning thousands of assets daily. Industry data suggests that scanning accuracy typically falls below 85%. A common issue is the inadvertent duplication of scanned items, leading to time-consuming investigations.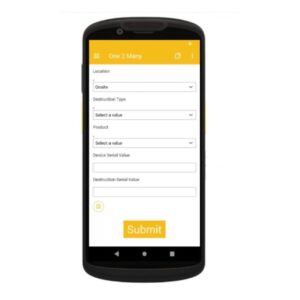 One of the most significant challenges in ITAD is ensuring that every asset is correctly matched to its corresponding storage device before being securely disposed of. Many of our clients, particularly those in the banking and financial services sectors, require assets to be matched to their storage cabinets for com
One of the most significant challenges in ITAD is ensuring that every asset is correctly matched to its corresponding storage device before being securely disposed of. Many of our clients, particularly those in the banking and financial services sectors, require assets to be matched to their storage cabinets for com



 What is Unified Endpoint Management (UEM)?
What is Unified Endpoint Management (UEM)?

 In a fast-paced digital environment, businesses must constantly upgrade their technology to remain competitive. Millions of electronic devices are discarded or replaced yearly, creating an escalating
In a fast-paced digital environment, businesses must constantly upgrade their technology to remain competitive. Millions of electronic devices are discarded or replaced yearly, creating an escalating  Ultra-secure IT recycling
Ultra-secure IT recycling Collection and Inventory
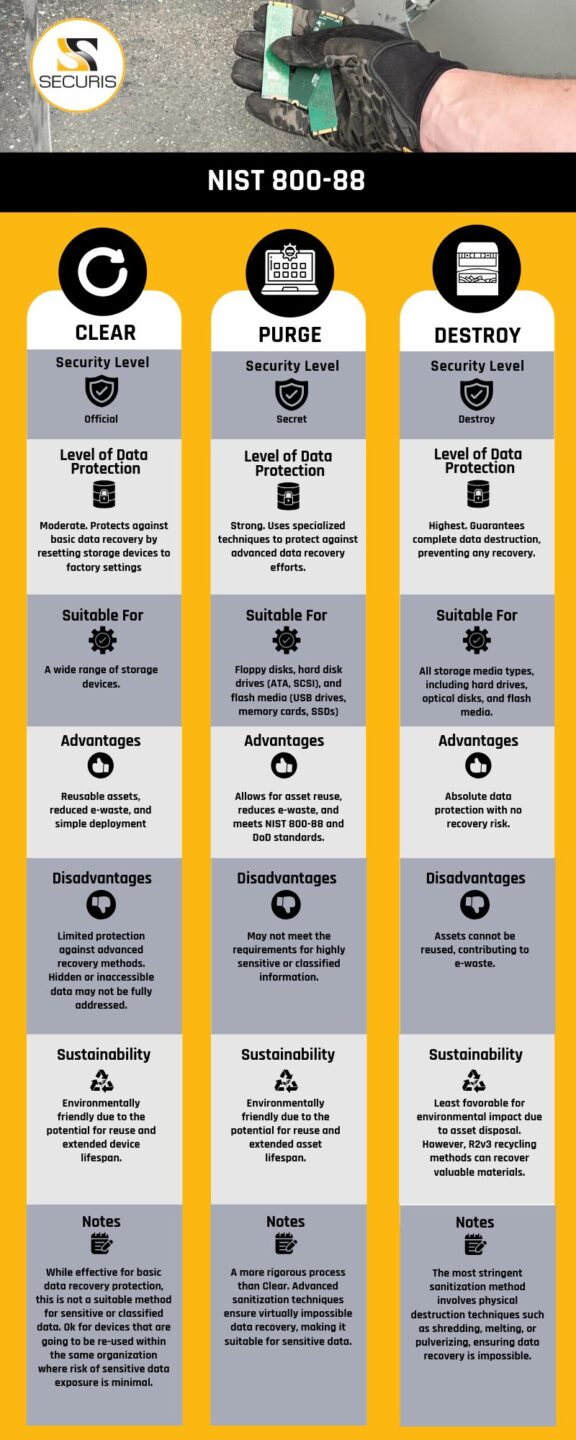
Collection and Inventory Securis’ data erasure processes meet or exceed industry standards such as
Securis’ data erasure processes meet or exceed industry standards such as  The benefits of computer and device donation extend beyond the donating company, making a significant impact on communities in need:
The benefits of computer and device donation extend beyond the donating company, making a significant impact on communities in need: As technology evolves, the need for responsible
As technology evolves, the need for responsible