Why Chain of Custody Matters in E-Waste Asset Management
Why Chain of Custody Matters in E-Waste Asset Management
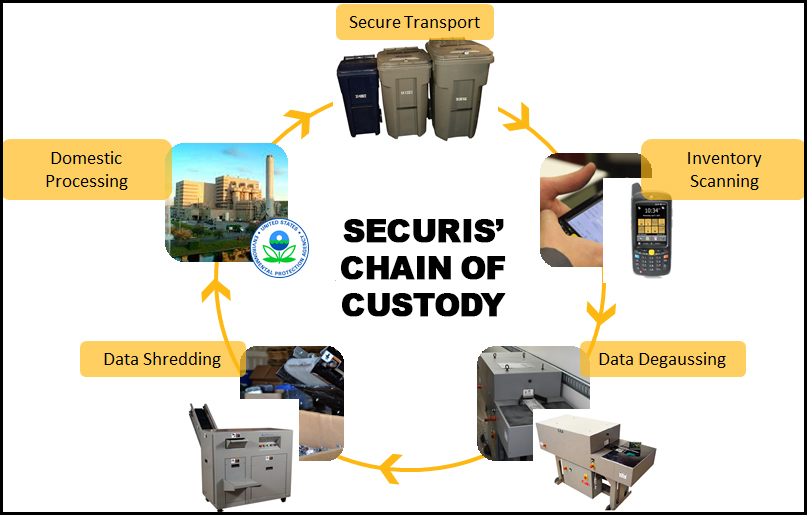
When it comes e-waste asset management, the chain of custody tracks where each asset is throughout the process. According to ITAssetManagement.net, the chain-of-custody is evidence that an ITAD vendor has physical possession of an IT asset. Suppose e-waste is found in a dump or sold on eBay with data. Chain of custody means that the vendor is accountable.
Securis understands the need for transparency for the entire lifecycle of a business’ e-waste. As a result, it has developed the leading chain of custody process for e-waste management. It ensures visibility into the disposal, destruction, and recycling of every asset included in a job.

Securis’ IT asset management chain of custody process:
- All electronics are inventoried by serial number. If there is no serial number or barcode, units are tagged with a proprietary Securis asset tag for easy identification and tracking.
- Data is destroyed in complete compliance with NSA and DOD standards, HIPAA, FACTA, Gramm-Leach-Bliley, and other compliance measures.
- Additional security protocols such as degaussing can be used.
- Corporate identifying information is removed from all electronics. Processing includes data anonymization to prevent a link between audit reports and specific destroyed hard drives.
- Materials are shredded using one of Securis’ industrial hard drive shredders. The material can be shredded down to 2mm particles.
- Securis clients receive an audit-ready IT inventory list.
- Clients are given a signed Certificate of Data Destruction. This Certificate is a nationally recognized legal document.
- Securis employees undergo extensive background checks and are U.S. citizens. Each must sign non-disclosure and confidentiality agreements. All participate in ongoing training on security procedures.
- Securis’ facilities are subject to constant monitoring and protection.
- Every Securis vehicle is equipped with the latest in GPS tracking and intrusion protection reinforcement.
Securis follows its stringent chain of custody protocols at all of its secure locations. Securis can also securely destroy assets on-site while you witness the destruction.
Related Blogs
Why a Dedicated Remote Hands Partner Outperforms In-House or On-Site Data Center Support
Posted Aug 20th,2025Partner guest blog: B-612 The Challenge of Supporting Global Infrastructure Managing physical infrastructure—whether...
Retiring Data Center Equipment
Posted Aug 1st,2025From Racks to Recycling: A Secure and Sustainable Process for Retiring Data Center Equipment At some point, every data ...
Secure Data Erasure Unlocks Value Recovery
Posted Jul 29th,2025Don’t Destroy—Wipe and Reuse: Why Secure Data Erasure Is the Smartest First Step in IT Asset Value Recovery Protect...
The Untapped Goldmine in Your Old Tech
Posted Jul 22nd,2025How Secure IT Asset Value Recovery Pays Off Every IT department has that moment: a stack of laptops being phased out,...
Navigating the M&A Minefield: Protecting Your Data in the Midst of Transformation
Posted Jul 7th,2025Mergers and acquisitions (M&A) are transformative events, offering immense opportunities for growth, market expansio...
Cybersecurity Starts with IT Asset Management
Posted Jun 24th,2025Interview with Senior Security Engineer and Cybersecurity Expert Greg Witte of Palydin About Greg Witte As a S...
What Is a Degausser and How Does It Work?
Posted Jun 16th,2025Degaussing Basics: What Is a Degausser? A degausser (also known as a demagnetizer) is a machine that disrupts and elimi...
Smart Data Center Decommissioning Strategies for a Secure, Accurate, and Sustainable Transition
Posted Jun 10th,2025Why Secure Data Center Decommissioning Matters More Than Ever Decommissioning a data center isn’t just about shutti...
Building a Circular Economy: How OEMs Are Leading the Way - An Interview with Dan Mattock, Securis
Posted Jun 2nd,2025Transcript from Video : Kurt: Good afternoon, Dan Mattock How are you? Dan: Hey good afternoon Kurt. I am...
IT Asset Disposal Gone Wrong: Compliance Nightmares for Financial Institutions
Posted May 22nd,2025No Room for Error in IT Asset Disposal for Financial Institutions When it comes to IT asset disposal (ITAD), financia...
Avoid a Million-Dollar Mistake: How to Get IT Asset Disposal Right in Healthcare
Posted May 14th,2025Why Proper IT Asset Disposal Matters in Healthcare In 2023, the Kaiser Foundation Health Plan and Hospitals paid $49 mi...
Why Choose Securis? IT Asset Disposition That IT Pros Count On
Posted May 5th,2025IT Asset Disposition Data Breach? Not on our watch. Managing end-of-life IT assets without opening the door to secu...
It’s Not Over ‘Til It’s Secure: The IT Asset Disposal Risk You Can’t Ignore
Posted May 1st,2025Upgrading your tech is exciting. The disposal of IT assets? Not so much. Most companies focus on identifying and procuri...
Top Data Center Decommissioning Companies
Posted Apr 22nd,2025Top Data Center Decommissioning Companies: Secure, Accurate, Sustainable and Compliant Decommissioning Services As en...
Hidden Data Risks: The ITAD Oversights That Put Your Business at Risk
Posted Mar 31st,2025Are You Really Destroying All Data? Most Companies Aren’t. Every company handling end-of-life IT equipment has a top ...
What is a Certificate of Data Destruction?
Posted Mar 26th,2025What Is a Certificate of Data Destruction—and Why It Matters to Your Organization A Certificate of Destruction is c...
Hardware Asset Management Challenges for Companies with Remote Employees
Posted Mar 24th,2025This is the transcript of a conversation about Hardware Asset Management between and Jeremy Boerger, the author of the P...
Transforming Lives Through Technology: Securis' IT Asset Donation in Africa
Posted Mar 11th,2025Life-Changing Opportunities Imagine a world where computers are a distant dream, medical records are scribble...
Federal Financial Institutions Examination Council (FFIEC) Data Destruction Guidelines
Posted Mar 10th,2025The Federal Financial Institutions Examination Council (FFIEC) provides guidelines to help financial institutions manage...
Request for Proposal (RFP) for IT Asset Disposition (ITAD) services
Posted Mar 3rd,2025Creating a comprehensive Request for Proposal (RFP) for IT Asset Disposition (ITAD) services is crucial for organization...
Top IT Asset Disposition (ITAD) Companies 2025
Posted Mar 1st,2025Finding the top IT Asset Disposition (ITAD) companies can be challenging. This regularly updated list has been designed ...
Advancing IT Asset Inventory Management
Posted Feb 24th,2025How Securis is Increasing Accuracy and Efficiency with Cutting-Edge Scanning Technology Inventory accuracy is a corners...
Sustainability Meets National Security
Posted Feb 19th,2025Sustainability Meets National Security-Interview Transcript Attendees Kurt Greening, EVP Securis Richard “Dick�...
How to Lower the Risk Associated with the Disposal of Organizational IT Assets
Posted Feb 4th,2025The transcript and the full video of the conversation between Kurt Greening, EVP at Securis, Greg Crabb, and Nick Crabb ...
NIST 800-88 Infographic
Posted Jan 29th,2025Organizations across various sectors use NIST Special Publication 800-88 (SP 800-88) for media sanitization guidelines d...
Using Unified Endpoint Management Tools to Maximize IT Asset Value and Increase Security
Posted Jan 23rd,2025Using UEM Automation to Prepare Computers for ITAD IT Asset lifecycle management, especially at end-of-life, can be...
Secure Data Destruction and Responsible Electronics Recycling: Protecting Data While Helping Others
Posted Jan 2nd,2025The Growing E-Waste Problem: A Call for Responsible IT Recycling In a fast-paced digital environment, businesses must c...
What are the Different Hard Drive Data Destruction Methods?
Posted Dec 19th,2024Data security has become a paramount concern for individuals and organizations in today's digital environment. As we acc...
Why Your IT Asset Disposition (ITAD) Partner Should Be NAID AAA Certified
Posted Dec 11th,2024Do You Need a NAID-AAA Certified Partner for IT asset disposition (ITAD)? According to the IBM Cost of a Data Breach ...
Should IT Departments Sell End-of-Life IT Assets on Ebay?
Posted Dec 5th,2024Corporate IT departments play a critical role in managing the entire lifecycle of a company’s technology assets, inclu...
AI-Powered Accuracy for IT Asset Tracking: Revolutionizing ITAD with Securis
Posted Dec 2nd,2024In IT Asset Disposition (ITAD), one thing is crystal clear: accuracy and efficiency are paramount. The slightest error c...
The Relevance of the Sarbanes-Oxley Act to Data Destruction
Posted Nov 25th,2024The Sarbanes-Oxley Act of 2002 (SOX), primarily known for its stringent financial reporting and corporate governance reg...
Is Your Smartphone Data Safe after a Factory Reset?
Posted Nov 14th,2024Smartphones are indispensable in our daily lives. We use them to stay connected, work remotely, navigate cities, track f...
Why choose an R2v3-certified e-waste Recycling Company for ITAD?
Posted Oct 29th,2024R2v3 is a comprehensive sustainability certification assuring the highest global electronics reuse and recycling stand...
What to Look for in a Responsible E-Waste Recycling Partner
Posted Oct 14th,2024Key Factors in Choosing a Secure and Responsible IT Asset Disposition (ITAD) Partner In today's rapidly evolving tech...
Financial Institutions Need Secure Data Destruction Policies to Comply With The Gramm-Leach-Bliley Act (GLBA)
Posted Sep 27th,2024What is the Gramm-Leach-Bliley Act? Financial Institutions must comply with information security and privacy regulati...
Balancing Data Security, Sustainability, and Disposal Costs for IT Asset Disposition (ITAD)
Posted Sep 5th,2024Finding Balance Between Information Security and Sustainability Electronic waste disposal (e-waste) has become a pres...
Federal Tech Podcast with Securis' Sal Salvetti
Posted Aug 19th,2024Moderator John Gilroy interviews Securis Director of Operations Sal Salvetti for the Federal Tech Podcast Podcast lin...
NIST 800-88: Secure Data Destruction Standards for Media Sanitization
Posted Aug 8th,2024NIST 800-88 Guidelines for Secure Data Destruction In today's data-driven world, where information is both currency a...
HITECH Compliance: Secure Medical Equipment Recycling & Data Destruction
Posted Jun 10th,2024In this article, learn: What is the HITECH Act? How do medical equipment recycling and data destruction support ...
How to Send ESG Ratings Up and Data Security Risk Down
Posted May 17th,2024Environmental, Social, and Governance (ESG) ratings are increasingly scrutinized in today's corporate landscape, leaving...
Fairfax County launches solar panel recycling program with Securis
Posted Apr 11th,2024The county’s Department of Public Works and Environmental Services launched a solar panel recycling program last wee...
Come Visit Securis at Data Center World
Posted Mar 14th,2024Join us at booth #748 at the upcoming Data Center World Event which is being held April 15-18 at the Walter E. Washingto...
How Are Magnetic Hard Drives Shredded?
Posted Mar 7th,2024Quite a few customers have asked us exactly how we shred a hard drive. To help explain this, below are the steps that a ...
What Is R2 Certification in E-Waste Recycling?
Posted Feb 29th,2024R2 certification, established by Sustainable Electronics Recycling International (SERI), is a global standard for any R2...
Why Inventory Matters in Electronics Recycling and Data Destruction Policy
Posted Jan 17th,2024In electronics recycling and data destruction, inventory reports plays a pivotal role in ensuring transparency, complian...
What is the Circular Economy
Posted Jul 14th,2023When purchasing a new computer, phone, and other electronics, most of us don’t think about where the materials needed ...
How to Recycle Batteries for IT Directors
Posted Apr 21st,2023Batteries are not only bad for the environment when we toss them in the trash, but they can be explosive. Varying types ...
Reusing Decommissioned Data Center Equipment
Posted Mar 31st,2023Data centers seem to be popping up everywhere. As they close or upgrade, it’s important to reuse as possible in the da...
Why Businesses Need R2 Certified E-Waste Recycling Companies
Posted Mar 17th,2023If your business is looking for an e-waste recycling company, knowing that not all are created equally is essential. The...
Top 10 E-Waste Recycling Misconceptions
Posted Mar 9th,2023The misconceptions around e-waste recycling can be deterring, but they aren’t the reality. If you have questions about...
What is ESG and Why is it Important?
Posted Feb 28th,2023ESG has become a buzz term in the ITAD industry- but what does it mean? ESG stands for environmental, social, and corpor...
Are We Being “Smart” or Creating More E-waste?
Posted Feb 13th,2023Our smart devices are ever-evolving, from our phones to our watches and everything in between. Many are trying to keep u...
Everything You Need To Know About Hard Drive Destruction
Posted Jan 30th,2023You may know that it’s crucial to remove information from hard drives before disposing of them- but do you know the in...
Data Privacy Day 2023
Posted Jan 27th,2023Did you know January 28th is Data Privacy Day? While the rest of the world may be celebrating, at Securis, every d...
Securis: Past, Present and Future of ITAD
Posted Jan 11th,2023It's 2023, and at Securis, we're looking forward to serving you with the best data destruction and end-of-life equipment...
Is Your Android Sharing Your Secrets?
Posted Jan 9th,2023When your phone gets old, becomes out of date, or starts to break, it’s time to decide whether to sell it or trade it ...
Securis Provides Federally Approved Data Destruction
Posted Dec 21st,2022Proper disposal for government contractors is vital for federal compliance. Different businesses and data centers may ha...
Where Can I Recycle Computers?
Posted Nov 30th,2022Technology constantly changes, which may leave you wondering, “Where can I recycle computers?” Electronics recycling...
How Can I Recycle Batteries?
Posted Nov 23rd,2022While the easiest thing to do is toss old batteries into a garbage can, proper battery disposal methods are vital. Batte...
Securis Attends DC's High Tech Prayer Breakfast
Posted Nov 22nd,2022On Thursday, November 10, 2022, Securis attended the 21st annual High Tech Prayer Breakfast. It's a unique event tha...
How to Avoid a Data Breach
Posted Oct 31st,2022When disposing of your equipment, tossing hard drives without properly removing the information they contain can cos...
Can You Make Money from End-Of-Life Electronics?
Posted Oct 29th,2022End-of-life electronics contain precious metals and elements, such as gold, silicon, platinum, and more. Your end-of-lif...
Learn from Morgan Stanley’s Data Breach: Use a Certified and Experienced ITAD Company
Posted Oct 26th,2022Have you tried to reduce costs when it’s time to get rid of old IT equipment? Morgan Stanley learned the hard way ...
What Happens to Recycled Computer Parts?
Posted Oct 21st,2022At Securis, we process, disassemble, and recycle as much e-waste as we can in-house. Recycling your computer with us...
Securis' E-Waste Recycling Statistics
Posted Oct 19th,2022In one month, we sell about 6,000 desktops If stacked on top of one another, they'd reach the top of the Empire St...
How to Protect the Chain of Custody During Data Destruction
Posted Oct 7th,2022Some businesses, governments, and other entities have a chain of custody requirement regarding data destruction. Securis...
Secure and Environmentally Safe Data Center Liquidation
Posted Sep 15th,2022The environment doesn’t usually come first in a data center operator’s priorities. While Securis recognizes the impo...
Why You Need HIPAA Compliant Data Destruction Services
Posted Jul 25th,2022In this day and age, it’s vital to keep your client’s personal information and data secure. Healthcare providers and...
Where Can I Recycle Old Computers?
Posted Jun 24th,2022Do you have old computers sitting around taking up space? As a refurbisher, re-integrator, and data destruction firm, Se...
Why Does Size Matter For SSD Shredding?
Posted Jun 16th,2022Solid State Drives (SSDs) hold massive amounts of data and can be an alternative to the traditional hard disk drive. SSD...
Working for a Company with Great Core Values
Posted May 18th,2022One of the most important aspects of hiring people to work with Securis is how potential employees fit in with the compa...
Eighth-Grader Saves End-of-Life Electronics from Landfills
Posted Apr 13th,2022When his family threw out an old microwave, eighth-grader Eric Akers figured there must be a better way to get rid of ol...
Happy St. Patrick's Day!
Posted Mar 17th,2022Although we don't have proof just yet, the Leprechaun community is really excited about green, sustainable electronics r...
Securis Doubled Its E-Waste Recycling Efforts in 2021
Posted Mar 9th,2022In 2021, Securis collected 6,015,125 pounds or just over 3,000 tons of e-waste to refurbish, reuse, or recycle. That’s...
E-Waste Recycling for the Community with WUSA9
Posted Mar 2nd,2022We were proud to participate as the e-waste recycler for WUSA9’s #RecyclingMatters events this weekend. On Saturday, F...
Best eWaste Recycling Specialist Award Given to Securis
Posted Feb 12th,2022United Kingdom, 2022 – Acquisition International Magazine has announced the 2021 Global Green Business Awards winners....
Happy Holidays from Securis
Posted Dec 20th,2021We wish you and yours a very happy holiday and a new year full of laughter, comfort, and blessings. We hope you'll enjo...
Securis at The High Tech Prayer Breakfast 2021 in Photos
Posted Nov 17th,2021Earlier this month, Securis employees and a few guests headed to the Ritz-Carlton in Tysons Corner for the High Tech Pra...
The EPA's America Recycles Day is November 15, 2021
Posted Nov 13th,2021The Environmental Protection Agency (EPA) has announced that on America Recycles Day, they will release the final versio...
How to Take Apart a Computer for Recycling in 7 Steps
Posted Oct 27th,2021It's important to properly recycle computers and other e-waste. Electronics contain harmful substances such as arsenic a...
How Businesses Should Recycle Electronics and Other Items
Posted Sep 22nd,2021Montgomery County, Maryland's Department of Environmental Protection recently held a live webinar discussing how busines...
How Securis Identifies Employees who Lead, Thrive, and Innovate
Posted Sep 2nd,2021At Securis, diversity isn’t just a buzzword. It’s a core company strength. It’s an acknowledgment that while peopl...
ITAD Company Securis Benefits from Workforce Diversity
Posted Sep 2nd,2021From the very beginning, Securis has prided itself on its commitment to diversity – not just in words, but in actions ...
Recycling Technology Assets: A Business Revenue Stream
Posted Aug 2nd,2021For businesses, when times are tough, they look for every income stream possible. When times are booming, smart business...
Destroying SSDs: Drive Type Matters
Posted Jun 11th,2021Solid State Drives (SSDs) are a vital component of the machines we rely on. SSDs are essential to the operation of deskt...
Why Choose Local Hard Drive Shredding and Electronics Recycling?
Posted May 12th,2021Securis provides local hard drive shredding, electronics recycling, and data destruction. However, at our core, we're re...
Electronics Recycling Events to Celebrate Earth Day
Posted Apr 20th,2021This year, Earth Day is April 22, and people will celebrate by participating in ways to be better stewards of the earth....
The Securis Core Value Innovation at Work during a Power Outage
Posted Apr 8th,2021Securis is a strong believer in our Core Values and this week, one was put to the test. There was a large power outage i...
Data Erasure for the Military in Hampton Roads Virginia
Posted Mar 9th,2021The Hampton Roads region of Virginia is home to Naval Station Norfolk, the largest navy base in the world. It's also hom...
5 Reasons Not to Use Best Buy Computer Recycling
Posted Mar 2nd,2021This post is NOT an attempt to bash or knock Best Buy. We like the company and think they're a good retailer. However,...
What is the NSA Recommended SSD Shredded Particle Size?
Posted Feb 23rd,2021Sometimes, a standard shredder isn’t enough. For highly sensitive information, especially on smaller devices such as s...
Data Destruction is Essential for Healthcare During COVID-19
Posted Jan 22nd,2021Since the beginning of the COVID pandemic, many health care organizations have been pushed to the brink. They're at capa...
60,000 Pounds of E-Waste Recycled in Loudoun County
Posted Dec 22nd,2020Securis recently partnered with Loudoun County, VA to run their county-wide e-waste recycling and shredding event. Despi...
Securis Hampton Roads Brings Cheer to Military Families
Posted Dec 11th,2020Securis is a company that takes its core values seriously. They are part of all that the company does – both on and of...
The Foods that Make Thanksgiving Thanksgiving
Posted Nov 25th,2020With Thanksgiving not looking the same for many families this year, we had a Securis group chat about which foods make T...
Dan Mattock Celebrates 10 Years with Securis
Posted Nov 13th,2020“I’ve really enjoyed seeing people get hired as entry level technicians or warehouse workers and advance to senior l...
Securis Recycled 20,000 Pound of E-Waste at Community Event
Posted Oct 30th,2020Securis is dedicated to its clients and to the communities that it serves. That was evident during an event in Broadland...
Securis is a Computer Recycling Leader in North Carolina
Posted Oct 13th,2020If the secret to real estate is “location, location, location,” then the secret for providing exemplary service to c...
When Should You Use A Degausser to Destroy Data on Hard Drives?
Posted Sep 22nd,2020Remember back in the 80s and 90s the care, time, and effort it took to make a mixtape? Sure, the hard work was worth it ...
Does Degaussing Work to Destroy a Solid State Drive?
Posted Aug 26th,2020Securis gets a lot of questions about how to destroy a solid-state drive, and whether degaussing works to do so. It’s ...
Recognizing the Securis Employee of the Month
Posted Jul 22nd,2020June's employee of the month award was given to Lawrence Nicholson, a Securis warehouse worker in the disassembly divisi...
Hampton Roads, VA Recycles 3,224 Pounds of IT Equipment in a Day
Posted Jul 9th,2020Securis' data destruction and electronics recycling facility in Hampton Roads, Virginia provides ongoing recycling servi...
How To Reward Employees For A Job Well Done?
Posted Jun 25th,2020Small businesses are especially affected by the global pandemic, and Securis is no exception. While employees who are ab...
Data Destruction And IT Recycling Perks For Small Businesses
Posted Jun 18th,2020As a small business, Securis understands the impact that the COVID-19 pandemic has had on small businesses all over the ...
How Securis Helps The Healthcare Industry Protect Data In Hampton Roads, VA
Posted Jun 11th,2020The healthcare industry is one of the largest and most rapidly growing industries in the world. In 2019, the United Stat...
How Does The U.S. Navy Handle Data Destruction In Hampton Roads, VA?
Posted May 27th,2020Hampton Roads is home to many of the nation's largest Naval Bases including Norfolk Naval Base, Oceana Naval Air Station...
Celebrating Hard Work With Cool Treats
Posted May 15th,2020There's no doubt that the global pandemic has forever affected the world as we've known it. People are stressed out abou...
How is a TV Recycled?
Posted Apr 21st,2020Whether you’re upgrading to a bigger flat screen or laying a defective one to rest, there comes a time when you must d...
Socially Distant E-Recycling Success During COVID
Posted Apr 16th,2020Saturday, April 11 was Securis' scheduled community e-recycling event. They take place on the second Saturday of each mo...
What Is A Hard Drive & The Difference Between HDD and SSD
Posted Mar 24th,2020Hard Drive Definition A hard drive stores all your data, where all your files and folders are physically located. A typ...
We're Here For You During Coronavirus
Posted Mar 19th,2020Over the past 20 years Securis has been in business, we've seen many ups and downs, although the reality of the coronavi...
What Is a Hard Drive Shredder?
Posted Feb 28th,2020Here’s everything you need to know about hard drive shredders. What is a hard drive shredder? TechTarget defines...
Three Reasons Companies Fail to Secure Cloud Data
Posted Jan 28th,2020Even with the major leaps made in recent years in the cloud and security industries, companies continue to make mistakes...
The State of Cybersecurity in 2020
Posted Jan 2nd,2020Just two weeks shy of the new year, the US Navy announced a ban on TikTok, the popular video sharing app. Following the ...
Happy New Year
Posted Dec 31st,2019Thank you for being a part of the Securis community. 2019 has been a great year for us. We're honored to be trusted by o...
Securis is 19 Years Old!
Posted Dec 13th,2019Securis had a birthday last month and turned 19 years old. We found ourselves reflecting on our history and goals for ...
NPMA Partnership Led to Successful Food Drive & Data Destruction
Posted Nov 22nd,2019This week, Securis was able to host the NPMA NOVA (National Property Managers Association - Northern Virginia Chapter)...
8 Common HIPAA Violations and How to Avoid Them
Posted Sep 25th,2019Professionals in the medical industry are all too familiar with HIPAA and the responsibilities it brings. Failure to fol...
Data Protection Regulations and Opportunities You Should Know
Posted Jul 22nd,2019The biggest news in data protection in the last several years was the GDPR changes in the European Union. Those privacy ...
SERI Makes Revision of R2 Certification Standard
Posted Jul 1st,2019Are you in the market looking for a good e-waste recycling partner? Or are you currently working with a partner and you ...
Top E-Waste Recycling Tips for Small Business
Posted Jun 14th,2019While it’s true that switching to digital applications has helped us reduce paper and plastic waste, the cyclical rele...
Top Five Human Errors That Impact Data Security
Posted Jun 3rd,2019Despite our security innovations, human folly continues to be the source of hacks and breaches. Just last year, vulnerab...
How to Find a Responsible E-Waste Partner
Posted May 29th,2019How many times have you upgraded your smartphone over the last 5 years? If you’re an average tech enthusiast, chances ...
Facebook Shows Why We Need to Rethink Data Security
Posted May 6th,2019We all remember the infamous Facebook data breach incident that took place last year. Almost 50 million user accounts we...
74% of Data Breaches Start With Privileged Credential Abuse
Posted Apr 13th,2019How threatened are businesses when they fail to implement and prioritize Privileged Access Management? Very threatened. ...
Humans Produce 125,000 Jumbo Jets Worth of E-Waste Every Year
Posted Mar 18th,2019According to a January, 2019 report from Davos, the world now produces 44.7 million tons of electronic waste every year....
Dell Recycles 2 Billion Pounds of E-Waste
Posted Mar 5th,2019There can be no doubt that the technological advancements of the digital age have produced a myriad of benefits. Acc...
An Inside Look at Rwanda's Battle to Eliminate E-Waste
Posted Feb 28th,2019Along with the inexorable march of technology, and the creation and consumption of new electronic devices, the world is ...
Target Gets $7.4 Million Fine for Throwing E-Waste in the Trash
Posted Feb 12th,2019According to the Alameda County District Attorney Office, between the years of 2012 and 2016, the corporate retail giant...
Top 8 Cybersecurity Predictions for 2019
Posted Dec 28th,2018Data breaches continue to increase in scope and sophistication each year. That’s because cybercriminals stop at nothin...
How Artificial Intelligence Can Improve Data Security
Posted Dec 4th,2018Digitization has brought tremendous benefits to multiple industries, including trade, banking, and healthcare, but it ha...
Being Thankful During Thanksgiving in 2018 at Securis
Posted Nov 20th,2018Happy Thanksgiving! It's Thanksgiving week here in the US, and we thought we'd share a few things we're thankful for du...
Securis Expands Training for Students with Disabilities
Posted Nov 7th,2018Securis is pleased to announce a partnership that allows us to expand job training for High School Students with disabil...
Partnering With the Community
Posted Oct 10th,2018For eight years now, Securis has proudly participated in a program with a local high school. The program provides specia...
The Rise of the Recycled Metal Market
Posted Oct 10th,2018Metal recycling has become an increasingly important factor in environmental as well as economic outcomes. After all, me...
25% of Data Breaches Are Caused by Human Error
Posted Oct 2nd,2018In an increasingly digital world, you are becoming more and more susceptible to data breaches. Most of the time, you can...
What is the Future of Electronics Recycling?
Posted Sep 11th,2018When you get rid of your old cell phone, television, or stereo, where does it end up? Electronic devices, whether they�...
Finding an E-Waste Recycling Center
Posted Sep 4th,2018Technology is evolving faster than it ever has before. Most of us have reaped its benefits which, in many ways, have mad...
Improving the Recovery of E-Waste
Posted Aug 29th,2018Now more than ever, it’s important for the world to embrace healthy recycling practices and pass stronger policies to ...
Urban Mining - Help the Environment
Posted Aug 13th,2018With billions of people owning smartphones and other electronic gadgets, it’s not surprising that e-waste is one of th...
Program Teaches Special Ed Students IT Recycling and Data Destruction
Posted Jul 24th,2018Article as seen in The Chantilly Patch: When Sergey “Lex” Schmitt, a senior at Chantilly High School, graduates i...
Apple Adds ‘Daisy’ to Its E-Waste Management Innovations
Posted Jul 9th,2018Apple is continuing its course to implement green processes in manufacturing and retail. As a symbolic move ahead of Ear...
Planned IT Obsolescence Poses an Environmental Threat
Posted Jul 2nd,2018It turns out, planned obsolescence is not only harmful to a consumer’s wallet; it’s a considerable danger to the env...
IoT Devices will Lead to More E-Waste in the Future
Posted Apr 4th,2018Smartphones, smartwatches, fitness armbands, and other Internet of Things (IoT) devices have become more common in our e...
Four Things You Need To Know About E-Waste Recycling
Posted Mar 15th,2018Electronic product life spans have become shorter. On average, consumers replace their computers every five years. Smart...
Why Millions of CRT Screens Never Get Recycled
Posted Mar 1st,2018Although CRT TV's and monitors have become a thing of the past for most consumers, there are still many stockpiles of CR...
E-Scrap Processor Caught with a FORGED R2 Certificate
Posted Feb 19th,2018The electronics recycling industry is a heavily regulated industry that requires companies to gain certifications to ens...
CES 2018: The Top 5 Weirdest Gadgets
Posted Feb 8th,2018This year's Consumer Electronics Show in Las Vegas earlier had a bit of everything – from talking toilets to cuddly ro...
Preventing Data Breaches In Your Business
Posted Jan 18th,2018Businesses today collect and store massive amounts of data about customers, employees, and competitors. This data usuall...
Is It Better to Repair or Replace Devices?
Posted Jan 3rd,2018If you take a look at the most popular devices today, you'll notice that most, if not all, of them, are very hard to rep...
Securis Giving Back and Being of Service
Posted Dec 18th,2017The holidays are a wonderful time to reflect on giving back and being of service to support our local and global communi...
What You Need to Know about HIPAA
Posted Nov 27th,2017Disposing of protected health information (PHI) isn't as simple as tossing your hard drive in the trash and calling it a...
We're Thankful for You (and pie)
Posted Nov 21st,2017Happy Thanksgiving to you and yours! While we prepare to spend time with friends and family (and consume way too much tu...
What's On Your Wrist Might Be A Security Risk
Posted Nov 7th,2017In this day and age, people and businesses alike have more security concerns to worry about than ever before. We all car...
Wiping Isn’t Enough, You Must Destroy Data to Protect Your Data
Posted Sep 20th,2017Unlike the movies from the 1980s would lead us to believe, wiping a hard drive doesn’t remove the information from it ...
Securis In the Community - JDRF One Walk
Posted May 17th,2017Daniel Mattock Securis believes in our community and the health of its citizens. Team members enjoy participating in...
4 Ways Employee Background Checks Reduce Your Risk
Posted Apr 6th,2017Does your business have $4 million it can spare if your data is lost or stolen? That’s the average total cost of a dat...
America’s Electronic Waste Problem
Posted Mar 22nd,2017Americans and their businesses wait for days, stand in long lines, and spend millions of dollars on new equipment every ...
What Is a Degausser and How Does It Work?
Posted Nov 15th,2016A degausser is a machine that disrupts and eliminates magnetic fields stored on tapes and disk media, removing data from...
Securis in the Community - Walking to Eliminate Type 1 Diabetes
Posted May 25th,2016Securis Sales VP Daniel Mattock recently participated in the JDRF Walk to Cure Diabetes. JDRF raises vital funds that...
Celebrating Earth Day with Electronics Recycling
Posted May 2nd,2016After the 1969 oil spill in Santa Barbara, a U.S. senator organized a nationwide demonstration against environmental po...
Great Video on E-Waste Not being Recycled Correctly
Posted Apr 6th,2016We came across this powerful story as another reminder of why we should care about what happens to our old electronic eq...
Why You Need to Recycle More Hardware in Today’s Cloud World
Posted Jan 27th,2016Every time we accidentally trash a file, it feels like magic when the IT staff can recover it for us in just a few momen...
60 Minutes Video on an Electronics Landfill in Guiyu
Posted Jan 19th,2016This 60 Minutes Video on an Electronics Landfill in Guiyu illustrates how the town has become a dumping place for very t...
Data Destruction Franchise Owner Featured on CBS Local
Posted Nov 19th,2015Central Maryland Securis franchise owner Hugh McLaurin has been featured on CBS Local. McLaurin shares advice for others...
Securis and 6th graders – What’s the Deal?
Posted Nov 13th,2015Securis and 6th graders – What’s the deal? A group of enthusiastic 6th graders recently visited the Chantilly VA l...
Why Recycle Electronics?
Posted Apr 15th,2015A large part of the Securis mission is our commitment to proper IT recycling and ensuring that our customer’s retired ...
Data Destruction & E-Recycling in New Jersey
Posted Apr 9th,2015For years, IT asset disposal has been considered a logistical and operational challenge. However, due to the explosion...
Securis is Giving Back To The Community
Posted Nov 10th,2014Securis is a big believer in giving back to the community and regularly participates in fundraisers and public events. ...
Featured on Technical.ly Baltimore
Posted Aug 27th,2014Securis franchise owners George Parks and Daniel Dodd, who own and operate the data destruction and electronics recycli...
MD Franchise Owner's ALS Ice Bucket Challenge
Posted Aug 25th,2014Thursday, August 21, we participated in the ALS Ice Bucket Challenge. That day, we were pleased to see that this inc...
Securis and the ALS Ice Bucket Challenge
Posted Aug 21st,2014Over the past few weeks, you've likely seen colleagues, friends, and celebrities dump a bucket of ice water over th...
Bloomberg BusinessWeek: "The Complex Business of Recycling E-Waste."
Posted Apr 3rd,2014From BloombergBusinessWeek's CEO Tech Guide to Sustainable Business Practices comes this very informative article on, "T...
Asset disposal process for solid state drives
Posted Sep 25th,2013We ran across a compelling article on Inside Analysis called, "Is Spinning Disk About to Die?" which argues we may be at...
Securis in the Community: The JDRF Walk to Cure Diabetes
Posted May 21st,2013Along with a half-million others nationwide, Securis team members participated in the JDRF Walk to Cure Diabetes this pa...
Micro-Shredding Solution for Solid State Drives
Posted Feb 27th,2013NEW! Securis announces "micro-shredding" process exclusively for Solid State Drives (SSDs), flash drives, SD cards, ...
Destroying Solid State Drives-- Size Does Matter
Posted Oct 29th,2012Companies that are storing and utilizing massive amounts of data are finding solid-state drives (SSDs) enticing as an al...
Electronics Recycling FAQs
Posted Apr 6th,2012Why Should I Recycle? Most electronic consumers in the United States do not realize the impact of e-waste on the local ...
Giving Back to Our Community
Posted Dec 14th,2011'Tis the season for giving and Securis would like to take a moment to recognize one of our partners. For the past seven ...