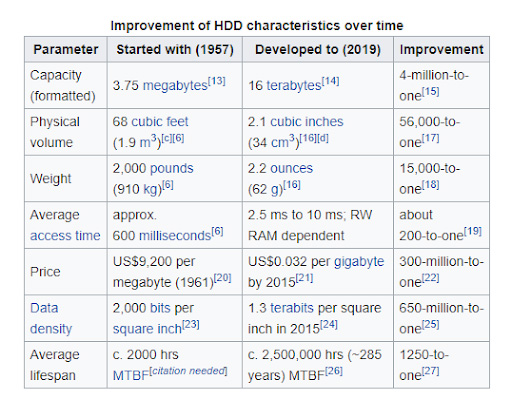
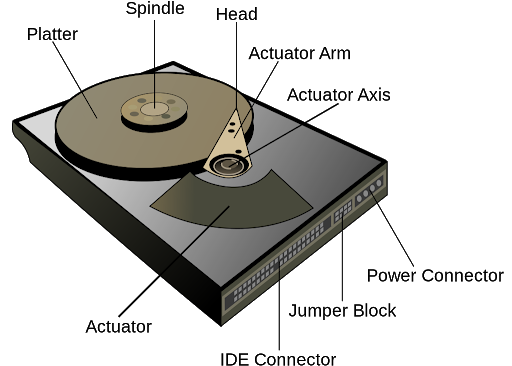
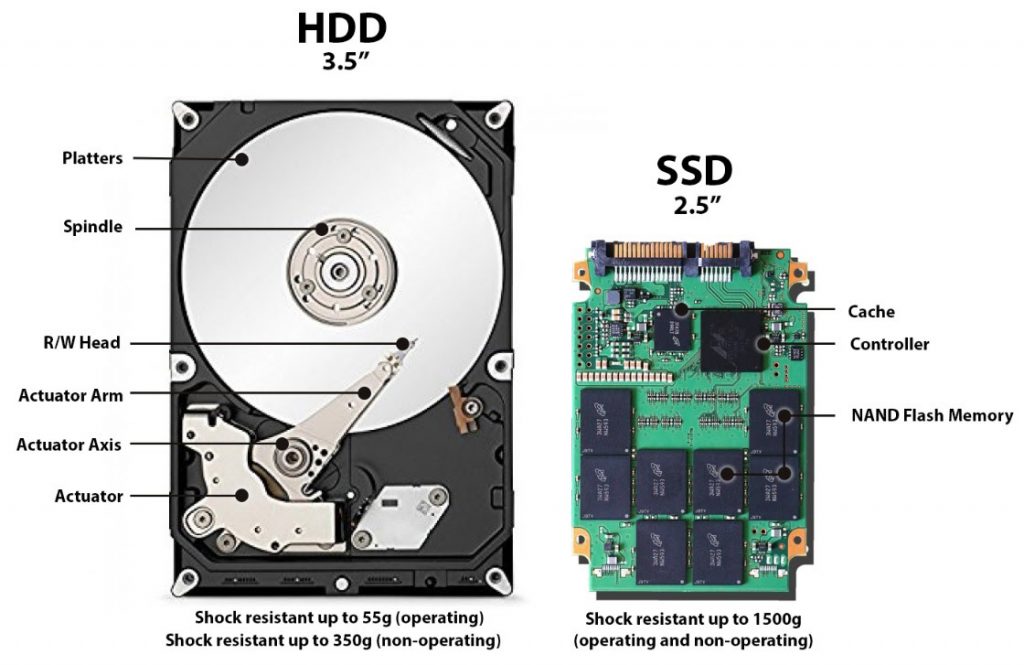
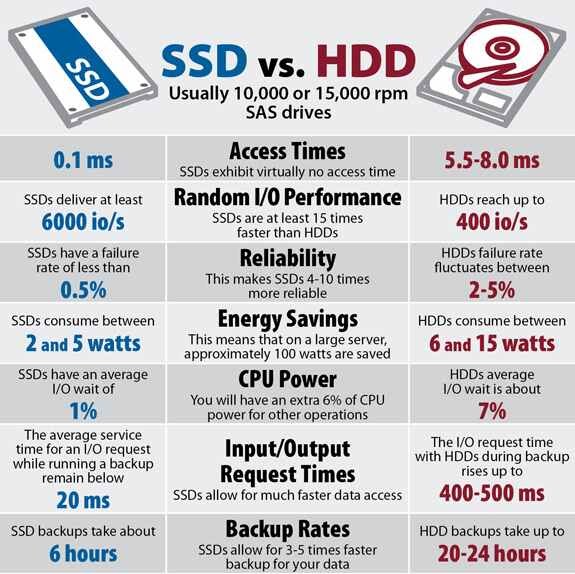
Hampton Roads is home to many of the nation’s largest Naval Bases including Norfolk Naval Base, Oceana Naval Air Station, Joint Base Little Creek, and Yorktown Naval Weapons Station. Naval Station Norfolk supports the operational readiness of the US Atlantic Fleet, providing facilities and services to enable mission accomplishment. Curious about how the U.S. Navy handles data destruction?
Securis’ Hampton Roads location protects the data on local Navy retired IT assets. In an interview with the Norfolk, Virginia business owner Allan Jenik, we explore some unique data destruction needs of the Navy.
Q: What are some observations about the unique needs of Navy customers regarding data destruction and IT recycling?
A: The Navy typically handles data destruction by using the DLA DRMO process for disposing of retired IT equipment. We’ve helped organizations such as NAVFAC dispose of heavy equipment such as copy machines and large printers that are difficult to retire and recycle properly. Documentation is extremely important to our Navy customers and we provide reporting that lists the serial numbers and manufacturer of every piece of equipment along with a certificate of recycling.
We do two types of data destruction for NAVFAC, SPAWAR, and CNIC. Both types of destruction require a representative of the Navy to witness the destruction and it is almost always done on base. Unclassified hard drives, cell phones, and tablets have their serial numbers scanned before destruction and must match a corresponding list provided by the Navy representative. We typically scan the identifying information and provide our list of serial numbers to the Navy representative to make sure they match before we begin the shredding process.
Classified hard drives and devices are handled in a similar manner as unclassified drives but must remain in the possession of an authorized Navy representative throughout the process until the storage devices are degaussed in our NSA-evaluated equipment before being shredded. Solid State hard drives, cell phones, and tablets must be shredded to a 2mm particle size to meet NSA requirements and we have equipment with that capability. Late-model cell phones and tablets need to be disassembled before microshredding to remove the batteries which we can do on-site to maintain security protocols.
Q: How do you protect the data on old IT devices for the Navy (degaussing, shredding, etc.)?Any particular regulations they have that are different from most companies?
A: If the devices contain unclassified/non-sensitive information, we take them back to our secure Norfolk facility for disassembly and hard drive removal. We have a lot of experience with large printers and copiers and can locate hard-to-access data storage devices such as SD and compact flashcards in addition to hard drives. If any unexpected storage devices are uncovered, we contact our Navy customer to determine the next course of action.
Q: How often do you work with the Navy in Hampton Roads, VA?
A: We typically work with our Navy customers on a semi-annual basis.
Q: Why did the Navy choose Securis over the competition?
A: Securis is flexible- many of our competitors will not allow Navy personnel to maintain possession of the data storage devices throughout the destruction process. We allow them to watch the process on our truck while following the proper safety procedures. The size of our company allows us to be flexible regarding process and documentation- we can adapt to any reasonable request.
Q: Anything else you’d like to mention about working with the Navy or about how the Navy handles data destruction?
A: Our Operations Director is a retired Navy Chief who is very familiar with procedures and base access/logistics.
 Special thanks to Securis’ Hampton Roads location business owner Allan Jenik for sharing the unique needs of the U.S. Navy in Norfolk, Virginia regarding their data destruction and IT recycling needs.
Special thanks to Securis’ Hampton Roads location business owner Allan Jenik for sharing the unique needs of the U.S. Navy in Norfolk, Virginia regarding their data destruction and IT recycling needs.
Facility Location:
2551 Eltham Ave, Suite G
Norfolk, VA 23513
Phone: 757-272-1166
Email: VA03@securis.com
Areas Serviced:
Cities and counties in southern Virginia including Norfolk, Virginia Beach, Hampton Roads, Hampton, Suffolk, Chesapeake, Newport News, Sussex, Smithfield and more.